
CVE-2014-0546 used in targeted attacks.
Today Adobe released the security bulletin APSB14-19, crediting Kaspersky Lab for reporting CVE-2014-0546.
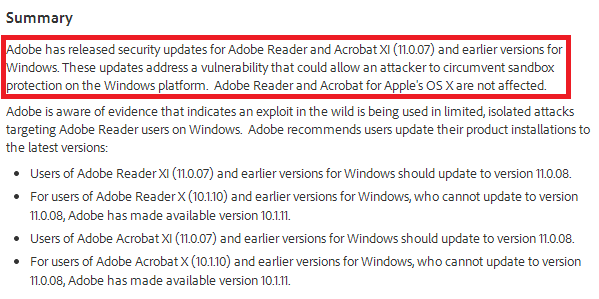
This out of band patch fixes a rather creative sandbox escape technique that we observed in a very limited number of targeted attacks.
At the moment, we are not providing any details on these attacks as the investigation is still ongoing. Although these attacks are very rare, just to stay on the safe side we recommend everyone to get the update from the Adobe site as soon as possible.
You can grab the Adobe Reader updates here.
CVE-2014-0546 used in targeted attacks – Adobe Reader Update




















Lars Groh
I’m afraid I don’t quite get the “out of band” part – after all it’s Adobe Patch Tuesday.
Confused,
Lars
Costin Raiu
This was indeed an out-of-band update. Updates for Reader and Acrobat (!) are shipped quarterly (the next regularly scheduled update is September). Adobe felt this was an important issue and decided to issue an out-of-band patch.
Thanks,
C
Amy Smith
I recently purchased a new laptop that didn’t come with Adobe Reader. The first time I downloaded it I got some kind of virus that was attached to my browser and changed all my browser (at the time Mozilla Firefox) settings, changed my search engine to something I’d never heard of. It took me a while to figure out what happened and figure out how to correct it but Kaspersky didn’t prevent it from happening or warn me that it had happened.
I waited about 6 weeks before attempting to download Adobe Reader again, and with that download ended up with a Trojan virus. Kaspersky caught it immediately, cleaned it up, quarantined it, etc. an I deleted Adobe from my computer. I downloaded it again the next day and the very same thing happened. I’m pretty sure the most recent, patched, free version is what I downloaded from Adobe’s site. So whatever the problem is – it’s not fixed. if it’s known that this is happening perhaps Adobe should stop allowing people to download the free version until the problem is fixed. That’s an entire day of wasted productivity when you have to stop everything you’re doing and clean up that mess.
Lars Groh
Got it – thanks for clarification.
L.
David
Can it be indicated whether this exploit is effective with JavaScript and all other active content features disabled?
Does EMET 5.0 mitigate it?
David
Also, independent of EMET and disabled-JavaScript, does AcroRdr32 version 11 “protected mode” mitigate this attack? Though XP is no longer supported, does the lack of ASLR and often DEP on that platform allow exploitation of AcroRdr32 in protected-mode?
manish sardiwal
Thanks for clarification.
If you can provide md5 for the same.
Thank you.
Pam
what abou t Adobe Flash player and active x and Air – do they need updating to a certain level. I have been having problems with adware which is supposed to be the ‘legal’ type. Kaspersky is sorting it when I run a scan but yesterday I had 16 hits.