
Comparisons with Shamoon and DarkSeoul
This week, for the first time, the FBI issued a Flash warning about a destructive wiper activity, used in the attack on Sony Pictures Entertainment. Samples of this Destover malware contained configuration files created on systems using Korean language packs.
Since the attack, further information about the malware has surfaced in one form or another, but some details, such as those relating to the previous activity of the prime suspects, are still to be examined.
So, while Sony Pictures silently completes its costly clean-up efforts and prepares to release “The Interview”, let’s discuss some of the malware functionality, glaring similarities with other wiper events, and some of the suspect group’s previous activity.
The first thing to note is that destructive activity targeting the networks of large organizations is clearly becoming more commonplace. Previous major wiper malware is discussed here. For these, most of the related events occurred in the Middle East and the Korean Peninsula. We also noted a separate Eastern European BE2 ICS environment-related wiping event, covered in more detail here. And it’s hard to ignore the complete customer data wipe of Code Spaces in Great Britain by a cybercriminal holding them for ransom, as reported here.
The malware involved in the Sony Entertainment attack is called Trojan Destover and is capable of wiping disk drives and MBR.
Destover Wiper Functionality
The most interesting aspects of the destructive functionality of the malware are related to the selection and storage/delivery of the drivers that are now used repeatedly in these kinds of sabotage attacks.
The Destover droppers install and run EldoS RawDisk drivers to evade NTFS security permissions and overwrite disk data and the MBR itself. There are implications for data recovery in this. In the case of the DarkSeoul malware, the overwritten data could be restored using a method similar to the restoration of the Shamoon ‘destroyed’ data. Destover data recovery is likely to be the same.
The chain of intermediary components leading to the destructive payload follows multiple stages (which have previously been described elsewhere), with capabilities set to run in several modes, just like Shamoon:
- The sample is run on a 32-bit OS for the first time.
- The sample is run on a 32-bit OS as a self-installed service, with one of several code paths.
- The sample is run on a 64-bit OS as a self-installed service.
On a first run, it creates the ‘Backup and Restore Management’ Windows brmgmtsvc service, adds its own executable and sets a startup ‘-i‘ switch. It also drops several copies of itself and starts each of them with a different switch: -m, -d, and -w.
-m (mbr overwrite):
This attempts to connect with the three IP addresses. Even if this is unsuccessful, process execution takes place.
It fetches its resource that contains the compressed EldoS RawDisk driver, and writes it out to the temp directory as a ‘usbdrv3.sys’.
It then installs the driver as the usbdrv3 service ‘USB 3.0 Host Controller’.
After this, it starts the driver service and closes its service handle.
It then creates a filehandle to the driver with write permissions:
‘\\?\ElRawDisk\??\\PhysicalDrive0#99E2428CCA4309C68AAF8C616EF3306582A64513E55C786A864BC83DAFE0C78585B692047273B0E55275102C664C5217E76B8E67F35FCE385E4328EE1AD139EA6AA26345C4F93000DBBC7EF1579D4F’
and writes to that handle with 64k strings of ‘0xAAAAAAAA’. ← note that the issue of a lengthy license key (#99E2428…) is discussed in our Shamoon The Wiper – part ii blogpost.
It then creates new threads, each of which attempts to connect to any possible physical drive letter and overwrite them as well.
-d (data overwrite):
This attempts to connect with the same three IP addresses. Again, process execution takes place regardless of communications.
It gets the logical drives and traverses recursively through them, identifying all data files. If it is not .exe or .dll, the process overwrites file contents with ‘0x0df0adba’ in a 20k chunk. This overwrite is completed from user mode, without the EldoS drivers.
It then attempts to delete the data file using the win32 api ‘DeleteFileW’. As it recurses through all the system’s directories, it attempts to delete .exe and .dll files.
-w (web server):
This attempts to connect with the same three IP addresses. Again, process execution takes place regardless of communications.
It stops the Windows Terminal Services from the cmd line: ‘cmd.exe /c net stop termservice /y’
Then finds resource#85, decompresses and writes contents out to ‘c:\windows\iissvr.exe‘.
It launches the iissvr.exe process and exits.
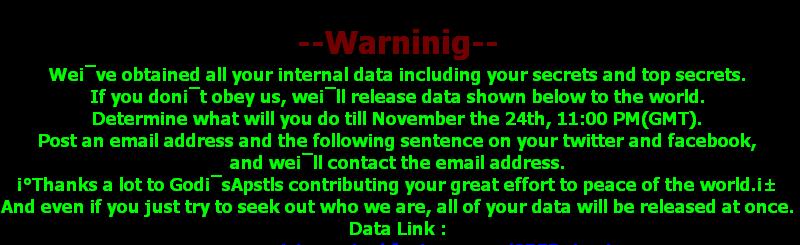
iissvr is what it seems to be – a web server that maintains an encoded JPG, HTML and WAV file. It listens on Port 80 and serves these files. The full graphic and scrolling green warning can be found later in the article. The decoded jpg here:
Lastly, after a two hour sleep, the original service restarts the machine with a call to ExitWindowsEx(EWX_REBOOT|EWX_FORCE, 0). This forces an exit but delays the shutdown itself while system state file creation occurs.
Commonalities Across Wipers
Just like Shamoon, the Destover wiper drivers are commercially available EldoS RawDisk driver files.
Just like Shamoon, the Destover wiper drivers are maintained in the droppers’ resource section.
Just like Shamoon, the DarkSeoul wiper event included vague, encoded psuedo-political messages used to overwrite disk data and the master boot record (MBR).
Just like DarkSeoul, the Destover wiper executables were compiled somewhere between 48 hours prior to the attack and the actual day of attack. It is highly unlikely that the attackers spear-phished their way into large numbers of users, and highly likely that they had gained unfettered access to the entire network prior to the attack.
The Shamoon components were compiled in a similarly tight timeframe prior to their deployment. The CompiledOn timestamps all fall within five days of their executables’ detonation. Nearly all were compiled on Aug 10, 2012 (between 00:17:23 and 02:46:22) and set to detonate on Aug 15, 2012. That is a tight window to quietly deploy these binaries considering the fact that tens of thousands of machines were destroyed with this payload.
In all three cases: Shamoon, DarkSeoul and Destover, the groups claiming credit for their destructive impact across entire large networks had no history or real identity of their own. All attempted to disappear following their act, did not make clear statements but did make bizarre and roundabout accusations of criminal conduct, and instigated their destructive acts immediately after a politically-charged event that was suggested as having been at the heart of the matter.
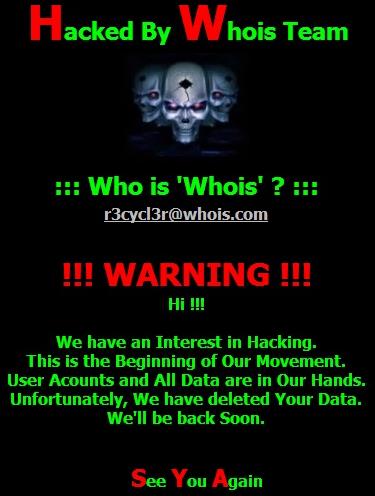
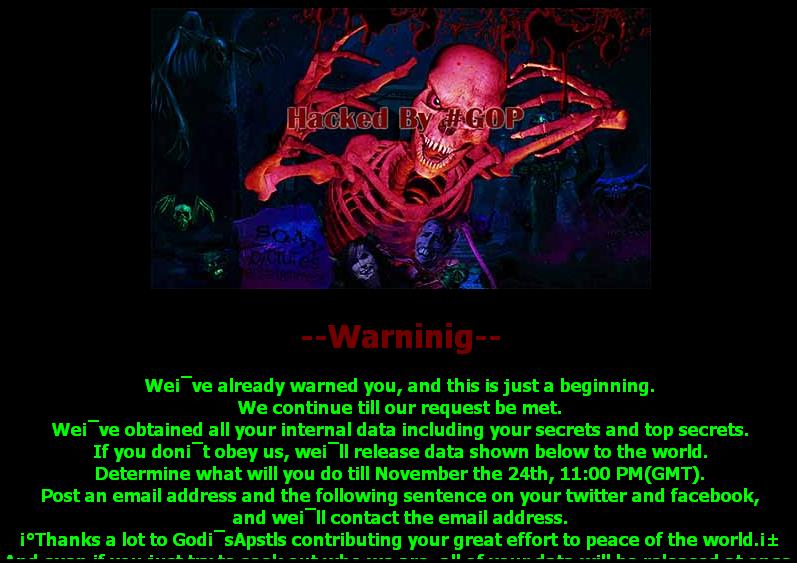
Images from the DarkSeoul ‘Whois’ and Destover ‘GOP’ groups included a ‘Hacked by’ claim, accompanied by a “warning” and threats regarding stolen data. Both threatened that this was only the beginning and that the group will be back. It appears that original skeletal artwork was also included in both.
Whois team graphics and warning:
GOP team graphics and warning:
Differences between the Destover and DarkSeoul Wiper attacks include Destover’s lack of *nix scripts to erase partitions across Linux systems.
The above list of commonalities does not, of course, prove that the crew behind Shamoon is the same as the crew behind both DarkSeoul and Destover. But it should be noted that the reactionary events and the groups’ operational and toolset characteristics all carry marked similarities. And, it is extraordinary that such unusual and focused acts of large scale cyber-destruction are being carried out with clearly recognizable similarities.
Network activity
Related beacon destinations were published as:
- 88.53.215.64
- 217.96.33.164
- 203.131.222.102
However, directly related samples perform callbacks to a number of other IP addresses as well. Kaspersky Security Network (KSN) data presents a complete lack of malware being served from any of these addresses in the past:
- 58.185.154.99
- 200.87.126.116
- 208.105.226.235
- 212.31.102.100
The connections appear arbitrary and inconsequential to the execution of the malicious package. Some are not currently active. These IPs all appear to be oddly selected.
Some of these addresses are known to have performed RDP Scans in the recent past. In late 2012, 217.96.33.164 was a known RDP brute forcing network scanner. The server is hosted at an IP address in Poland, maintained at that provider since 1996.
In early 2014, 88.53.215.64 was hosted in Italy and served as a ‘Hide My Ass’ premium and free proxy server over port 443. The malware attempts to connect to that server on ports 8000 and 8080, and currently no resources are available.
200.87.126.116 also previously served as a free SOCKS proxy in 2011 and 2012. Often, these sorts of resources were misused by spammers and blackhat SEO scammers.
Previous Backdoors
The DarkSeoul campaigns have been linked to several families of Trojans and backdoors, all used over the course of several years. Some links are much stronger than others:
- Concealment Troy
- DarkSeoul
- HttpDr0pper
- HttpTroy
- TDrop
Destover MD5s
Trojans:
| MD5 | Size | CompiledOn | Kaspersky name |
| d1c27ee7ce18675974edf42d4eea25c6 | 262 kb | 2014.11.22 00:06:54 | Trojan.Win32.Destover.a |
| 2618dd3e5c59ca851f03df12c0cab3b8 | 430 kb | 2014.11.22 00:05:02 | Trojan.Win32.Destover.d |
| 760c35a80d758f032d02cf4db12d3e55 | 244 kb | 2014.11.22 04:11:08 | Trojan.Win32.Destover.c |
| b80aa583591eaf758fd95ab4ea7afe39 | 304 kb | 2014.11.24 04:12:55 | Trojan.Win32.Destover.b |
| e1864a55d5ccb76af4bf7a0ae16279ba | 112 kb | 2014.11.13 02:05:35 | Backdoor.Win32.DestoverServ.a |
| a3fa8c7eb4f061ab8b9f7829c6741593 | 111 kb | 2014.05.03 07:10:22 | Trojan.Win32.Destover.f |
| 2c545b89acdb9877da5cbb96653b1491 | 53 kb | 2014.07.14 13:38:18 | Trojan.Win32.Destover.e |
| e904bf93403c0fb08b9683a9e858c73e | 90 kb | 2014.07.07 08:01:09 | Trojan.Win32.Destover.d |
Eldos Drivers:
6aeac618e29980b69721158044c2e544 (32-bit), signed by the EldoS Corporation
86e212b7fc20fc406c692400294073ff (64-bit), signed by the EldoS Corporation
Certificate (6aeac618e29980b69721158044c2e544 32-bit and
86e212b7fc20fc406c692400294073ff 64-bit):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 |
Data: Version: 3 (0x2) Serial Number: 01:00:00:00:00:01:10:0c:98:3a:31 Signature Algorithm: sha1WithRSAEncryption Issuer: C=BE, O=GlobalSign nv-sa, OU=ObjectSign CA, CN=GlobalSign ObjectSign CA Validity Not Before: Jan 10 15:20:07 2007 GMT Not After : Jan 10 15:20:07 2010 GMT Subject: C=VG, O=EldoS Corporation, CN=EldoS Corporation/emailAddress=info@eldos.com Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (1024 bit) Modulus: 00:d7:60:2f:bf:3c:85:1b:f3:a1:19:8c:4d:0e:49: c5:a5:f5:16:15:b6:ea:91:e2:c2:92:7b:d6:e5:2a: 1e:68:8c:7b:28:eb:07:dc:b0:3a:dd:11:ee:84:a9: 8b:6f:04:b0:ae:c2:2d:bc:b7:56:41:61:e1:ae:01: 0d:0e:83:47:00:3a:ca:b5:12:fb:e5:b6:55:ac:e0: 94:00:5b:e0:61:70:24:ba:d9:ef:4a:e2:af:8f:21: 93:9e:8b:83:17:2a:e4:3d:74:e6:07:c8:4a:69:ed: 60:9b:89:6e:5b:85:50:49:52:f9:fa:91:63:9f:61: a7:ea:e2:3e:d7:1b:07:22:a1 Exponent: 65537 (0x10001) X509v3 extensions: Netscape Cert Type: Object Signing X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment, Data Encipherment X509v3 Authority Key Identifier: keyid:D2:5B:F3:4B:26:4B:A5:B0:E7:5D:FD:56:7F:F6:F1:2E:38:4E:53:A0 X509v3 CRL Distribution Points: Full Name: URI:http://crl.globalsign.net/ObjectSign.crl Signature Algorithm: sha1WithRSAEncryption 44:0d:5b:2c:f4:c3:c0:91:c0:9f:4d:91:f0:25:5c:79:72:ff: 82:7a:a8:97:fb:08:2b:c2:eb:ae:4b:78:b6:a8:0f:5b:3a:1d: 12:c9:07:81:d0:16:e0:94:1e:69:3c:43:c1:d8:85:b1:4c:1a: 21:84:1c:c8:ed:0a:7e:e4:55:b7:f8:ae:69:a8:b0:8c:10:da: 6e:57:f4:a3:62:5b:2b:4f:06:25:a9:35:f0:63:cc:3f:e0:f6: 4c:ee:1d:d8:9f:d8:ae:d3:fe:de:3b:0b:c5:f3:19:1c:2a:37: ad:0d:5c:87:5e:da:8f:31:02:d3:78:5d:f1:30:28:78:c3:86: f7:b2:f6:6c:2d:d8:45:8a:8b:16:eb:bb:d0:6e:5b:98:68:8e: 9b:cc:7e:77:9d:0d:b3:5f:01:d8:57:26:6d:cf:85:2a:46:52: 0f:79:93:85:f7:19:14:01:73:d5:03:e7:96:1a:16:cd:24:0b: 67:6d:f9:72:55:b8:b9:e9:be:07:58:b3:01:bd:a1:18:57:bb: b3:19:e5:88:0e:f5:96:fe:eb:b8:66:a6:c6:2c:62:b5:21:59: f2:d9:4d:2b:d1:59:20:07:13:78:26:dc:d5:b3:d1:55:47:5e: 2e:cb:cb:cc:04:7c:d5:e2:9d:7c:24:b1:18:70:da:1f:54:5b: 59:88:d1:17 Data: Version: 3 (0x2) Serial Number: 01:e2:b4:f7:59:81:1c:64:37:9f:ca:0b:e7:6d:2d:ce Signature Algorithm: sha1WithRSAEncryption Issuer: C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Code Signing CA-1 Validity Not Before: Sep 18 00:00:00 2012 GMT Not After : Sep 22 12:00:00 2015 GMT Subject: C=US, ST=California, L=CULVER CITY, O=Sony Pictures Entertainment Inc., CN=Sony Pictures Entertainment Inc. Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:b6:08:80:f6:6d:9c:3a:f4:fb:45:bc:bd:6a:27: e5:97:23:fa:6a:5d:39:08:97:37:53:13:70:85:1b: 0e:08:b1:b7:5f:e3:78:6e:b1:6b:26:7a:82:86:f8: 37:2d:b0:b2:65:f0:8a:56:c7:e1:1a:88:19:f9:00: bd:c3:4b:8d:97:10:b6:9a:09:14:8d:95:0a:75:56: cd:c5:2f:1c:ad:21:82:cb:8c:ad:8d:78:11:1e:b8: 50:94:90:96:7a:e4:69:38:9c:bd:2f:4c:8c:2b:23: 45:f1:ac:59:2f:10:12:d4:64:3a:9b:41:5d:14:2b: 56:10:eb:c6:15:ed:1d:f0:06:d3:0e:9e:96:8e:c1: 0e:cf:62:17:7c:c7:a9:d5:2a:40:99:d6:a2:68:93: f6:02:2a:1e:95:e6:1e:a4:d6:c4:fd:61:7d:d7:15: 9a:1f:2d:ab:4e:fc:61:9f:d8:54:55:8e:79:d3:57: 8a:22:14:31:d4:a4:4e:a5:43:ec:4b:35:04:8d:f8: 10:37:10:3f:bb:2a:ae:b7:b8:a1:16:f4:f6:02:df: 97:fc:32:95:97:38:23:48:c2:96:b3:aa:9f:88:66: 26:eb:d4:70:38:2f:84:b1:e0:1e:a1:27:5f:3f:14: b7:dd:4c:f2:c7:22:6a:1a:f8:85:1a:57:23:b3:c7: 58:1f Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Authority Key Identifier: keyid:7B:68:CE:29:AA:C0:17:BE:49:7A:E1:E5:3F:D6:A7:F7:45:8F:35:32 X509v3 Subject Key Identifier: 51:6E:D7:E5:BB:2E:FD:39:6B:0D:37:D5:D0:70:6B:5A:8C:D6:11:F8 X509v3 Key Usage: critical Digital Signature X509v3 Extended Key Usage: Code Signing X509v3 CRL Distribution Points: Full Name: URI:http://crl3.digicert.com/assured-cs-2011a.crl Full Name: URI:http://crl4.digicert.com/assured-cs-2011a.crl X509v3 Certificate Policies: Policy: 2.16.840.1.114412.3.1 CPS: http://www.digicert.com/ssl-cps-repository.htm User Notice: Explicit Text: Authority Information Access: OCSP - URI:http://ocsp.digicert.com CA Issuers - URI:http://cacerts.digicert.com/DigiCertAssuredIDCodeSigningCA-1.crt X509v3 Basic Constraints: critical CA:FALSE Signature Algorithm: sha1WithRSAEncryption 90:0f:0b:0f:93:f7:77:e7:34:dc:b4:2a:7e:bd:d1:0f:05:ac: a5:9d:c8:1c:77:18:cd:28:90:28:e7:c6:ac:ad:f9:9e:b0:c6: 74:db:da:8c:b2:38:06:c5:a0:e4:cd:66:e4:ef:f7:21:58:1f: 9a:4f:17:3c:e1:af:c3:67:1e:37:ab:2a:2b:8f:7d:bc:9e:eb: 9b:f5:aa:c0:24:80:70:63:b0:2a:10:54:27:01:12:ec:61:12: 97:2d:98:c5:6f:e5:7e:1c:7c:17:2c:f5:ad:40:fb:b2:44:40: fa:e1:02:45:22:7d:6f:6d:04:fc:ff:2c:d2:e5:2f:3e:49:5c: 72:4b:0c:5a:ce:6e:13:44:79:f9:b9:26:d9:2e:6f:4d:05:72: 0d:d2:e9:bc:66:88:af:63:5b:1b:44:50:a4:c7:e4:bc:73:d6: ac:25:7c:1a:88:37:c2:71:3f:1c:32:38:32:12:55:75:db:55: 6d:d9:1e:40:a7:d3:35:f4:bf:86:a3:72:60:49:c3:a4:9a:2e: 4d:5d:0d:4d:97:2b:34:91:5c:e1:e6:a9:93:eb:d2:62:2a:ef: a1:73:6e:a4:0b:22:d4:31:a8:d5:53:9d:26:29:e1:1c:4a:04: c5:8a:df:15:01:42:6f:a2:b3:3b:da:2e:e5:4c:b5:53:6b:76: 86:b2:25:29 |
Previous and Parallel Research References
- Exclusive: FBI warns of ‘destructive’ malware in wake of Sony attack
- Dissecting Operation Troy: Cyberespionage in South Korea, McAfee, 2013 (PDF)
- Darkseoul/Jokra Analysis And Recovery, Fidelis Cybersecurity, 2013 (PDF)
- Analyzing Unknown Malware
- DarkSeoul – Jokra – MBR wiper samples
- Shamoon The Wiper: Further Details (Part II)





















Sony/Destover: mystery North Korean actor’s destructive and past network activity