
This week I was invited to speak at the Fifth Congress on Cybercrime, an event promoted by the São Paulo State Federation of Commerce (FECOMERCIO). There were more than 1500 participants, including journalists, politicians, lawyers, security professionals, police and businessman, all of them discussing the effects of cybercrime in the country and how society is trying to tackle it.
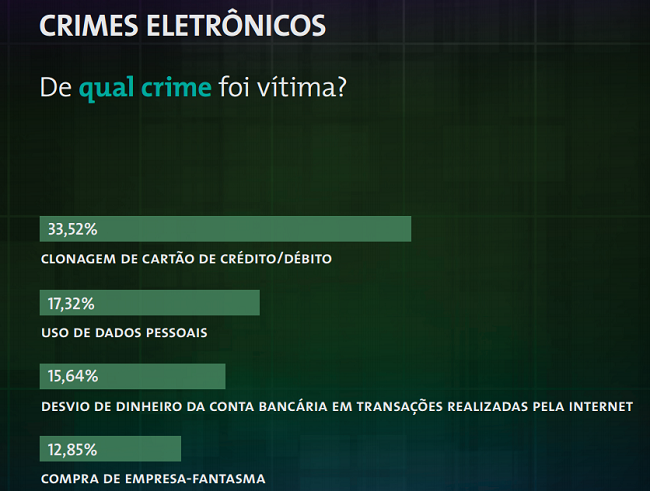
Some very thorough research was unveiled during the Congress, which showed how Brazilians are affected by cybercrime, data leakage, privacy concerns and mobile usage. To see the complete research, download a summary here or the complete data here (Portuguese). According to this study, the most common cybercrimes reported by the respondents were:
1) Credit card cloning
2) Malicious use of personal data
3) Theft of money from Internet banking services
4) Making purchases on fake e-commerce sites
The Congress discussed the latest cybercrime legislation, the recently approved “Carolina Dieckmann law”, and its effect on society. Lawyers and experts alike concluded that the law does not go far enough – the sentences are too lenient to deter the criminals.
Two more projects are awaiting approval. Brazil’s Government is considering two high-priority pieces of legislation which may change the cybercrime situation in the country: one is a law on personal data protection which aims to regulate how companies manage the data of Brazilian citizens; a second is the“Internet Constitution”, which would regulate the neutrality of the Internet and oblige IT companies to host their servers and user data locally.
I presented an overview of Brazilian malware and botnets, detailing recent attacks such as the DSL modem vulnerabilities, the latest techniques used by the crooks and the current trends among Brazilian Trojan bankers.
At the end of the event the audience had reached a consensus: any successful battle against cybercrime will require a joint effort from government, industries, commerce, and security companies.























Discussing cybercrime laws in Sao Paulo