
This is the topic that cybercriminals are speculating about and using as a hook to infect victims. The campaign stems from malicious emails that are sent in bulk to victims:
The links mentioned in the email re-direct users to a legitimate Russian website called “Znakvoprosa” (translation: “interrogation sign”) that has been hacked in several occasions and even reported in Zone-h as such.
When the victim clicks on one of the links in the email, he/she is first re-directed to the website Znakvoprosa.tv and from there, he/she is automatically re-directed to the website Porkafadonta.com (translation: “from spankings to Fondot”) located in Bulgaria and which uses the following ColoCrossing provider as its ASN:
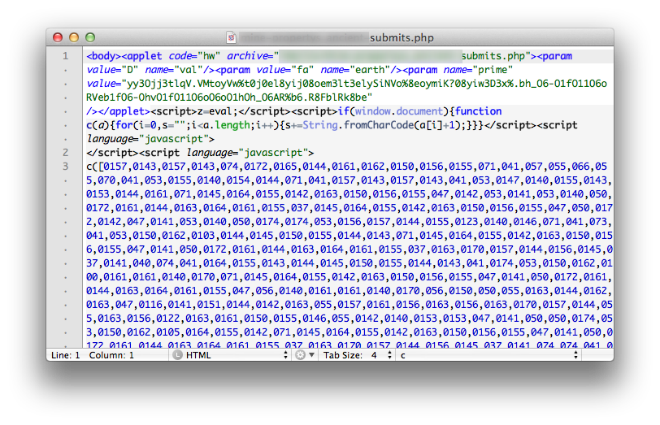
The latter contains a heavy obfuscated JS that after meeting the necessary parameters of the victim’s operating system executes the corresponding exploit. Following is a section of the mentioned script:
The launched exploit takes advantage of the CVE-2012-0507 vulnerability. Its current detection in VirusTotal is 8 out of 46 antivirus. Kaspersky proactively detects the exploit with the verdict HEUR:Exploit.Java.CVE-2012-0507.gen
Said malicious campaign is apparently based on the exploit kit BlackHole v2.0 and it is still active.
Follow me on twitter: @dimitribest

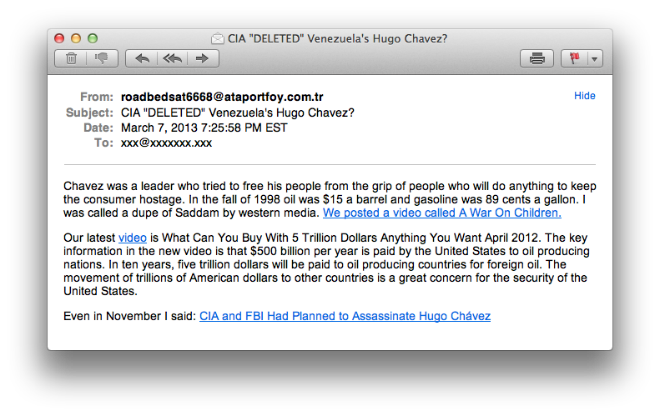





















CIA “DELETED” Venezuela’s Hugo Chavez?