
Some months ago my colleague Roel Schouwenberg wrote a blog post about a money mule recruitment campaign through Facebook. We’ve been monitoring this activity and found new, quite active and successful campaigns of the same recruitment purpose and in the same social network but with a bit different approach: creating groups to follow.
An example of one of such groups:
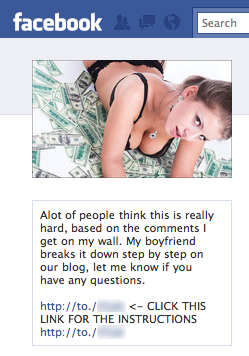
The criminals promise that= their potential mules will get more than $ 6,000 USD per month and will only need to work no more than
18 hours a week. The mule site has a GeoIP javascript, which customizes some parts of the offer according to your current geographical
location. So, it’s another old, but in some cases, effective trick to lure more potential mules.

I was surprised to see how many followers this money mule group had:
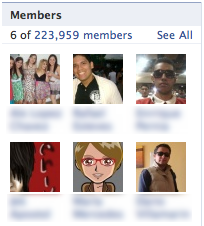
We’re talking about 224 thousand people! Who knows how many of them accepted the offer to be a money mule?= When I checked
the list of members of the group I even found some people I had met personally in my life.
It’s always important to remember that the criminals behind online money stealing are in a better (safer) position than their
mules. They also get the biggest part of the money. And what about mules…? The mules, instead of money, get to go to jail. If someday you receive an invitation by email, IM or some social network to be a part of such business, don’t let to be fooled by the criminals; odds are you’ll get prison time, not free money.





















Easy money, social networks and prison as the reward