
While working on the IT Threat Evolution report for Q3 2015, we discovered that Australia had become the leading country in terms of number of users attacked by mobile banker Trojans. We decided to find out what was behind this jump in activity and managed to identify the cause: Trojan-Banker.AndroidOS.Acecard. This family accounted for almost all the banker Trojan attacks in Australia.
After analyzing all the known malware modifications in this family, we established that they attack a large number of different applications. In particular, the targets include nine official social media apps that the Trojan attacks in order to steal passwords. Two other apps are targeted by the Trojan for their credit card details. But most interestingly, the list includes nearly 50 financial apps (client software for leading global payment systems and banks) and services, and the various modifications of Acecard make use of all the tools at their disposal to attack them – from stealing bank text messages to overlaying official app windows with phishing messages.
Here is another interesting fact that we established while investigating the Trojan: the modifications of Acecard were written by the same cybercriminals who earlier created Backdoor.AndroidOS.Torec.a, the first TOR Trojan for Android, as well as Trojan-Ransom.AndroidOS.Pletor.a, the first encryptor for mobile devices. All three Trojans run on Android.
How it all started
Given Acecard’s growing popularity and the rich criminal past of its creators, we decided to delve deeper into the history of this malware family.
It all started with Backdoor.AndroidOS.Torec.a. The first version of this malicious program was detected in February 2014 and could perform the following commands from the C&C server:
- #intercept_sms_start – start intercepting incoming SMSs;
- #intercept_sms_stop – stop intercepting incoming SMSs;
- #ussd – create a USSD request;
- #listen_sms_start – start stealing incoming SMSs;
- #listen_sms_stop – stop stealing incoming SMSs;
- #check – send information about the phone (phone number, country of residence, IMEI, model, OS version) to C&C;
- #grab_apps – send a list of applications installed on the mobile device to the C&C;
- #send_sms – send an SMS to numbers specified in the command;
- #control_number – change the phone’s control number.
Then, in April 2014, a new version emerged with more capabilities. The additional commands were:
- #check_gps – send the device’s coordinates to the C&C;
- #block_numbers – add numbers to the SMS interception list;
- #unblock_all_numbers – clear the SMS interception list;
- #unblock_numbers – remove specified numbers from the SMS interception list;
- #sentid – send an SMS with the Trojan’s ID to a specified number.
In late May 2014, we detected the first mobile encryptor, Trojan-Ransom.AndroidOS.Pletor.a. It encrypted files on the device and demanded a ransom for them to be decrypted. Some modifications of Pletor used TOR to communicate with the C&C.
A month later, we detected a new modification, Backdoor.AndroidOS.Torec. Unlike previous versions, it did not use TOR and targeted credit card details: the Trojan overlaid the official Google Play Store app with a phishing window that included data entry fields.
We assigned the verdict Trojan-Banker.AndroidOS.Acecard.a to this modification, and classified it as a separate family of malware. From that moment on, all new versions of the Trojan have been detected as belonging to the Acecard family.
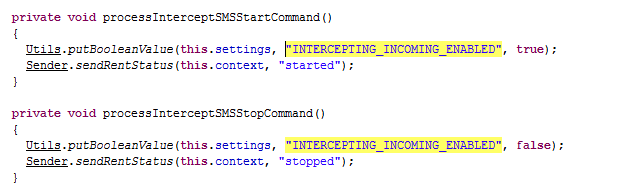
An analysis and comparison of the code used in Backdoor.AndroidOS.Torec.a, Trojan-Ransom.AndroidOS.Pletor.a and Trojan-Banker.AndroidOS.Acecard.a has shown they were all written by the same cybercriminals. Here are some clear examples:
Code from the SmsProcessor class of the Trojan Backdoor.AndroidOS.Torec.a
Code from the SmsProcessor class of Trojan-Banker.AndroidOS.Acecard.a
Code from the SmsProcessor class of Trojan-Ransom.AndroidOS.Pletor.a
Here is another example:
Code from the SmsProcessor class of the Trojan Backdoor.AndroidOS.Torec.a
Code from the SmsProcessor class of Trojan-Banker.AndroidOS.Acecard.a
Code from the SmsProcessor class of Trojan-Ransom.AndroidOS.Pletor.a
A lot of the class, method and variable names are the same for all three Trojans. The code of the corresponding methods is either the same or very similar with only minor differences.
Acecard’s progress
The initial Trojan, Trojan-Banker.AndroidOS.Acecard.a, could only handle four commands sent from the C&C:
- #intercept_sms_start – start intercepting incoming SMSs;
- #intercept_sms_stop – stop intercepting incoming SMSs;
- #send_sms – send an SMS to the number specified in the command;
- #control_number – change the phone’s control number.
The next modification of Acecard was detected in late August 2014 and used the TOR network for C&C communication, just like the earlier Pletor. Besides that, we identified two more differences. Firstly, the list of supported commands had grown to 15; nearly all of these commands had been seen before in earlier versions of the Trojan Torec:
- #intercept_sms_start – start intercepting incoming SMSs;
- #intercept_sms_stop – stop intercepting incoming SMSs;
- #ussd – create a USSD request;
- #check_gps – send the device’s coordinates to the C&C;
- #block_numbers – add numbers to the list of senders from which SMSs will be intercepted;
- #unblock_all_numbers – clear the SMS interception list;
- #unblock_numbers – remove specified numbers from the SMS interception list;
- #listen_sms_start – start stealing incoming SMSs;
- #listen_sms_stop – stop stealing incoming SMSs;
- #check – send the Trojan’s ID to the C&C;
- #grab_apps – send the list of applications installed on the mobile device to the C&C;
- #send_sms – send an SMS to the number specified in the command;
- #control_number – change the phone’s control number;
- #sentid – send an SMS with the Trojan’s ID to a specified number;
- #show_dialog – show a dialog window to the user with specific objects (data entry fields, buttons etc.) depending on the C&C command parameters.
The second difference was the number of phishing windows. Along with the official Google Play Store app, this Trojan now overlaid the display of the following apps with its own windows:
- IM services: WhatsApp, Viber, Instagram, Skype;
- The apps of the VKontakte, Odnoklassniki and Facebook social networks
- The Gmail client
- The official Twitter client
In the second half of October 2014, we detected the next modification of Acecard. It no longer used TOR (neither have any of the versions of the Trojan subsequently detected). However, there was another, more important difference: starting with this version of the Trojan, there have been dramatic changes in the geography of the targeted users. The earlier versions mostly attacked users in Russia, but starting in October 2014 the bulk of Acecard attacks targeted users in Australia, Germany and France. Russia accounted for just 10% of the attacked users. This trend continued for another four months, until February 2015, but even then Australia, Germany and France still remained among the most frequently attacked countries.
At the same time, the geography of Pletor attacks remained largely unchanged: most attacks targeted, and continue to target, users in Russia and the US. The TOP 5 most attacked countries also includes Ukraine, Belarus and Saudi Arabia.
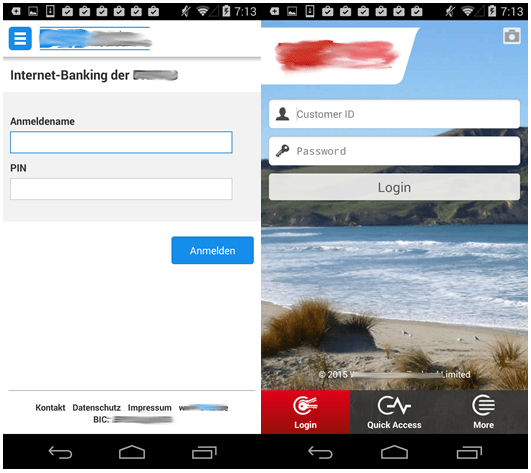
A new modification of Acecard emerged in mid-November 2014. As well as stealing passwords from popular social network clients, it started to overlay the banking app of Australia’s most popular bank with a phishing window. Just two days later, we managed to detect another modification of this Trojan that was already attacking the apps of four Australian banks.
This functionality has persisted up to the very latest Trojan-Banker.AndroidOS.Acecard modifications that we detect.
This version of Acecard also checks the country code and the service provider code as it launches, and if it finds itself in Russia, it shuts down. This check is carried out in almost all subsequent modifications. Interestingly, similar changes to Trojan-Ransom.AndroidOS.Pletor only took place in late March 2015, and did not extend to all versions of the malware.
For the next nine months, there was practically no change in the functionality of the new Acecard modifications that emerged, until early August 2015 when we detected a new version that was capable of overlaying the PayPal mobile app with its own phishing window.
There was also a new command that this version could perform – #wipe. When this command is received, Acecard resets the mobile device to factory settings.
It should be noted that there has been a dramatic increase in Acecard developer activity since June 2015. Before, we typically identified 2-5 files a month related to this Trojan; since June we have detected around 20 files per month.
Number of Acecard files detected each month
The graph above shows the number of files associated with the banking Trojan Acecard that are detected each month; these include both the modifications of Acecard and related files, such as downloader Trojans. The dramatic rise in file numbers detected in November and especially December is down to the malware writers making active use of a commercial code obfuscator and the emergence of obfuscated versions of the Trojan.
Also at this time, there was an increase in the number of attacks using this malicious program.
The number of unique users attacked by Acecard per month
In the first half of September, we detected a new modification of Acecard. Its new capabilities included overlaying the windows of more mobile banking apps, including those of one Australian bank, four New Zealand banks and three German banks.
It means this modification of the Trojan is capable of overlaying 20 apps – including 13 banking apps – with a phishing window.
The subsequent development of Acecard’s “banking business” then got even faster:
- The next modification emerged just several days later, and was capable of overlaying as many as 20 banking applications. The list of targeted apps grew to include another app belonging to an Australian bank, four apps for Hong Kong banks and three for Austrian banks.
- In late September, a new modification came out with a new functionality: the malicious program included a list of bank phone numbers, so text messages arriving from those banks are redirected to the cybercriminal. The Trojan has a list of phrases, so it can compare incoming text messages and identify those with verification codes for bank operations or registration, and send just the code to the cybercriminal, rather than the full SMS. This version of Acecard intercepts SMSs from 17 Russian banks.
- Early October saw the emergence of a new modification that attacked the banking apps of the three largest US banks. Interestingly, from the very start, the US has been among the TOP 10 countries most often attacked by this Trojan; however, December 2015 saw a dramatic rise in the number of attacks on US users. In that month, the US came third in terms of the number of unique users attacked by this malware.
- In mid-October, a new modification appeared capable of overlaying as many as 24 financial applications, including apps belonging to five Australian banks, four Hong Kong banks, four Austrian banks, four New Zealand banks, three German banks, three Singapore banks, and the PayPal app.
- A new modification was detected in early November that has a phishing window that targets an app belonging to a Spanish bank.
It should also be noted that virtually all versions of Acecard can handle a C&C command that orders the Trojan to overlay any specified app with its own window. Perhaps the cybercriminals thought this option was more promising, because many of the versions detected in November and December 2015 have a dedicated window that only overlays Google Play and Google Music apps to target credit card details. No other applications will be overlaid without first receiving the appropriate C&C command.
The most recent versions of the Acecard family can attack the client applications of more than 30 banks and payment systems. Considering that these Trojans are capable of overlaying any application upon command, the overall number of attacked financial applications may be much larger.
Although the Trojans belonging to this family can attack users from a long list of countries, most attacks target users in Russia, Australia, Germany, Austria and France.
Number of unique users attacked by country
In Germany and Australia, the Trojan-Banker.AndroidOS.Acecard family is the most widespread type of mobile banker Trojan targeting users.
Propagation
In many countries, Trojans belonging to the Acecard family are typically distributed with the names Flash Player or PornoVideo, although other names are sometimes used in a bid to imitate useful and popular software. This malware family also propagates with the help of downloader Trojans that are detected by Kaspersky Lab’s products as Trojan-Downloader.AndroidOS.Acecard.
We should note that on 28 December we were able to spot a version of the Acecard downloader Trojan – Trojan-Downloader.AndroidOS.Acecard.b – in the official Google Play Store.
A Trojan-Downloader.AndroidOS.Acecard.b page in Google Play Store
The Trojan propagates under the guise of a game, but in reality it has no useful functionality. The main goal of this malicious app is to download and install a fully functional modification of the banking Trojan Acecard. Its creators didn’t even bother to make it look like a legitimate application: when the malware is installed from Google Play, the user will only see an Adobe Flash Player icon on the desktop screen.
We have also been able to detect a new modification of the downloader Trojan, Trojan-Downloader.AndroidOS.Acecard.c. It differs in that the Trojan, once launched, uses vulnerabilities in the system to gain super-user rights. With these privileges – Trojan-Downloader.AndroidOS.Acecard.c can install the banking Trojan Acecard into the system folder, which makes it impossible to delete using standard tools. However, in most cases this propagation method is used to spread another Trojan that we are already familiar with – Trojan-Ransom.AndroidOS.Pletor.
The cybercriminals are using virtually every available method to propagate the banking Trojan Acecard, be it under the guise of another program, via official app stores, or via other Trojans. This combination of propagation methods, which includes the exploitation of vulnerabilities in the operating system, along with Acecard’s capabilities make this mobile banker one of the most dangerous threats to users.
MD5
58FED8B5B549BE7ECBFBC6C63B84A728
8D260AB2BB36AEAF5B033B80B6BC1E6A
CF872ACDC583FE80B8F54957E14355DF
FBBCCD640CE75BD618A7F3187EC1B742
01E8CEA7DF22B1B3CC560ACB049F8EA0
DDCE6CE143CCA26E59063E7A4BB89019
9D34FC3CFCFFEA760FC1ADD377AA626A
03DA636518CCAF432AB68B269F7E6CC3
05EBAA5C7FFA440455ECB3519F923B56
E3FD483AD3731DD62FBE027B4E6880E6
53888352A4A1E3CB810B2A3F51D0BFC2
E1C794A614D5F6AAC38E2AEB77B139DA
54332ED8EA9AED12400A75496972D7D7
5DB57F89A85F647EBBC5BAFBC29C801E
702770D70C7AAB793FFD6A107FD08DAD
CF25782CAC01837ABACBF31130CA4E75
07DF64C87EA74F388EF86226BC39EADF










































The evolution of Acecard