
This is the fourth and final part of our series of blogposts about the World Cup and the IT threats associated with it. Moreover, these are problems that we face right now, while our soccer stars are strutting their stuff in Brazil.
Many fans have found themselves away from the TV and looking for a live stream of a big game – but looking for live broadcasts on the Internet can cost you money or leave a malicious program on your computer.
When you search on Internet for the live Word Cup broadcast, you will sometimes find purchased advertisements that lead to fraudulent or malicious content. Here are two fresh examples of it, all set up for the World Cup:
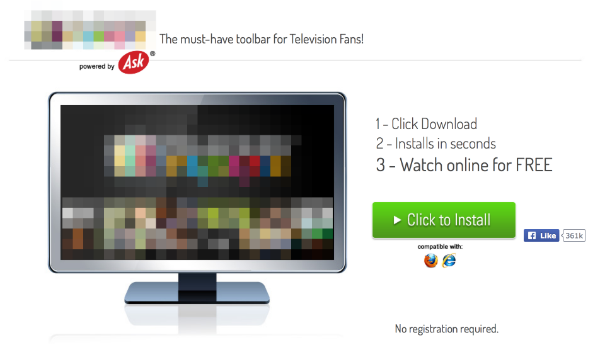
When you go to the Website, it asks you to download a special plugin available for all browsers. This is supposed to be the player needed to watch the on-line broadcast of the games:
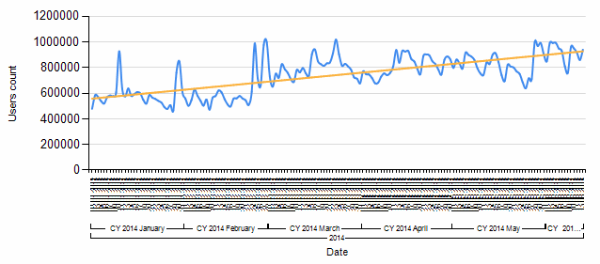
In reality, it is an Adware program, which may not show you anything but will drain your computer’s resources. Adware software straddles a thin line between classic cybercrime and legitimate software. This is why our statistics show the constant detection grow on the same on the user’s devices:
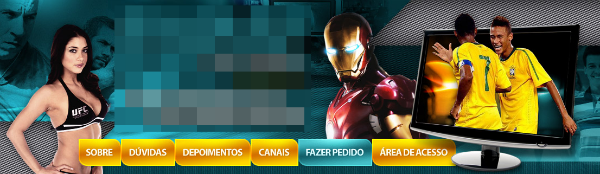
Sites like these also promise to show all the World Cup action:
The sites offer every game, at any time. They promise high quality footage taken from the best cameras in the arenas. Of course, all credit cards are accepted!
However, if you pay, you will just lose your money. Dubious and dishonest websites like these have no interest in playing by any rules.
One last important point is every day we see a lot of new registered domain names containing words like “Fifa Live World Cup steaming 2014”. We believe most of them will be used for a malicious purpose.
Cybercriminals, opportunists and other malicious individuals look for occasions like the World Cup. They know this is the best time to cheat people, stealing their money and infecting their devices. Stay ahead of the game and do not fall into their social engineering traps. Use the best anti-malware protection and keep your wits about you when browsing and looking for the content. By the way, if you want to see a live broadcasting, probably you may use one of these legitimate councils.
You may follow me on twitter: @dimitribest






















Adware or money loss instead of your favorite World Cup game