
Introduction
Last week a good friend (@Dkavalanche) mentioned in his twitter account his findings of a Betabot malware which was spammed via fake emails in the name of Carabineros of Chile. It piqued my attention so I dug a little bit and this is what I found:
The original .biz domain used in the malicious campaign was bought by someone allegedly fromPanama. It’s a purely malicious domain used exclusively for cybercriminal activity; however, the server itself is hosted in Russia! The same server has several folders and files inside, which we will discuss a little bit later. First, let’s speak about the initial malicious binary spoofed via email and then about other things. I will only focus on the most interesting details.
Denuncia_penal.exe
This is the name of the original binary. Translation to English is the “Criminal complaint”.
The file is compiled with fake information and it claims to be a legitimate tool build by NoVirusThanks, called NPE File Analyzer.
So, what is interesting about this malware? It’s a Spy malware which interacts with C2 using some commands like: “JOIN“, “PRIVMSG” and others. It steals data from the clipboard, keystrokes and also makes screenshots. Additionally, it steals cookies from the browsers and sends it via SQLite format to a remote DB.

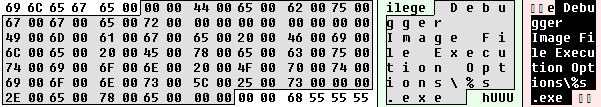
It also has backdoor functionality and it actively fights locally installed AV by manipulating Image File Execution Options denying the execution of 15 different AV solutions. This technique is very harmful because even if the malware is removed but the debuggers are not fixed, the victim won’t be able to successfully install an AV solution. The debugger will just block the execution of the files by its file names.
The malware tries to detect if the sample is executed in a Sandbox environment by detectingSBIEDLL.DLL library which belongs to Sandboxie software and also it tries to detect if the environment is a virtual one by looking for resources like HGFS and VBoxGuest.
While working in the memory you may find the string identifying the sample with the Betabot.

In September 2013, the FBI posted a Public Service Announcement about this threat. However, the difference now is that this botnet is no longer just being used by Russian speaking criminals but by cybercriminals from LatAm as well.
Victims
Who are exactly the victims of this particular campaign? I was able to recover the DB of the email addresses used to spam and basically, if we analyze only 1st level domains and look for a specific geo related ones, then Chile and the Dominican Republic are the main targets:

The complete list is quite long. If we check only geo specific domains, then the Top 10 countries where most of the victims are include:
1. Chile
2. Dominican Republic
3. Spain
4. Argentina
5. Mexico
6. Ecuador
7. Germany
8. France
9. Colombia
10. Italy
Also, it’s important to note that the list of victims has thousands of emails in .edu and .gov domains. In the next post we will discuss a little bit more about the victims and the operation behind the attack.
Kaspersky detects this sample as Trojan.Win32.Neurevt.zp
You may follow me on twitter @dimitriest




















Big Box LatAm Hack (1st part – Betabot)