
The Democratic Party of Hong Kong’s website was compromised and malware uploaded to the web server. Interestingly, the server was distributing malicious flash and spyware nearly identical to the compromised UK Amnesty International servers at the beginning of this month. The server is being cleaned up.
The english version of the website did not include injected iframe links pointing to the exploit.html page, which in turn delivers three different version-appropriate malicious variants of flash detected by Kaspersky as “Exploit.SWF.CVE-2011-0611”. The malicious flash was 0day at the beginning of this month, and will be effective on unpatched systems.
While it’s interesting that the security team researching the previous incident thought that the technique for delivering the payload to the hard drive is deserving a new term “drive-by caching”, it’s also incorrect to think that security products are given a higher bar to hurdle in preventing the attack because of the minor tweak – Kaspersky’s detection and prevention for the 0day flash files was released weeks before the Adobe patches. In other words, the attacks are being stopped just the same by Kaspersky products.
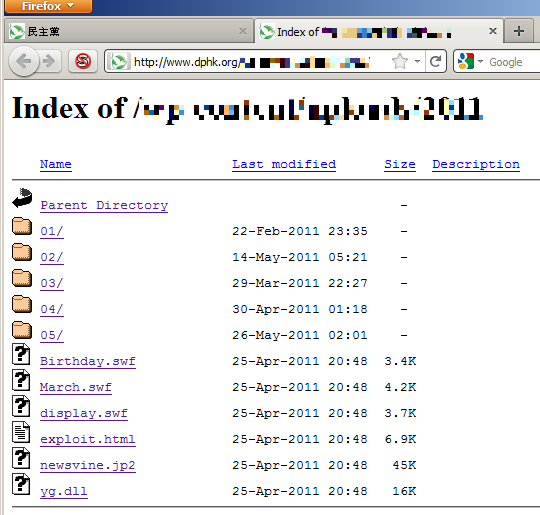
If one of the malicious flash is successful in downloading and executing the newsvine.jp2 file hosted on the server, it immediately drops a couple of files, pe.dll and srvlic.dll. These files are loaded and the delphi component decrypts its more sensitive information in-memory and phones collected information off of the system to loveusa.dyndns-blog.com. The drop server is not active at this point.
Because so many individuals run vulnerable versions of Adobe Flash and infrequently update their software, and because CVE-2011-0611 was just patched this month, the attackers had a pretty good chance of hitting their targets. Political groups continue to be an active target of cyberattacks this year.
UPDATE: we had a few final links to clean up from the standard suckerfish.js script on the server’s home page. These same malicious links leading to a 3rd party server at thesaj(dot)com hosting malicious flash, detected by Kaspersky as Exploit.SWF.CVE-2011-0611.u and Exploit.SWF.CVE-2011-0611.v, were injected and cleaned from “The Taiwan Brain Trust” web site a couple of weeks ago. The “Trust” is a group in Taiwan that “…provides policy analysis and recommendations to decision-makers in government, multinational corporations, private enterprises and civil society”, making it another compromised high value political target.






















Democratic Party of Hong Kong Website Compromised and Serving Spyware