
It’s two years to the day that the antivirus industry first encountered Bagle – Email-Worm.Win32.Bagle.a. Depending on your point of view, two years could be a long time, or a short time. But whatever position you take, one thing is certain – Bagle has evolved from a single worm into a criminal infrastructure, which is constantly searching for new victims to infect. Bagle has become a business, which is making real profits – clear motivation for cyber criminals. The authors of Bagle have continued to develop the worm’s defences against its main enemy, the anti-virus industry. We’ve seen Bagle evolve from using primitive polymorphic code, to saving the password to an infected archive in graphical form, to the use of denylists. These last list users such as e.g. antivirus and network activity monitoring companies who are likely to attempt to download the latest Bagle variant via malicious links. If a user whose address is denylisted attempts to download the latest Bagle, an error message will be returned instead of the malicious file.
Over the last two years we’ve detected more than 400 modifications of Bagle-related malware. All these malicious programs (Trojan-Proxies, Email-Worms, Trojan-Downloaders, SpamTool etc) are designed to steal information from victim machines, conduct mass mailings and other criminal activity.
As our users know, Kaspersky Lab releases two types of antivirus database update – standard updates, and urgent updates. Urgent updates provide rapid protection against possible epidemics and spamming of malicious programs. The graph below shows the number of urgent updates (axis Y) released every three days (in order to highlight the virus epidemics) throughout 2005 (axis X) we get the following picture:
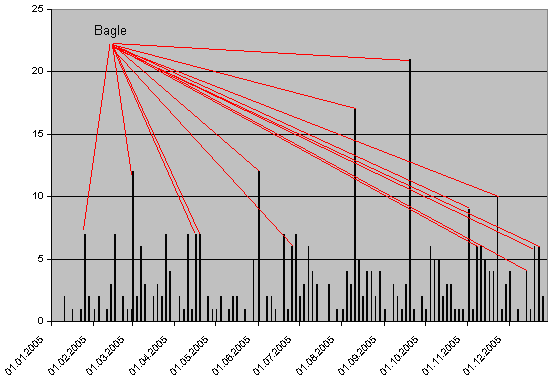
It’s clear that the highest number of urgent updates were released on days when Bagle was very active. During one attack, 21 new modifications were detected. The figures clearly show that users should continue to take the threat posed by Bagle seriously.




















Bagle’s birthday