
We recently reported about SambaCry, a new family of Linux Trojans exploiting a vulnerability in the Samba protocol. A week later, Kaspersky Lab analysts managed to detect a malicious program for Windows that was apparently created by the same group responsible for SambaCry. It was the common C&C server that both programs used – cl.ezreal.space:20480 – that suggested a relationship between them.
Kaspersky Lab products detect the new malicious program as Backdoor.Win32.CowerSnail. MD5: 5460AC43725997798BAB3EB6474D391F
CowerSnail was compiled using Qt and linked with various libraries. This framework provides benefits such as cross-platform capability and transferability of the source code between different operating systems. This, however, has an effect on the resulting file size: the user code ends up as a small proportion of a large 3 MB file.
First stage
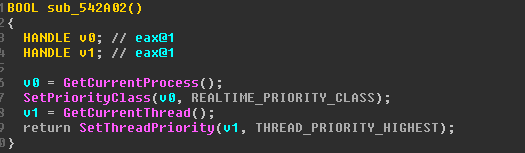
First of all, CowerSnail escalates the process priority and the current thread’s priority.
Then it uses the StartServiceCtrlDispatcher API to launch the main C&C communication thread as a control manager service.
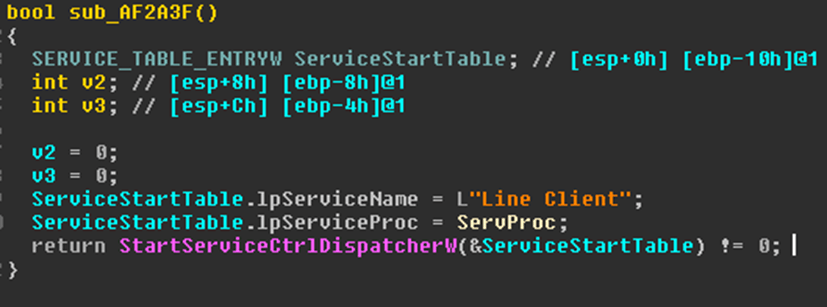
If the thread is successfully launched as a service, further communication with the C&C is carried out through that service; otherwise, CowerSnail operates without it. CowerSnail can also accept various variables as input, such as the C&C host. When these are absent, the required data is extracted from the file itself.
Invoking the main C&C communication method will look like this in the control service routine (the method is stated as ‘route’).
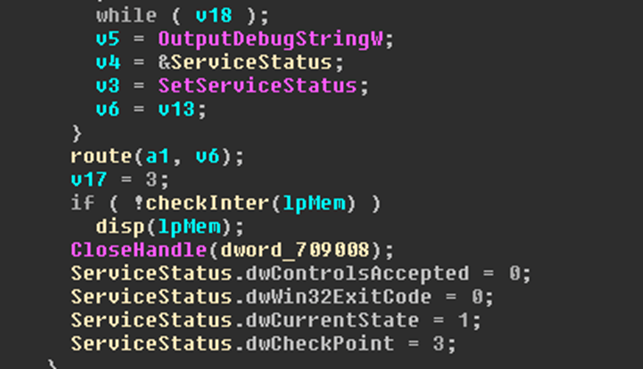
C&C server communication
Traffic analysis shows that the bot communicates with the C&C via the IRC protocol. This can be seen from the characteristic ‘CHANNEL’ command and the subsequent exchange of pings, which often occurs in IRC botnets made up of IoT devices.
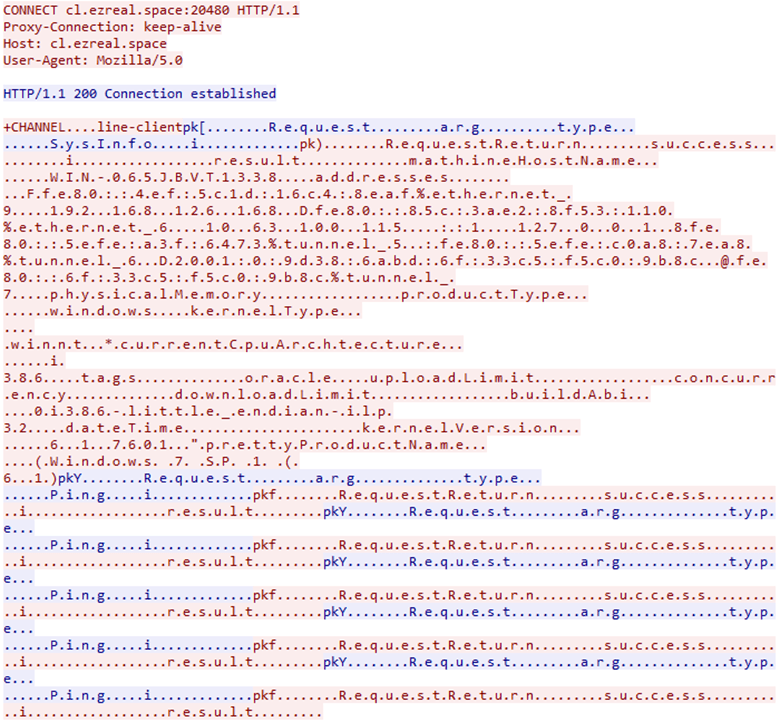
The first two bytes are the ‘pk’ signature which occurs in each packet except the CHANNEL command. The DWORD that follows is the size of the remaining part of the packet:
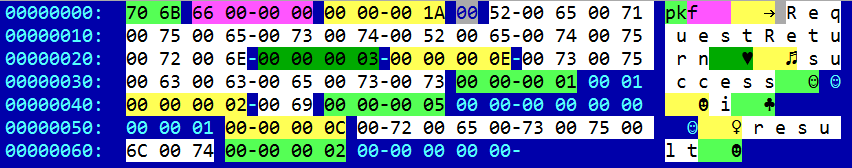
The name of each field is encoded in Unicode and is preceded by field length. The RequestReturn/Request DWORD coming after the status bar shows the number of variables for the variable RequestReturn. In this example, there are three variables: ‘success’, ‘I’ and ‘result’. Each of these fields, in turn, can contain more nested variables. The screenshot below shows the response to the SysInfo request in which CowerSnail sends 14 (0xE) different strings containing information about the infected system. The type of variable is stated after its name, followed by its value.

The structures of the request packet and the response packet are slightly different. The server’s request includes the request name coded as Request->arg->type->”Ping/SysInfo/Install”, as well as extra parameters that are nested into the arg field.
Here are examples of several variable types:
0x00000005 – Integer variable
0x0000000A – String variable
After registering the infected host at the C&C server, which includes sending information about the infected system, CowerSnail exchanges pings with the server and waits for commands.
Commands
Unlike SambaCry, CowerSnail does not download cryptocurrency mining software by default, but instead provides a standard set of backdoor functions:
- Receive update (LocalUpdate)
- Execute any command (BatchCommand)
- Install CowerSnail as a service, using the Service Control Manager command line interface (Install)
- Uninstall CowerSnail from service list (Uninstall)
- Collect system information:
Conclusion
SambaCry was designed for *nix-based systems. CowerSnail, meanwhile, was written using Qt, which most probably means the author didn’t want to go into the details of WinAPI, and preferred to transfer the *nix code “as is”. This fact, along with the same C&C being used by both programs, strongly suggests that CowerSnail was created by the same group that created SambaCry. After creating two separate Trojans, each designed for a specific platform and each with its own peculiarities, it is highly probable that this group will produce more malware in the future.























CowerSnail, from the creators of SambaCry