
A Twitter phishing scheme is spreading its wings, as the previous couple of phishing domains used by this scheme late last week have been taken down. So its operators have decided to put up multiple effective domains. Here are a couple of things to look for.
When you are using a browser like Google Chrome and you are visit twitter.com, the browser displays a green url indicator that the domain has been verified by an extended SSL CA. Now, with the CA breaches that we’ve seen in the past year (the Diginotar breach report was finalized this past week), that may not mean everything. But, in this case, here is how you might verify that you are using the legitimate twitter site:
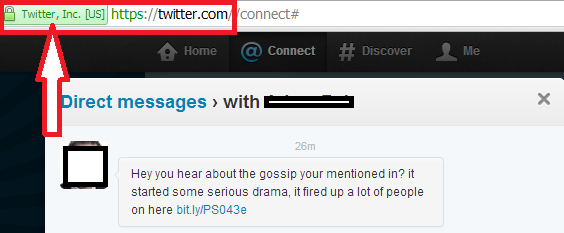
This Direct Message attracts phish with a dramatic notice: “Hey you hear about the gossip your mentioned in? it started some serious drama, it fired up a lot of people on here”. There are a handful of messages in use, as the GFI guys mentioned here last week.
If you were to click on that bit.ly shortened link, your browser will be redirected through a click tracking service:
hXXp://client1.gtisolutions.co.uk/track?type=click=|||hXXp:// tivvtter.com/r1?zcms
And on to the unverified, carefully selected domain. At first glance, this one almost looks like the twitter domain itself:
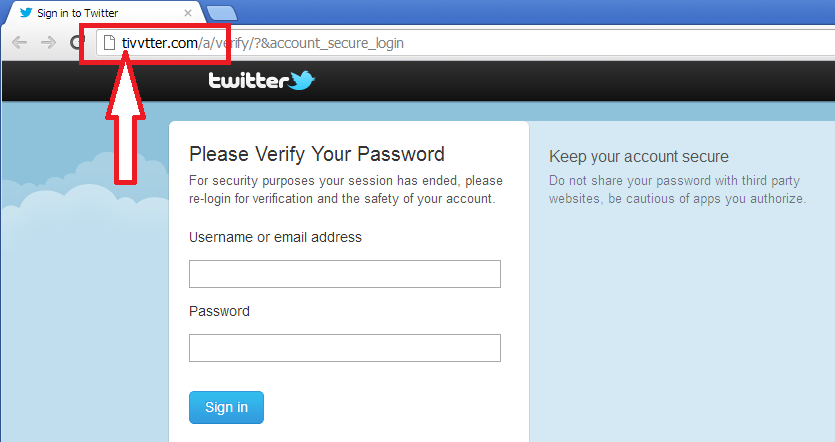
Do not enter your username and password at this site. Also, there are at least a half dozen other domains that look fairly close to “twitter.com”, like this one. These guys are using all of them with the same page and graphics to tempt you into entering your credentials. This theft can be a risk if you re-use your passwords across accounts. Also, there is often other personal information within these twitter accounts, like the user’s email address used to create the Twitter account. So please keep an eye out for this sort of play on word recognition-domains.



















A Quick Look at the Twitter Phish Rotating through Domains