
NO-IP is one of the many Dynamic DNS providers out there, which can be used for free to register a subdomain on top of popular names such as servepics.com or servebeer.com . For a long time, this has been a favorite method for cybercriminals who wanted to register easy to update hostnames to control their malware implants. Yesterday, Microsoft moved against NO-IP and seized 22 of their domains. They also filed a civil case against Mohamed Benabdellah and Naser Al Mutairi, and a U.S. company, Vitalwerks Internet Solutions, LLC (doing business as No-IP.com), for their roles in creating, controlling, and assisting in infecting millions of computers with malicious software harming Microsoft, its customers and the public at large.
Interestingly, Microsoft cited two specific malware families which were used to infect innocent victims with the Bladabindi (NJrat) and Jenxcus (NJw0rm) family of malware . These have been used by multiple cybercriminal and activist groups to target users, including the (in-)famous Syrian Electronic Army. (stay tuned for a more detailed blog on that soon)
In addition to these, the takedown disrupted many other APT operations, which used NO-IP for their C&C infrastructure. These include:
- Flame/Miniflame
- Turla/Snake/Uroburos, including Epic
- Cycldek
- Shiqiang
- HackingTeam RCS customers
- Banechant
- Ladyoffice
- etc…
Based on our statistics, the shutdown has affected in some form at least 25% of the APT groups we are tracking. Some of these hosts that were previously used in large and sophisticated cyberespionage operations are now pointing to what appears to be a Microsoft sinkhole, at 204.95.99.59.
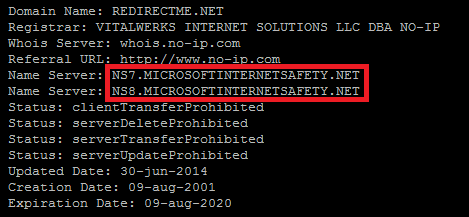
Some top level domains that have been taken away from Vitalwerks and now use Microsoft’s DNS infrastructure include:
- BOUNCEME.NET
- MYFTP.BIZ
- MYVNC.COM
- NO-IP.BIZ
- NO-IP.INFO
- REDIRECTME.NET
- SERVEBEER.COM
- SERVEBLOG.NET
- SERVECOUNTERSTRIKE.COM
- SERVEGAME.COM
- SERVEHALFLIFE.COM
- SERVEHTTP.COM
- SERVEMP3.COM
- SERVEPICS.COM
- SERVEQUAKE.COM
- SYTES.NET
In the meantime, NO-IP / Vitalwerks have published their answer online:
Apparently, the Microsoft infrastructure is not able to handle the billions of queries from our customers. Millions of innocent users are experiencing outages to their services because of Microsoft s attempt to remediate hostnames associated with a few bad actors.
We think yesterday s events have dealt a major blow to many cybercriminal and APT operations around the world.
In the future, we can assume these groups will be more careful on using Dynamic DNS providers and rely more often on hacked websites and direct IP addresses to manage their C&C infrastructure.
Update (2014-07-02): Microsoft published a list of over 20,000 NO-IP hosts that were used in attacks, together with other documents on a specially crafted website www.noticeoflawsuit.com for this incident.
Since the publication of our blogpost, many people have contacted us and complained about disruption of their otherwise clean hosts due to the Microsoft takedown. In fact, two hosts previously used in APT attacks that we were sinkholing were also taken away from us. We were using the logs from these, together with other data from our sinkhole to notify victims in many different countries.
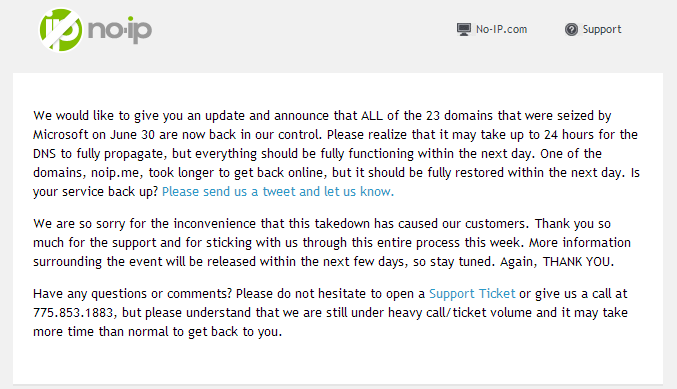
Update (2014-07-04): NO-IP just sent a note to their customers that all 23 domains that were seized by Microsoft are now back in their control. This appears to be true, with Microsoft DNS servers no longer controlling the domains.
Have you been affected about the NO-IP takedown? Please let us know by sharing your comments below.
Microsoft seizes 22 NO-IP domains, disrupts cybercriminal and nation state APT malware operations






















Robert Thompson
It’s pathetic that after taking in hundreds of billions of dollars in profits, Microsoft still subjects its customers to products that are so insecure that botnet operators are able to penetrate Windows systems at will, alternately poaching victims from each other! The world of the Microsoft customer is one of masochistic users being willingly subjected to systematic abuse by the entire world.
FRANCIS
I really agree with that guy, actually the entire world is getting secure with there daily system off which the microsoft doesnt want to solve the situation, its very an abuse even to me as an new operetor to the systems that microsoft tirecoon cant solve yhe problem????