
There is that expression “TGIF” and I recently noticed that some of my Japanese colleagues/friends would not know what it actually stands for.
Spoiler: It commonly means “Thank god it’s Friday” and probably many working people will be able to appreciate such a feeling.
On the other hand, while many offices may close down for the weekend, it’s the time for bad guys to boost their activity because they count on the fact that they may go unnoticed for some time, at least until the upcoming Monday morning.
The IT community is working hard to find and take down malicious sites as soon as possible, but then … the weekend is the weekend for many.
What happened just last Friday may be a good example of such malicious weekend activity. We received the following email to one of our inboxes:
The email body utilizes some social engineering in order to scare the email receiver about possible loss of emails. It also somehow mentions “high massage” but that may just be a spelling error on the bad guy’s side.
When we click the contained link (which is, of course, one of those “don’t do this at home” things), we see the following:
After clicking “OK”, we get a popup which looks very much like the popup of a Microsoft email client. Note that it is quite well crafted, containing the domain name of the email receiver several times.
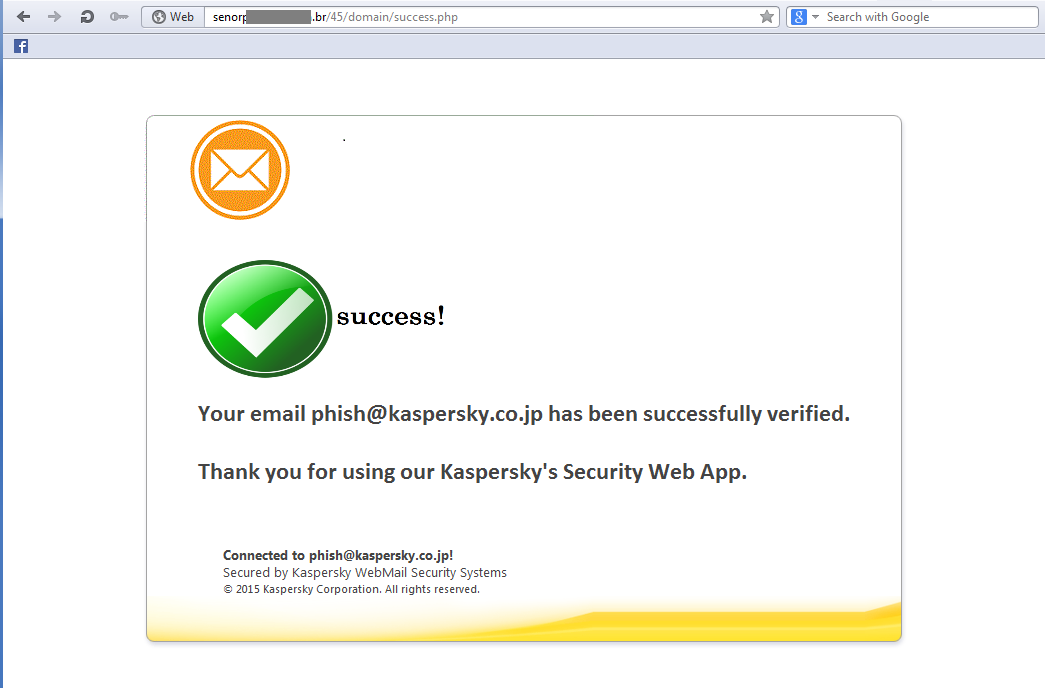
When we input some data into that form, we get this:
Again, it looks well crafted, containing the domain name several times, and even including a copyright notice.
To top it all, that page contains functionality to search the web for the mentioned domain name and finally directs the user’s browser to the search result:
The above content may not seem too convincing to an average home user. This phish seems more likely to target corporate users, as the style of the information shown above mimics the corporate environment very well.
However, attentive users may spot the following details which give away the fake:
- Email sender – mismatching the domain name;
- “Hello User” – is probably not commonly used to address staff;
- All clickable links in the email body point to the same location;
- Spelling mistakes like “massage”;
We have added the malicious site to our anti-phishing denylist.
Updated Sep. 4th 2015:
Only minutes after we published the above content, another similar email arrived in our inbox:
Taking a quick look at the email headers, we noticed that the email appears to have been sent using a “maxo.php” file from a server in Japan:
Intrigued by that information, we tried to figure out what this maxo.php file could be.
Searching the web for the file name gave some interesting results. One of them was an infamous backdoor with no less than 40 layers of encryption:
But we were looking for something else, namely some kind of php mailer.
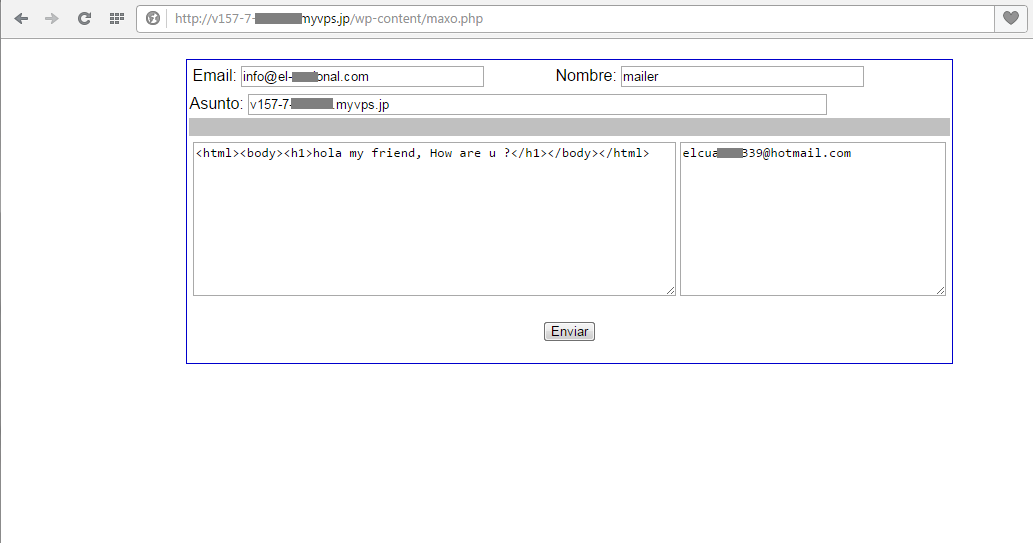
The actual server seen in our email headers did indeed serve that script:
It was a publicly accessible web form with fields for spoofing email address and sender name, and fields for email body and receivers list. The contained data is hardcoded in the script itself. The script also contains a function to trigger file uploads to the host.
When searching the web for the address shown in the “Email” field, we found a whole bunch of reports going back to December 2014 – all regarding the same phishing scheme.
We have notified the relevant ISP of the malicious activity.
TGIF(P) – Thank god it’s fried phish





























garry sives
Wow! I wish I had paid more attention to the possibilities of the upcoming revolution of computing,but sadly in the early 70s the after school computer club was for geeks who revelled in typing fortran and algol this was and still is gobbledygook. But thank got its Friday,no sorry,thank god the team at Karspersky have their minds trained to protecting the likes of computer illiterate me.Well done guys I thank Barclays for introducing you to me.Garry Sives.