

The HITB (Hack In The Box) SecConf2013 was held from 14-17 October 2013 in Kuala Lumpur, Malaysia. On 14-15, they provided us with hands-on technical training about exploits, web hacking, penetration testing and building a secure web/mobile app. On 16-17, we had a conference with three tracks; Commsec village, Hackweekday and Capture The Flag Weapons of Mass Destruction: War of the World (referred to as “CTF WMD:WotW”).

I would like to introduce “CTF WMD:WotW”. In this game, each team represented a country. Each team was provided the same server with daemons. One of them was a daemon that generated HP (main score of this game) for playing countries. The country with the highest HP country would be the winner. Other daemons generated and added extra cash for the playing countries. The cash was used to purchase shields and to repair any damaged daemons. Teams were required to “attack” rival teams, as well as to protect their own daemons. A special (strong) weapon called “Nukes” was unlocked if they successfully solved bonus challenges.
To protect/attack daemons, they were required to analyze daemons to identify a vulnerability. Let’s take a look at one daemon as an example. The daemon was designed to receive 1024 bytes maximum, but actually it could receive 1040 bytes. So, the last 16 bytes could be used to overwrite memory:
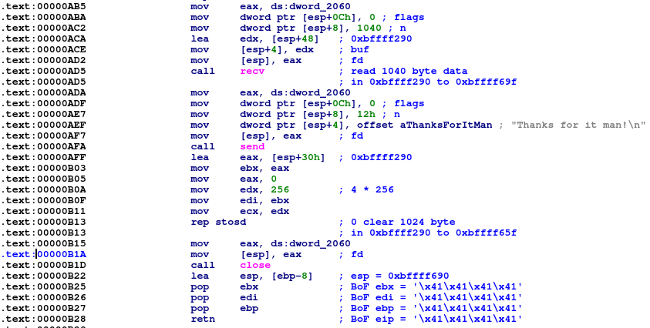
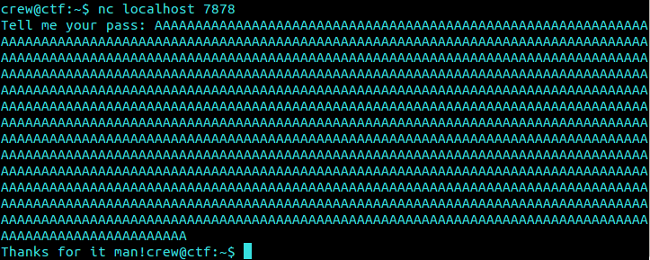
Below is the test data (“A”(x41) * 1040 byte) sent to the daemon to check the vulnerability:
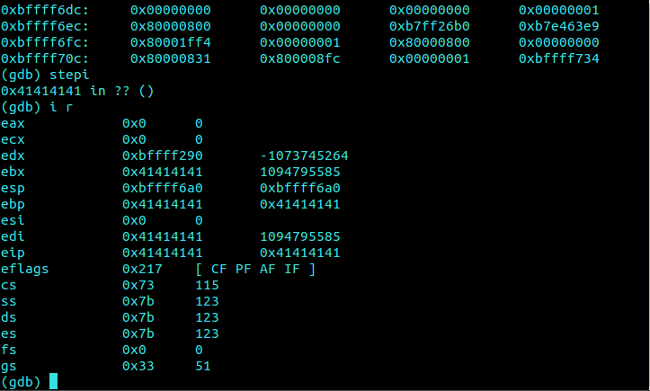
The data overwrites EBX, EBP, EDI and EIP with “x41x41x41x41” in GDB.
Creating a security patch for the daemon seems to be not so difficult. On the other hand, it looks much more difficult to create an exploit for this vulnerability – because it would need more of a trick than overwriting only the 16 bytes.
This game also had bonus challenges and a team could unlock Nukes by solving the challenges. Nukes were capable of completely destroying a rival team’s daemon.
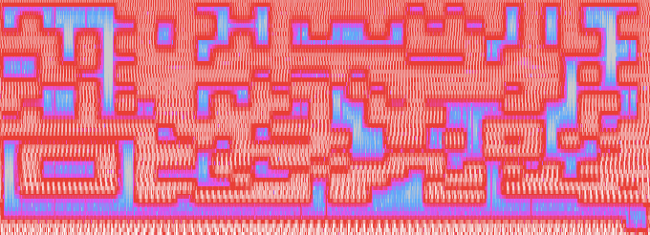
In one of the bonus challenges, wave files were supplied. The above picture was derived from the analysis of a wave file. It looks like a part of QR code, doesn’t it?
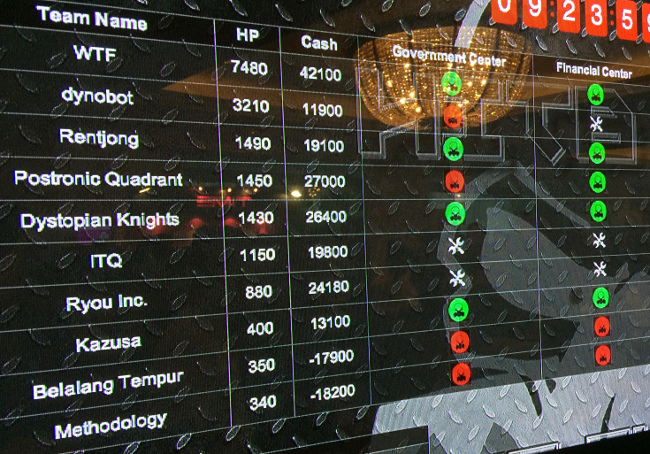
The top teams successfully unlocked some Nukes from the bonus challenges and squared off against each other. At the final phase of the game, they started to use Nukes against their rivals. Use of Nukes affected the final results a lot.
Finally, the winner was “WTF” with the significant result of 7480HP, and 2nd was “dynobot” with 3210HP.
If you think it is interesting, please join up for the next conference and play CTF!




















CTF WMD: WAR OF THE WORLD in HITB2013 Kuala Lumpur