
The ice cream social is a lie
This year’s Blackhat USA briefings were held at the spacious Mandalay Bay, bringing speakers from all over the world to deliver mostly technical cyber-security talks. A number of our researchers were there attending talks and participating in the parallel IOActive and BSides events on Smart Cities cyber-security and “Stealing Food From the Cat’s Mouth”. We even bought a round of drinks for a GReAT happy hour at our booth, thanks for coming by! And on Tuesday night, we announced a public HackerOne-coordinated bug bounty program, setting aside $50,000 for critical vulnerabilities. Blackhat whitepapers, slidedecks, and some source code are being posted to the site.
Talks and speakers that we enjoyed here:
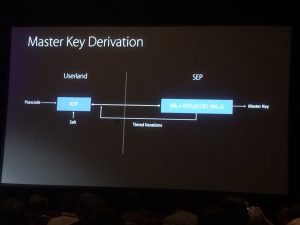
- DEMYSTIFYING THE SECURE ENCLAVE PROCESSOR and BEHIND THE SCENES OF IOS SECURITY
Low level details of Apple iPhone security were presented, both from offensive researchers hacking apart hardware and software, and one of the vendor’s lead security engineers Ivan Krstic. They revealed cryptographic design and implementation details of the secure enclave processor and its OS, the iCloud keychain, and JIT hardening, and pointed out some weaknesses and areas for likely security vulnerabilities in the code.
- CAPTAIN HOOK: PIRATING AVS TO BYPASS EXPLOIT MITIGATIONS
The speakers demonstrated how many AV vendors are performing inline and Kernel to user hooking for exploit mitigation, and how this is being done insecurely. They were able to utilize the mistakes made in the various hooking engines to run malicious code in memory. Their research identified six different types of vulnerabilities in the hooking engines and how to exploit them. Essentially, most of the vulnerabilities boiled down to improper handling of permissions on created memory blocks by the AV engines.
- ADVANCED CAN INJECTION TECHNIQUES FOR VEHICLE NETWORKS
As always, Charlie and Chris delivered a fantastic talk on the next step in their research; targeting CAN to manipulate vehicle behaviors while driving at high speeds. While their research was done hard wired into the car, they stated that if another remote vulnerability were discovered, these attacks would be plausible remotely, not requiring physical access. They showed how they were able to manipulate various vehicles to apply the emergency brake, turn off the power steering module, control the steering, etc, all while driving at a high speed. They had to essentially bypass security measures which don’t normally allow diagnostic mode to be invoked while the car is on or in motion. In normal Charlie and Chris fashion, the talk was full of funny videos of their exploits, one of which showed them crashing their Jeep into a ditch in a cornfield and subsequently having to be rescued by some locals. 🙂
A few GReAT researchers were caricatured by an artist at our Kaspersky Lab booth, next to our Kaspersky Anti-Targeted Attack demo. The artist was good!
Defcon’s challenge badges ran out in record time this year at under 60 minutes! The conference is going on now at Paris and Bally’s. See you next year!























Blackhat USA 2016