
Last week, Adobe released a patch for a vulnerability in Flash Player that was being exploited in targeted attacks.
Before reading any further, we recommend you to take a moment make sure you apply this patch. Adobe offers this nifty tool to check that you have the latest version of Flash Player.
If you are running Google Chrome, make sure you have version -24.0.1312.57 m- or later.
Now back to CVE-2013-0633, the critical vulnerability that was discovered and reported to Adobe by Kaspersky Lab researchers Sergey Golovanov and Alexander Polyakov. The exploits for CVE-2013-0633 have been observed while monitoring the so-called -legal- surveillance malware created by the Italian company HackingTeam. In this blog, we will describe some of the attacks and the usage of this 0-day to deploy malware from -HackingTeam- marketed as Remote Control System.
HackingTeam and RCS
We previously wrote about RCS (Remote Control System) and HackingTeam and over the past few months, we-ve closely monitored the usage of the RCS (aka as -DaVinci-) against human rights activists and political dissidents from Africa, South America and the Middle East.
We also presented the findings of this investigation last week at Kaspersky Lab-s SAS 2013 in a presentation named ?Cyber Cosa Nostra , which details the connections between HackingTeam with the shady organization known as -OPM-. An article documenting the findings will be published later this month on Securelist.
During our investigation, we discovered several ways through which the RCS malware was installed onto the victims- computers:
1. Self-signed JAR
2. CVE-2012-4167: (0-day from -Vupen-, see
http://www.dhses.ny.gov/ocs/advisories/2012/2012-073.cfm. ~3 months ITW before publishing ). Used with C2: hxxps://www.maile-s.com/yarab/stagedocJord
3. CVE-2010-3333: C2 at hxxps://ar-24.com/0000000031/veryimportant.doc2 + hxxp://rcs-demo.hackingteam.it/0000000001/exploit.doc2
4. CVE-2012-5054: (0-day Vupen, see
http://packetstormsecurity.com/files/116435/Adobe-Flash-Player-Matrix3D-Integer-Overflow-Code-Execution.html. ItW for ~3 months before patching) – used with C2 at: hxxp://176.58.100.37/0000040037/scandale.doc
5. CVE-2012-1682: (0-day. Security Explorations ~2 months ITW before publishing )- hxxp://ar-66.com/installer.jar
6. CVE-2013-0633: 0-day, previously unknown
Some of these infection vectors were previously described in great detail by Citizen Lab Security Researcher Morgan Marquis-Boire, in relation to RCS and also another malware known as ‘SPY_NET’.
Interestingly, from the list above, two of the 0-days appear to have been created by the French offensive security company Vupen. The link was also previously pointed out by Citizen Lab-s report, which says it-s unclear if the exploits used with HackingTeam-s malware have been purchased from Vupen, or just engineered in parallel.
CVE-2013-0633
We came by CVE-2013-0633 while analysing a number of targeted attacks which appeared to be deploying the malware Backdoor.Win64.Korablin.a, which is the Kaspersky detection name for HackingTeam-s -DaVinci- package for Windows (Mac versions is called ?Backdoor.OSX.Morcut ). The attacks employed Word documents which used multiple stages to deliver the malware to the target system.
Although we do not have the original documents used in the attacks, we-ve identified several locations from which the 2nd and 3rd stage were delivered. Here-s a list of command servers which were used as C2 to deliver the exploits, as hardcoded in the shellcode used in the second stage of the attack:
hxxp://li565-84.members.linode.com/0000000097/worddocument.doc3
hxxp://li565-84.members.linode.com/0000000093/worddocument.doc3
hxxp://li565-84.members.linode.com/0000000093/word_document.doc3
hxxp://li565-84.members.linode.com/0000000098/worddocuments.doc3
(a Linode server in Japan)
Previously, we-ve seen attacks using other C2s as well:
|
1 2 3 4 5 6 7 |
76.162.33.13/stagedocsis www.wiki-islam.info/new/stagedocbn ww.faddeha.com/palestine27/stagedocpal wiki-arab.com/index/stagedocwinword ->>>> close[CENSORED].com/7-2012/stage2 (LIVE MALWARE, censored) 192.168.100.100/0000000788/info.doc2 :) 173.255.215.193/napoli/napoli/stage2 |
The malware installed by these exploits is signed with a valid certificate from various entities around the world:
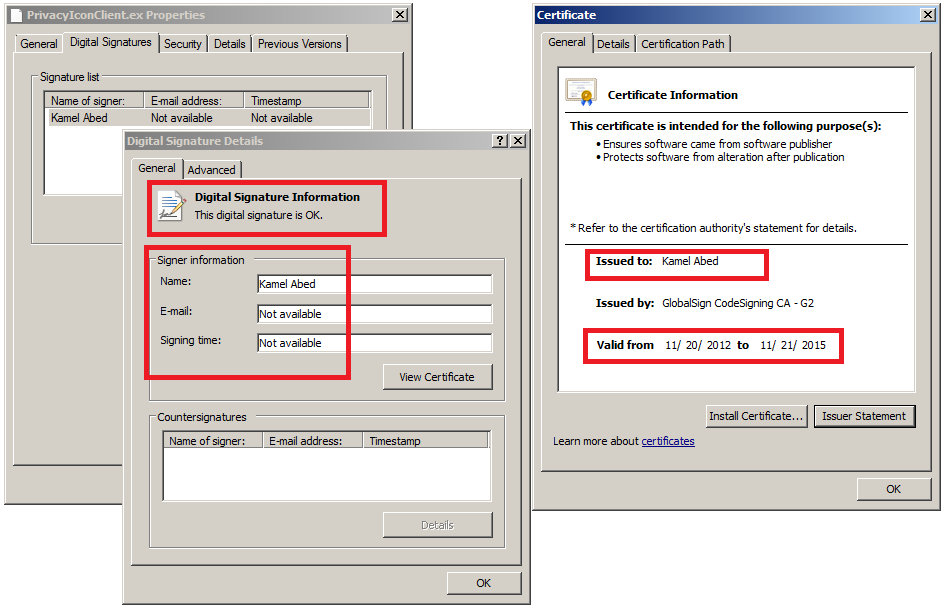
(Digital certificate belonging to ?Kamel Abed used to sign the -RCS- malware dropper)
How widespread are these attacks? Here-s a map of detections for Backdoor.Win32/64.Korablin.a:
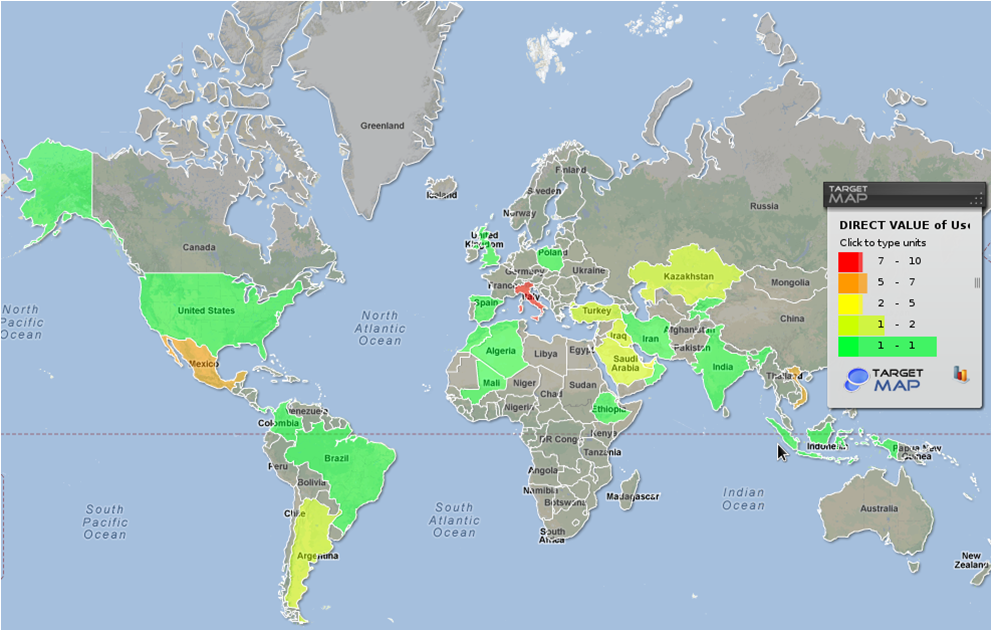
During the monitoring period, we observed about 50 incidents from countries such as Italy, Mexico, Kazakhstan, Saudi Arabia, Turkey, Argentina, Algeria, Mali, Iran, India and Ethiopia.
As it usually happens with such dubious software, it-s impossible to say who uses them and for what purpose. The problem with so-called -legal- spy tools is that any government can purchase them, including governments from countries with a poor human rights records. Additionally, one government can purchase these tools and use them against another country.
The link between HackingTeam and Vupen
During our investigation, we observed at least two 0-days which are credited to Vupen that have been used in attacks with DaVinci/RCS. We do not know if the exploits have been discovered and created in parallel by both teams or if HackingTeam is just one of Vupen-s customers. Nevertheless, it appears there is a link between the two companies in the sense that malware written by HackingTeam is commonly deployed using Vupen 0-days.
The future
Following the publication of Citizen Lab-s blog From Bahrain with Love: FinFisher-s Spykit Exposed, the U.K. government reaffirmed that existing controls restricting the export of cryptographic systems apply to the Gamma Group-s exports of FinSpy.
Although such restrictions exist in the U.K., there is currently little or no information on the regulations in France or Italy regarding the activity of companies that create 0-days and so-called -legal- malware. Even when such regulations exist, the spyware can be easily sold to anyone through umbrella companies in other countries, such as Panama. Based on existing evidence, the victims of such attacks are human rights activists in countries with poor human rights records. It is possible that tools such as FinSpy or RCS lead to the arrest and conviction of people in such countries.
We believe that the ‘legal spy’ industry is the equivalent of a ticking time bomb which can explode at any moment. The lack of regulation, the widespread trading of such dangerous technologies to pretty much anyone who has the money and the fact that they’ve already been in many dubious cases raises a big question about who will be held liable when the bubble finally bursts.
Kaspersky Lab products detect the RCS/DaVinci backdoors as: Backdoor.Win32.Korablin, Backdoor.Win64.Korablin, Backdoor.Multi.Korablin, Rootkit.Win32.Korablin, Rootkit.Win64.Korablin, Rootkit.OSX.Morcut and Trojan.OSX.Morcut.





















Adobe Flash Player 0-day and HackingTeam’s Remote Control System