
There are new variants of Bagle circulating actively at the moment: Email-Worm.Win32.Bagle.ax and Email-Worm.Win32.Bagle.ay. When the worms search the victim machines for email addresses to send themselves to, they won’t send emails to addresses containing the following text:
|
|
|
By doing this, the new Bagles are hiding from antivirus companies. This explains the relatively small number of samples that we’ve received so far.
Here’s a sample of what a Bagle.ay message looks like:
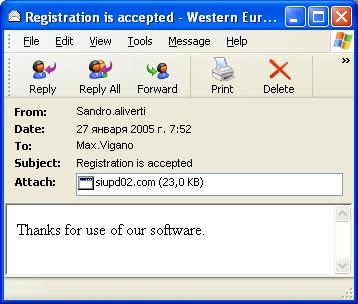
Full description of the new Bagles will be available in the Virus Encyclopedia in the near future.
Update If the infected attachment has a .cpl extension, it will be detected as Email-Worm.Win32.Bagle.at.






















Email-Worm.Win32.Bagle.ax and Bagle.ay