
Some time ago I wrote an article about how Brazilian banker Trojans work but time is running out and Brazilian coders are trying to improve their skills, making more complex methods of infection. The proof of this is the sample I worked on today. The infection scheme is the classic one:
executing of the initial Trojan.Downloader —-> Downloading and
installation of Trojan.Bankers
A new (for Brazil) concept takes place between second and third stages when the Trojan.Downloader downloads and installs the Banker. On the one hand Brazilian coders obfuscate the download links using several techniques and on the other hand now they also crypt the Banker to be downloaded to the system.
For example, if you deobfuscate the malicious links and try to download the Trojans behind them you will see something like this:
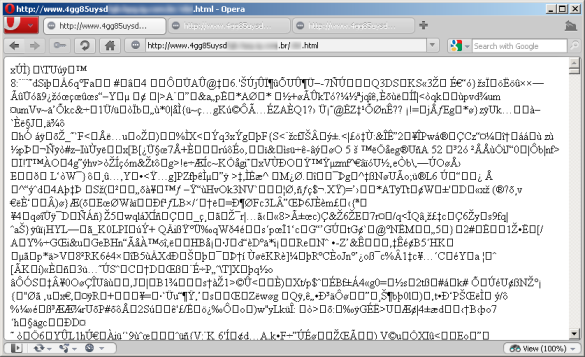
It’s a crypted (specially packed) PE file. The coders from Brazil use this technique to prevent an automated malware analysis and monitoring mode by AV companies. This sample downloaded as it is on the server won’t be functional on the user machine unless
it’s decrypted. The decryption mechanism in this case is included into the initial Trojan.Downloader, which first downloads malware, and then decrypts it to be able to infect the user machine:
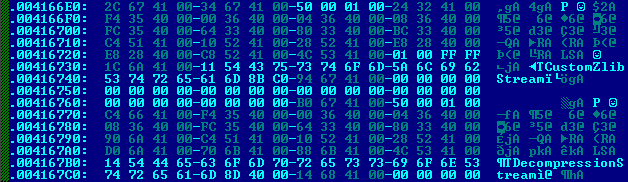
Now spot the difference: It’s the same file but after decryption looks like a standard malicious PE file and can be used to infect the victim:
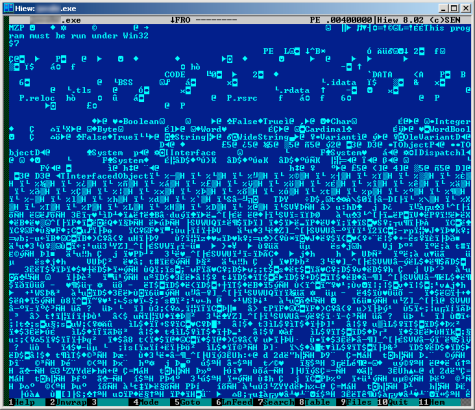
This particular sample is detected by Kaspersky Anti-Virus as Trojan-Banker.Win32.Banker.aumz and it attacks customers of the 3 most largest banks of Brazil.





















Brazil: new crypto challenge