
Malicious macro-enabled Microsoft Office document
The last interesting item found on the same malicious cybercriminal server is a .docm file (a macro-enabled document according to Microsoft Office standards).

It is a malicious file that when opened shows its victims the following content:
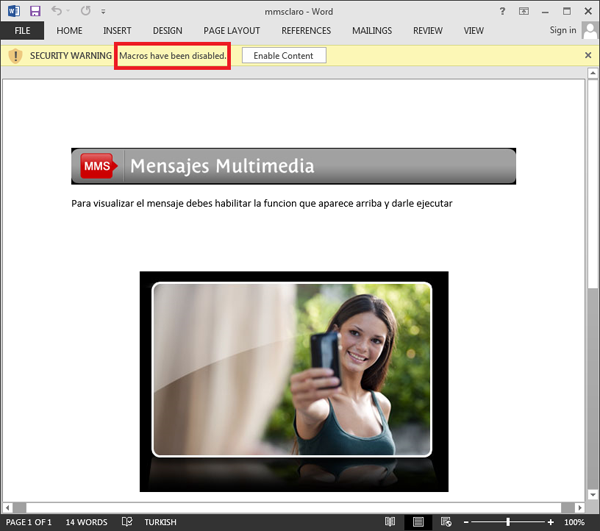
If macros are enabled and a victim clicks on the message to supposedly download an MMS message, two pieces of malware are installed into the machines of victims.
Malicious part of the document
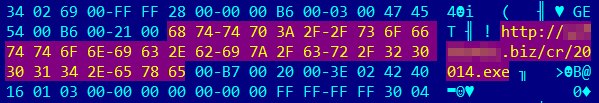
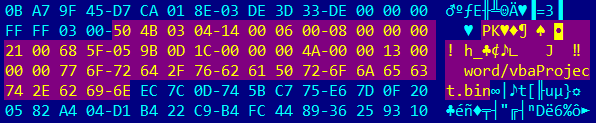
The malicious part of the document is located at 0x00000f14 offset, has 18,944 bytes in size and has the name “vbaProject.bin“.
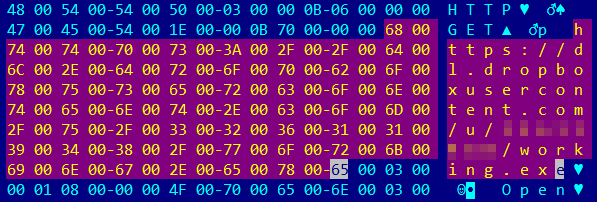
When it is extracted from the main .docm file, it has two different urls downloading two different pieces of malware. Each image in the macro-enabled file downloads different malware when the victim clicks on it.
The first malware is downloaded from the same malicious server located in Panama and the second one from the Dropbox cloud.
Kaspersky Anti-Virus detects both malicious files under the Trojan.MSIL.Agent family.
What is interesting here?
If you look at the image of the document above you will see that the content of the document is in Spanish; however, the language used to edit the document is Turksih. Metadata of the file also confirms it was compiled on a machine where a so-called ilyasOzdogan was the author.
It is interesting to notice that one of the downloaded malicious MSIL.Agents also has the same user name under the source path inside of the compiled binary:
c:userslyaszdoandocumentsdocumentsvisualstudio2012projectswindowsformsapplication13windowsformsapplication13objdebugwindowsformsapplication13.pdb
What does this mean? It means that Latin American cybercriminals are probably not only in touch with cybercriminals from Eastern Europe but from Turkey too.
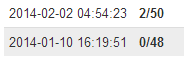
Today, some advanced cybercriminals use exploits to infect the machines of victims, but as you can see from this example, this may be a waste of money since the old school tricks still work for them. If you do not believe me, just see how on January 10, when the file was submitted for the first time to VirusTotal, it registered 0 of 48 detections and at the time of writing this post only 2 of 50 anti-virus solutions detected this malicious sample:
You may follow me on twitter:@dimitribest






















Big Box LatAm Hack (3rd Part – Infection by Office Files)