
Background
Yesterday a blog post on “The Linux Mint Blog” caught our attention. Apparently criminals managed to compromise a vulnerable instance of WordPress which the project used to run their website. The attackers modified download links pointing to backdoored ISO files of Linux Mint 17.3 Cinnamon edition. This “should only impact people who downloaded this edition on February 20th”, the author of the blog stated.
We managed to get our hands on the malware embedded in the ISO images. Let’s have a quick look.
Malware used
The criminals used a simple backdoor, which is controlled via an unencrypted IRC connection. We found four hardcoded C&C addresses. At the time of writing only one of them was available. We saw approx. 50 connected clients just in this channel called “#mint”:
The malware is capable of:
- running several types of UDP and TCP flooding (used in DDoS attacks)
- downloading arbitrary files to the victim’s machine
- executing arbitrary commands on the machine
We’re detecting this type of malware as HEUR:Backdoor.Linux.Tsunami.bh.
According to user reports, the compromised ISO images come with the backdoor’s C-source code, located in /var/lib/man.cy, which is compiled on first startup to “apt-cache” and is then executed.
Activity
While monitoring the C&C channel, we saw the criminal sending several SMB-related commands like “smbtree -N” to the connected bots. Apparently the attacker tries to access SMB/CIFS shares available in the local network of the victims.
Conclusion
In order to detect this kind of attack, one should use PKI with strong cryptographic signatures to ensure the integrity of downloaded software.
Integrity-checks based on file hashes like MD5 or SHA256 are insecure if a project’s website is compromised, since the attacker could also adjust the checksums provided on the website.
IOC
Hostnames and IPs
- updates[.]absentvodka[.]com
- updates[.]mintylinux[.]com
- eggstrawdinarry[.]mylittlerepo[.]com
- linuxmint[.]kernel-org[.]org
- 5.104.175.212
MD5s
- d945f9b959f76afe24f3a804fe316806
- 7d590864618866c225ede058f1ba61f0

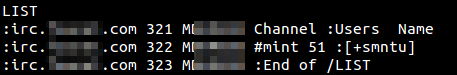





















Beware of Backdoored Linux Mint ISOs