
What do you see here?
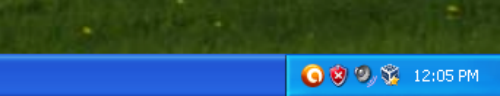
A free AV product protecting a Windows XP machine, right?
No, actually its malware a Brazilian Trojan banker coming via email and then using a masquerade to stay in the system. The malware is 386Kb only, written in Delphi, and comes via an email together with a bunch of many other malicious and non-malicious files.
If the victim clicks on the system tray icon, he will get this message:
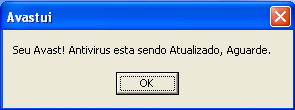
(Translation: Your Avast! Antivirus is
being updated, wait.)
In some combinations it also shows messages like this one:
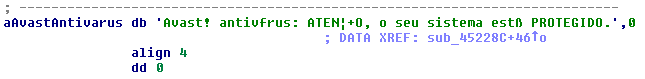
(Translation: Avast! antivirus: Attention, your system is protected)
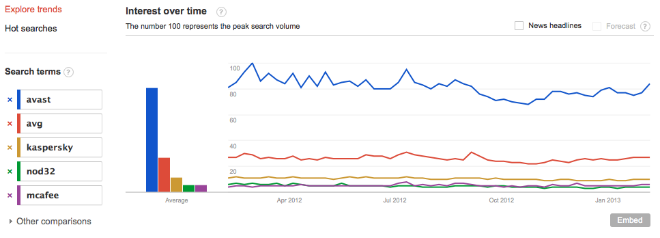
Why do cybercriminals use such a method to hide their malware in the system? Google trends shows that Avast is the most popular AV in
Brazil. And my experience of life in Latin America shows that people still dont want to pay when there is something free.
Before dropping the mentioned fake Avast product, another module, based on the anti-rootkit product Avenger, tries to remove the
following legitimate AV products from the system if they are installed: AVG, McAfee, Panda, Nod32, Kaspersky, Bitdefender, Norton, Microsoft Security Essentials, PSafe, Avira and Avast.
There are many malicious files used in the same campaign. They have different roles and are detected by Kaspersky Anti-virus as Trojan.Win32.Delf.ddir, Trojan.Win32.ChePro.aov, Trojan.Win32.ChePro.anv, Trojan-Banker.Win32.Delf.apg, not-a-virus:RiskTool.Win32.Deleter.i, Trojan-Banker.Win32.Agent.jst and Trojan.Win32.Delf.ddiq
Looks like cybercriminals from Brazil think this way: “Why to fight AV detections? Sometimes it’s too complicated. Let’s just
better replace them with our own fake solutions and everybody gets happy“.
Last, but not least, in addition to malware related to the mentioned campaign, we see more and more Trojan Bankers from Brazil coming
with fake descriptions, pretending to be modules of different AV products. Heres one example:

Follow me on twitter @dimitribest





















Brazilian Masquerade