
While many are still in shock after the Boston Marathon bombings on 16 April, it didn’t take long for cyber criminals to abuse that tragic incident for their dirty deeds.
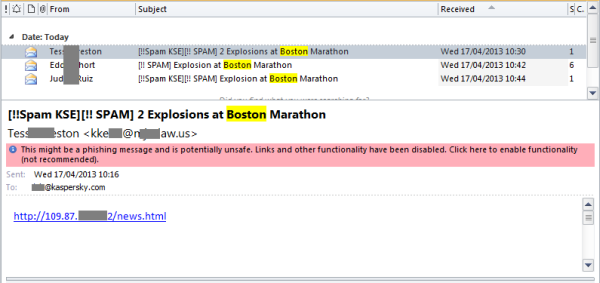
Today we already started receiving emails containing links to malicious locations with names like “news.html”. These pages contain URLs of non-malicious youtube clips covering the recent event. After a delay of 60 seconds, another link leading to an executable file is activated.
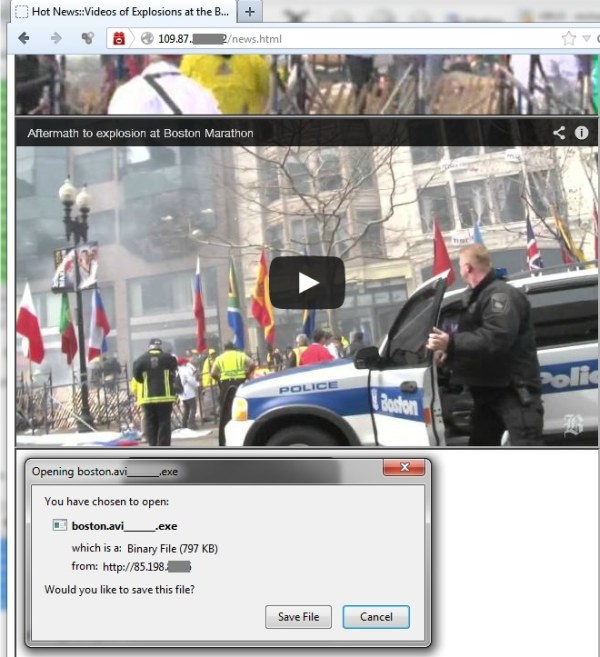
The malware, once running on an infected machine, tries to connect to several IP addresses in Ukraine, Argentina and Taiwan.
Kaspersky Lab detects this threat as “Trojan-PSW.Win32.Tepfer.*”.
MD5sums of some of the collected samples:
5EA646FFDC1E9BC7759FDFC926DE7660
959E2DCAD471C86B4FDCF824A6A502DC





















Boston Aftermath