
The Adobe AIR and Adobe Flash Player Incubator program
updated their Flash Platform runtime beta program to version 5, delivered as Flash Player version 11.2.300.130. It includes a “sandboxed” version of the 32-bit Flash Player they are calling “Protected Mode for Mozilla Firefox on Windows 7 and Windows Vista systems”. It has been over a year since Adobe discussed the Internet Explorer ActiveX Protected Mode version release on their ASSET blog, and the version running on Google Chrome was sandboxed too.
Adobe is building on the successes that they have seen in their Adobe Reader X software. Its sandbox technology has substantially raised the bar for driving up the costs of “offensive research”, resulting in a dearth of Itw exploits on Reader X. As in “none” in 2011. This trend reflects 2011 targeted attack activity that we’ve observed. 2011 APT related attacks nailed outdated versions of Adobe Flash software delivered as “authplay.dll” in Adobe Reader v8.x and v9.x and the general Flash component “NPSWF32.dll” used by older versions of Microsoft Office and other applications. Adobe X just wasn’t hit. IE Protected Mode wasn’t hit. Chrome sandboxed Flash wasn’t hit. If there are incident handlers out there that saw a different story, please let me know.
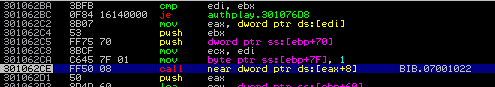
Adobe made and is making substantial investment in their defensive security efforts – they are a part of MAPP, they hired talent that is driving the efforts in the right direction (which is an extremely difficult thing to do in the global corporate software market), they quickly release updates and they are closing holes. Could they do more? I suppose, but the large volume of security effort has been paying off for users of their software that have updated to the most recent versions. Now the problem remains that folks need to upgrade. All too often, people forget that they are running outdated versions of the software, or disabled the software update options of their software. And here is the glaring piece – targeted attackers knew this problem. They hit law firms that didn’t bother to update, they hit directors on boards that think they are too busy or shouldn’t need to know the details of the software on their computers, they hit admin assistants that don’t have admin rights to change the software, they hit targets at organizations that “standardize” on one version or another and roll out patches on their own time. While I won’t provide detailed statistics for attackers’ misuse, unfortunately, Flash continues to be one of the most available vulnerable software packages installed, enabling 2011 APT related results like this:
This latest release helps move defense forward and in the right direction, another big step is getting the software out there upgraded.






















Adobe Incubates Flash Runtime for Firefox