
Our previous blog on Gpcode said we’d managed to find a way to restore files in addition to those files that can be restored using the PhotoRec utility.
It turns out that if a user has files that are encrypted by Gpcode and versions of those same files that are unencrypted, then the pairs of files (the encrypted and corresponding unencrypted file) can be used to restore other files on the victim machine. This is the method that the StopGpcode2 tool uses.
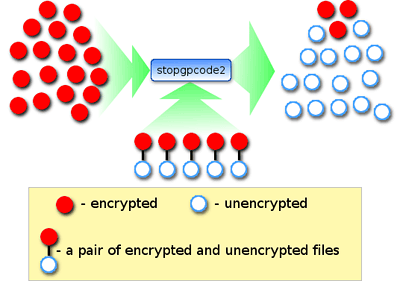
Where can these unencrypted files be found? They may be the result of using PhotoRec. Moreover, these files may be found in a backup storage or on removable media (e.g., the original files of photographs copied to the hard disk of a computer that has been attacked by Gpcode may still be on a camera’s memory card). Unencrypted files may also have been saved somewhere on a network resource (e.g., films or video clips on a public server) that the Gpcode virus has not reached.
We can’t guarantee that files will be restored, as the method used relies not only on the user having unencrypted versions of the affected files but also on the characteristics of the infected machine. All the same, the results we achieved during testing (80% of encrypted files were restored) suggest that it’s worth doing if you need to recover your files.
The more pairs of files that can be found the more data that can be restored.
Detailed instructions on the use of the StopGpcode2 tool can be found in the description of Virus.Win32.Gpcode.ak.





















Another way of restoring files after a Gpcode attack