
Earlier today, reports of a number of cyberattacks against various South Korean targets hit the news.
The attackers, going by the handle ?Whois Team¦ left a number of messages during the defacements:
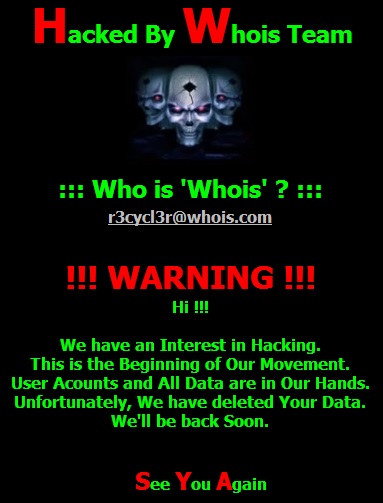
The code used for defacement, posted by an anonymous user to the ?pygments.org¦ forum (see http://pygments.org/demo/68313/) indicates several e-mails used by the attackers:
arrFadeTitles[1] = “dbM4st3r@whois.com”;
arrFadeTitles[2] = “d3sign3r@whois.com”;
arrFadeTitles[3] = “vacc1nm45t3r@whois.com”;
arrFadeTitles[4] = “r3cycl3r@whois.com”;
arrFadeTitles[5] = “s3ll3r@whois.com”;
The screenshots from victim-s computers indicate the at ?Wiper¦ type of malware was also used. We have previously written about two other ?Wiper¦-style malwares: Iranian Wiper and Shamoon.
So, is this an isolated incident or part of a bigger cyberwar campaign? Honestly speaking, we don-t know. If a nation state is NOT behind these attacks, then it’s just cyber-terrorism; cyberwar requires a nation state to be behind the attacks.
In general, if the attacks target critical infrastructure, they can be considered cyber-terrorism. According to the definition of critical infrastructure, banks can be considered as such, therefore, this counts as a cyberterrorism attack.
Previous incidents like Stuxnet and Wiper were part of an ongoing cyberwar campaign that went for years, although in a more stealthy fashion.
Obviously, the attacks were designed to be ‘loud’ – the victims are broadcasting companies and banks. This makes us think we are not dealing with a serious, determined adversary but script kiddies or hacktivists looking for quick fame.






















South Korean ‘Whois Team’ attacks