
Shortly after disclosure of the Bash bug called “Shellshock” we saw the first attempts by criminals to take advantage of this widespread vulnerability also known as CVE-2014-6271.
The most recent attempts we see to gain control of webservers just create a new instance of bash and redirect it to a remote server listening on a specific TCP port. This is also known as a reverse-connect-shell. Here’s an example of how this attack appears in a webserver logfile:
The attacker listens on IP address 195.xx.xx.101 on TCP port 3333, while the attack’s origin is the IP address 94.xx.xx.131. To gain control of a server with this method, no external binaries are involved.
In another ongoing attack the criminals are using a specially crafted HTTP-request to exploit the Bash vulnerability in order to install a Linux-backdoor on the victim’s server. We’re detecting the malware and its variants as Backdoor.Linux.Gafgyt.
The binary contains two hardcoded IP addresses. The first one is only used to notify the criminals about a new succesful infection. The second IP address is used as a command-and-control server (C&C) to communicate directly with the malware running on the infected webserver.
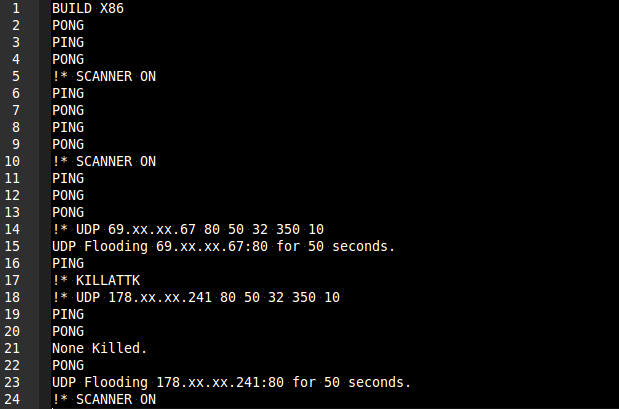
The following picture shows an example on how this communication can look like:
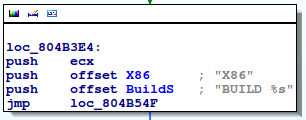
In line 1 the malware sends a “Hello” message and tells the attacker which architecture the binary was compiled for – here it’s x86.
Independently of commands sent by the attackers, the backdoor sends a “PING” request every 30 seconds, which is answered with a “PONG” from the server (for better readability we’ve removed some of PING/PONG-pairs from the example above).
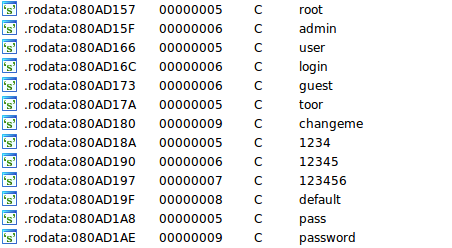
Commands always start with “!* “. The first command we see in this example is the “SCANNER ON” command in line 10. This tells the binary to scan random IP ranges for hosts accepting telnet connections on TCP port 23. When such a host is found, it tries to login using a hardcoded list of common default user/password combinations.
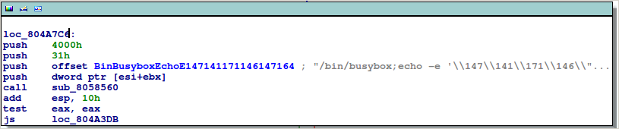
There is also a rudimentary honeypot fingerprinting routine implemented, which makes use of “busybox” as described by the Internet Storm Center here.
The next task the criminals start on the victim’s box is initiated in line 14. Here the binary is told to perform flooding of IP 69.xx.xx.67 using UDP for 50 seconds. In line 17 the attackers stop the flooding in order to restart it in line 18, now targeting 178.x.x.241. The “None Killed.” reply in line 21 appears because the flooding instruction from line 14 was already finished when the attacker tried to stop it using “!* KILLATTK” in line 17.
Here’s the complete list of commands the backdoor accepts:
!* PING – Replies with “PONG!”
!* SH – Execute arbitrary shell command
!* GETLOCALIP – Replies with “My IP: $ipaddr”
!* SCANNER ON | OFF – Scan random networks, perform a very small dictionary attack (see above), test if target is a honeypot
!* HOLD – Hold flooding
!* JUNK – Perform junk flood
!* UDP – Perform udp flood
!* TCP – Perform tcp flood
!* KILLATTK – Kill all flood
!* LOLNOGTFO – Terminate backdoor.
Related binaries:
73b0d95541c84965fa42c3e257bb349957b3be626dec9d55efcc6ebcba6fa489
2d3e0be24ef668b85ed48e81ebb50dce50612fb8dce96879f80306701bc41614
ae3b4f296957ee0a208003569647f04e585775be1f3992921af996b320cf520b
0fde4c72038189e3d86676d84a1370787bcd284f98d1dff7736707fe05af7d9a
3b13eef9b24919dc7e7071068a83defcc4808a41dc86fadf039e08dce1107f7d
64b3751182be737c005fb04ffbe8b4dfe5930ed46066e87a9f6344de1d9985b8



















Shellshock and its early adopters