
There is a new malicious ongoing campaign on Skype. It-s active and kicking yet.
The infection vector is via social engineering abusing infected Skype by sending massive messages to the contacts like these ones:
i don’t think i will ever sleep again after seeing this photo http://www.goo.gl/XXXXX?image=IMG0540250-JPG
tell me what you think of this picture i edited http://www.goo.gl/XXXXX?image=IMG0540250-JPG
Goo.gl short URL service shows that at the moment there are more than 170k clicks on the malicious URL and only 1 hour ago there were around 160k clicks. It means the campaign is quite active with around 10k clicks per hour or with 2.7 clicks per second!
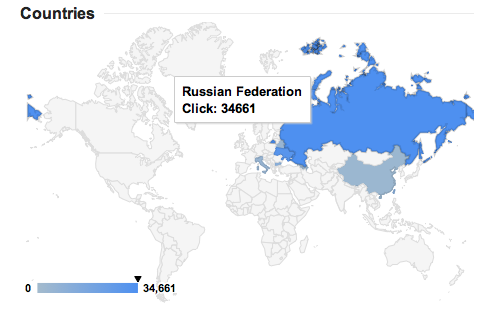
The most of victims come from Russia and Ukraine:
Between other most probably infected countries are: China, Italy, Bulgaria and Taiwan.
The campaign seems to be active since March 1, at least that day the short Google URL was created, however it got strength in the last hours. This graph shows the number of clicks in the last 2 hours:
So far VirusTotal shows 12 of 46 AV detection rate. Kaspersky AV detects the malicious sample by its cloud technology with the verdict UDS:DangerousObject.Multi.Generic
Now few words about malware itself. It-s written in Visual Basic. The subroutines called with human names like Lenka, Pier, Christiane, Ryann, etc. The next expressions are used as part of the social engineering in Skype:
hahaha
Is this you?
Picture of you?
Tell me what you think of this picture
This is the funniest picture ever!
I cant believe I still have this picture
Someone showed me your picture
Your photo isn’t really that great
I love your picture!
What do you think of my new hair?
You look so beautiful on this picture
You should take a look at this picture
Take a look at my new picture please
What you think of this picture?
Should I upload this picture on facebook?
Someone told me it’s your picture
Malware has capabilities to spread via USB too. Malware uses IRC protocol to interact with the C&C as part of the botnet once it-s infected. The string in the sample leading to the VB project file is C:\Users\s\Desktop\Must Use Different Name\HqwKH\avivah.vbp
Finally something interesting is this:
Follow me on twitter @dimitribest
An avalanche in Skype
























C
Can this also spread via the Skype app on android devices?