
Spam: quarterly highlights
Delivery service Trojans
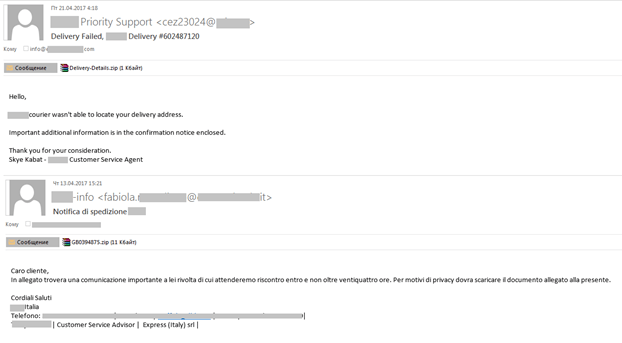
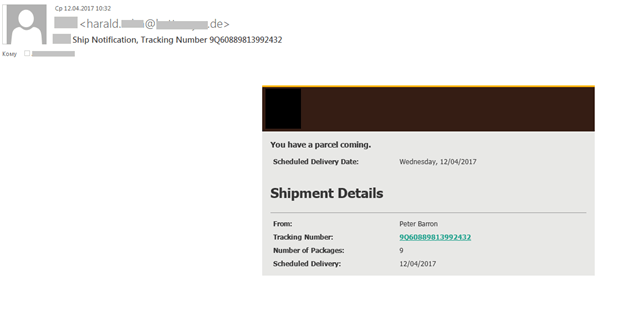
At the start of Q2 2017, we registered a wave of malicious mailings imitating notifications from well-known delivery services. Trojan downloaders were sent out in ZIP archives, and after being launched they downloaded other malware – Backdoor.Win32.Androm and Trojan.Win32.Kovter. The usual trick of presenting dangerous content as important delivery information was employed by the fraudsters to make recipients open the attachment. The malicious mailings targeted people from different countries and came in a variety of languages.
These fake notifications from delivery services also included malicious links to infect the victim’s computer and steal personal information. The fraudulent link was tied to the tracking number of a non-existent shipment and used the following format:
Http: // domain / name of delivery service __com__WebTracking__tracknum__4MH38630431475701
The domain and the sequence of letters and numbers at the end of the link varied within the same mass mailing.
After a user clicked on the link, the Js.Downloader family Trojan was downloaded, which in turn downloaded the banking Trojan Emotet. This malware was first detected in June 2014, and is still used to steal personal financial information, logins and passwords from other services, as well as to send spam, etc.
WannaCry in spam
In May 2017, hundreds of thousands of computers worldwide were infected by the WannaCry ransomware. While the majority of similar ransomware samples require some sort of user input before a computer is infected, WannaCry could do so without any user actions. It attacks the target using a Windows exploit and then infects all computers within the local network. Like other ransomware of this type, WannaCry encrypts files on the victim’s computer and demands a ransom for decryption. In these attacks, files are encrypted with the extension .wcry and become unreadable.
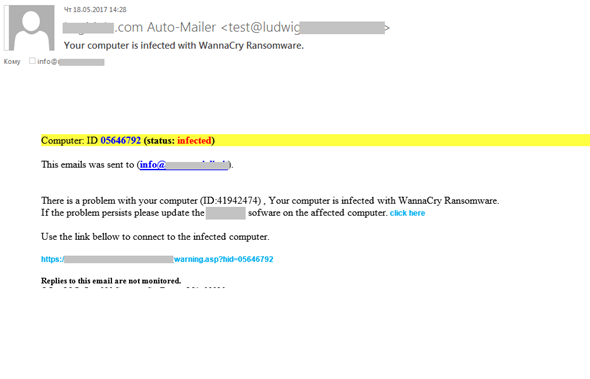
The media frenzy surrounding the WannaCry ransomware played into spammers’ hands, as all high-profile events usually do. For example, they distributed numerous offers of services to counter the new malware, to prevent infection, training for users, etc. Scammers who earn money via fraudulent mailings also took advantage.
They sent out fake notifications on behalf of well-known software vendors informing recipients that their computers had been infected with ransomware and had to be updated. The link to the supposed update, of course, led to a phishing page. We came across emails that showed the attackers hadn’t taken much care when compiling their mailings, obviously hoping their victims would be in too much of a panic to notice some obvious mistakes (sender’s address, URLs, etc.).
Malware in password-protected archives and the corporate sector
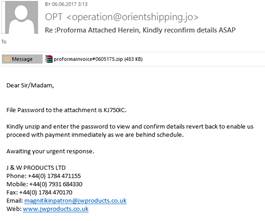
In the second quarter of 2017, we came across new mailings containing malicious attachments in a password-protected archive. They were obviously targeting the corporate sector.
As a rule, the distribution of password-protected archives serves two purposes. First, it is a form of social engineering, with the attackers emphasizing that all confidential data (such as business accounts) is additionally protected by a password. Second, until the files are extracted from the archive, they cannot be fully checked by antivirus software.

These archives contained a malicious program belonging to the Pony/FareIT family. This malware is designed to steal logins and passwords to web services stored in browsers, the URLs on which they were entered, authentication data to FTP servers, file managers, mail clients, synchronization applications, as well as crypto-currency wallets.

This archive contains a malicious program called Trojan-Downloader.MSWord.Agent.bkt, which is a password-protected Microsoft Word file. The document contains a malicious script that downloads other malicious software designed to steal bank data to the user’s computer.
It is worth noting that the tendency to mask malicious mailings as business correspondence has increased. Spammers are now not only copying the style of business emails – they often use the actual details of real companies, copy auto-signatures and logos, and even the subject of the messages can correspond to the company profile. Judging by the domain addresses in the ‘To’ field and by the content of the emails, these mailings also target the B2B sector.
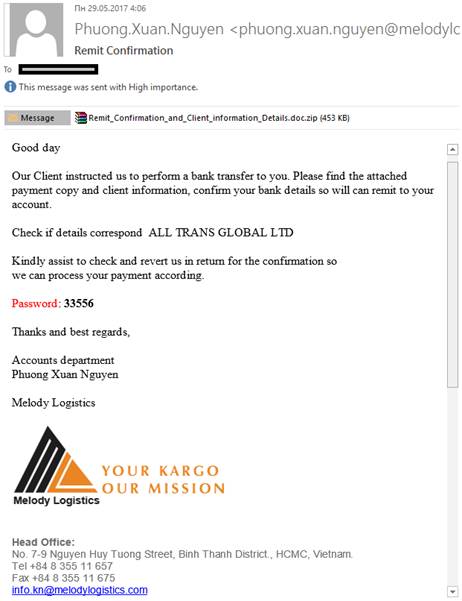
This archive contained a malicious program belonging to the Loki Bot family designed to steal passwords from FTP, mail clients and passwords stored in browsers, as well as crypto-currency wallets.

This archive contains the Exploit.Win32.BypassUAC.bwc malicious program, designed to steal passwords for network resources and email clients. To elevate privilege, the malware uses an exploit that bypasses the protection of the Microsoft Windows UAC component. During the operation it uses legitimate utilities to restore passwords.

This archive contains an XLS-file with a macro that was used to download HawkEye Keylogger to the victim’s computer. This malicious program written in .NET intercepts keystrokes and collects information about the system where it operates: internal and external IP addresses, the OS version as well as the name of the security product and the firewall.
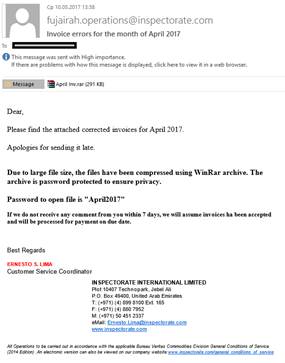
This archive contains two malicious files: EXE, disguised as PDF (detected as Trojan.Win32.VBKrypt.xdps) and an MSWord document with an exploit that uses the CVE-2017-0199 vulnerability. Both malicious programs download a modification of Zeus to the victim’s computer.
Such targeted attacks can have different aims. In the case of ransomware, it is obvious that a company’s intellectual property can be viewed as being much more valuable than the information on a private computer, so a potential victim is more likely to pay the necessary bitcoins to get it back. In the case of spyware designed to steal financial information, fraudsters can potentially hit the jackpot once they get access to a company’s accounts.
Spyware in the B2B sector can also be used in more sophisticated schemes of financial fraud, including MITM attacks during financial transactions. One such scheme disclosed by our colleagues is described here.
Interestingly, although the payload downloaded on the victim’s computer is very different, its main function is the theft of authentication data, which means that most attacks on the corporate sector have financial goals.
We shouldn’t forget about the potentially dangerous situation where an attacker gains access to a corporate network and gets control of industrial equipment.
Overall in the second quarter of 2017, the percentage of spam in email traffic grew slightly from the previous quarter. The number of email antivirus detections increased by 17% in Q2 vs. Q1.
Necurs botnet continues to distribute spam
The Necurs botnet continues to distribute spam, although the volumes are much smaller than in 2016. This botnet operation is characterized by alternating periods of low and high activity, when we register up to 2 million emails a day sent to Kaspersky Lab customers. In addition to malicious mailings from the botnet, Necurs actively spreads pump-and-dump as well as dating spam:
Malicious emails from the Necurs botnet are usually concise, contain files with DOC, PDF or other extensions. Sometimes, instead of attachments, emails include links to cloud storages such as Dropbox from where malicious files are downloaded.
Spam via legal services
Last quarter we wrote that in order to bypass filters, spammers often spread advertising and fraudulent offers via legitimate means. They include, for example, the ‘Invite friends’ field on social networking sites, notifications about comments that are usually sent to the recipient’s email address, or any other method available on the various sites that allow the sending of emails to a user’s list of trusted addresses. In addition, this type of spam is more difficult to detect because the source is legitimate. Spammers also like it because this type of resource makes for easy targeting. For example, they exploit job search sites to publicize easy earnings or for financial fraud:
Domain fraud
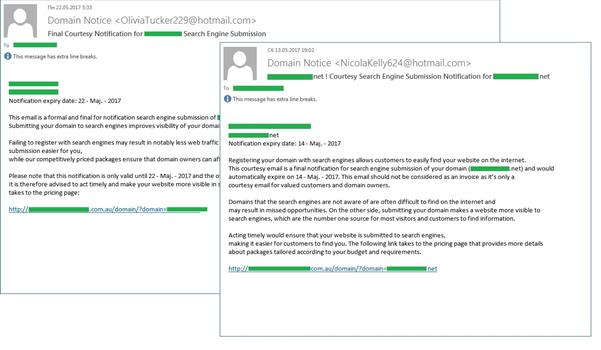
Last quarter we discovered several different mass mailings related to the domain fraud.
One of the mailings was sent in the name of a major company involved in the registration of domain names and addressed the administrators of registered domains. They were informed that it was necessary to activate a domain to confirm their administrator status and ability to manage the domain. These measures were allegedly taken in accordance with the amendments made to regulations by ICANN (Internet Corporation for Assigned Names and Numbers).
To do this, the administrator was told they had a limited time to create a PHP file with specific content in the root directory of the site. The email also stated that failure to observe these conditions would mean the confirmation procedure had not been completed and support for the domain would be suspended.
If the script is launched on the victim’s site, the attackers would be able to gain control of the site and to run any code. In addition, the script makes it possible to collect all user data entered on the site where it is registered and run. The fact that many of these fake emails were sent to addresses belonging to banks, means we can assume that the scammers wanted to collect data entered on the website of those banks, including the logins and passwords used for Internet banking.
Administrators also found themselves the target of yet another type of domain fraud. It involved the administrator of an organization receiving an email prompting them to register their domain with search engines to help potential customers find the company on the Internet. These messages came from addresses generated on free hosting.
This service was provided on a fee basis. In order to see the list of tariffs, the recipient was asked to click a link in the email that was “hosted” on a legitimate website. After choosing a tariff, the user had to fill in and send a form that asked for detailed personal information, including credit card information.
Statistics
Proportion of spam in email traffic
In Q2 2017, the largest percentage of spam – 57.99% – was registered in April. The average share of spam in global email traffic for the second quarter amounted to 56.97%, which was 1.07 p.p. more than in the previous quarter.
Sources of spam by country
The second quarter of 2017 saw a change in the top three sources of spam. Vietnam came first, accounting for 12.37% of world spam. It was followed by the previous quarter’s leader the US, whose share dropped by 8.65 p.p. and accounted for 10.1%. China (8.96%, +1.19 p.p.) completed the top three.
India was the fourth biggest source, responsible for 8.77% (+3.61 p.p.) of total spam, followed by Germany (5.06%, -0.31 p.p.).
Russia, in sixth place, accounted for 4.99%, which is only 0.06 p.p. less than in the previous quarter.
The top 10 biggest sources also included Brazil (4.47%), France (4.35%), Iran (2.49%), and the Netherlands with a share of 1.96%.
Spam email size
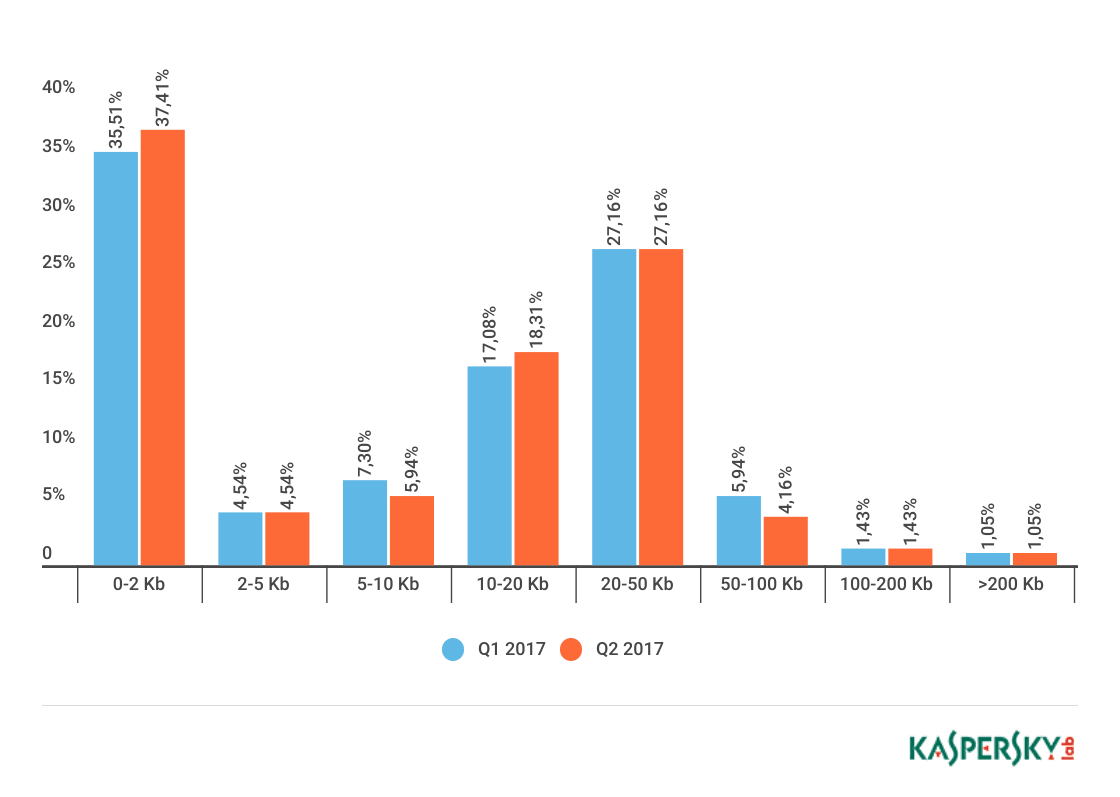
In Q2 2017, the share of small emails (up to 2 KB) in spam traffic changed only slightly and averaged 37.41%, which is 1.9 p.p. more than in the first quarter. The proportion of emails sized 2–5 KB remained at the same level: 4.54%; and those of 5–10 KB (7.83%) declined by 1.36 p.p. and accounted for 5.94%.
The proportion of emails sized 10-20 KB reached 18.31% and emails of 20-50 KB — 27.16%. The proportion of more emails sized 100 KB+ was slightly more than 2%.
Malicious attachments in email
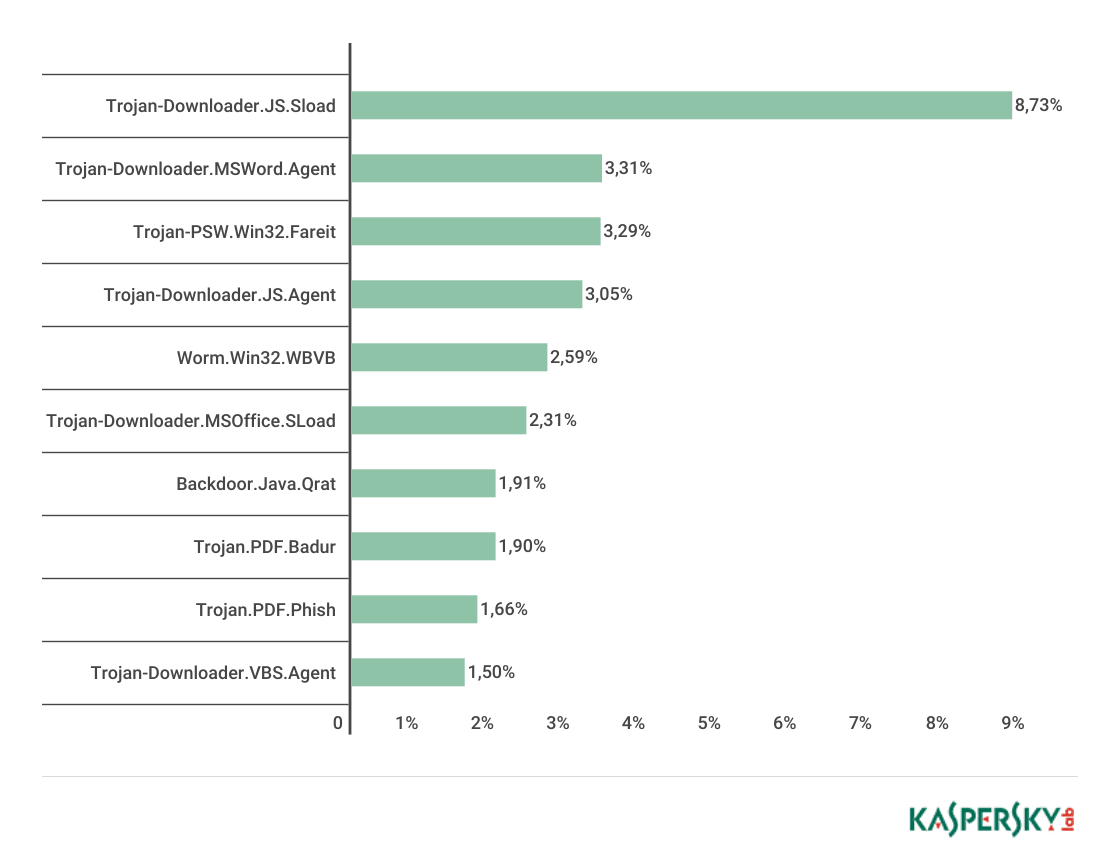
Top 10 malware families
Trojan-Downloader.JS.SLoad (8.73%) topped the rating of the most popular malware families. Trojan-Downloader.JS.Agent (3.31%) came second, while Trojan-PSW.Win32.Fareit (3.29%) rounded off the top three.
Trojan-Downloader.JS.Agent (3.05%) came fourth followed by Worm.Win32.WBVB (2.59%).
Newcomers to the top 10, Backdoor.Java.QRat (1.91%) and Trojan.PDF.Phish (1.66%), occupied seventh and ninth places respectively.
The Backdoor.Java.QRat family is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is typically distributed via email as a JAR attachment.
Trojan.PDF.Phish is a PDF document containing a link to a phishing site where users are prompted to enter their login and password for a specific service.
Countries targeted by malicious mailshots
Germany (12.71%) was the country targeted most by malicious mailshots in Q2 2017. China, last quarter’s leader, came second (12.09%), followed by the UK (9.11%).
Japan (5.87%) was fourth, with Russia occupying fifth with a share of 5.67%. Next came Brazil (4.99%), Italy (3.96%), Vietnam (3.06%) and France (2.81%).
The US (2.31%) completed the top 10.
Phishing
In the second quarter of 2017, the Anti-Phishing system prevented 46,557,343 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017.
Geography of attacks
In Q2 2017, Brazil (18.09%) was the country where the largest percentage of users was affected by phishing attacks, although its share decreased by 1.07 p.p. compared to the previous quarter.
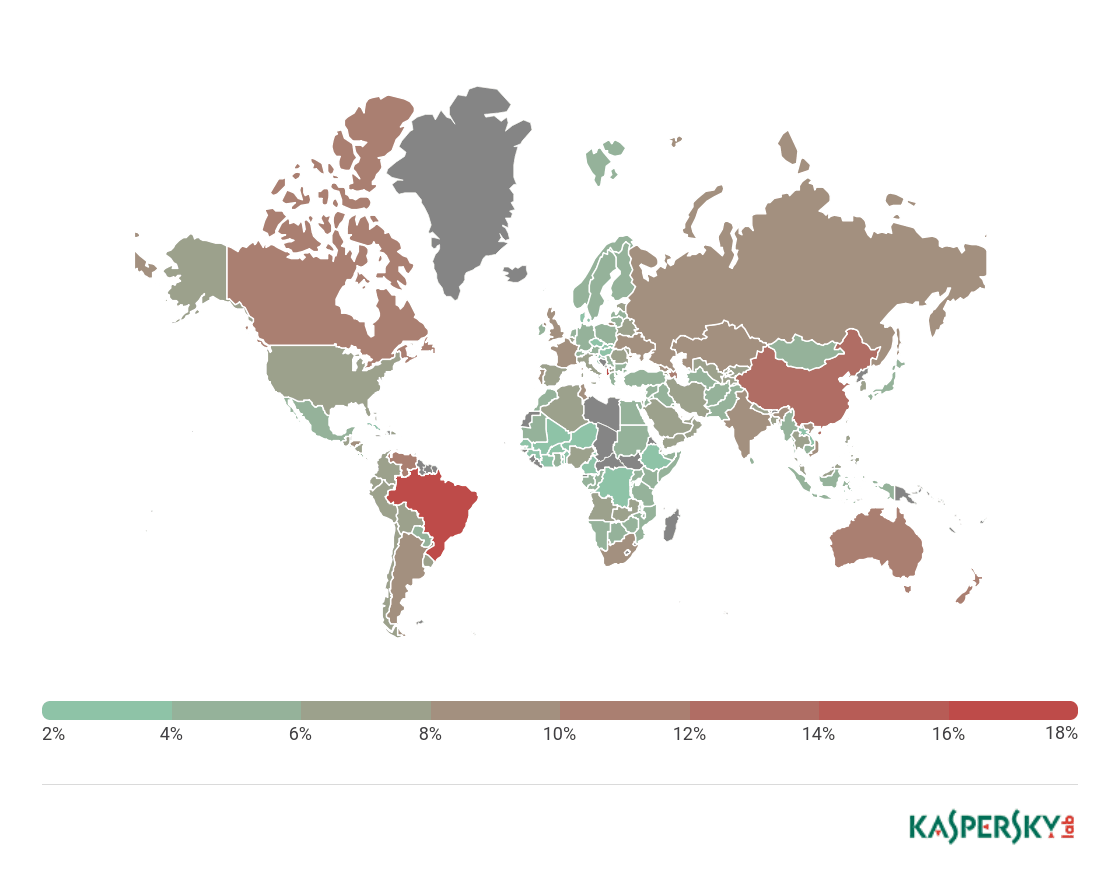
Geography of phishing attacks*, Q2 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
The percentage of users attacked in China decreased by 7.24 p.p. and amounted to 12.85%, placing the country second in this ranking. Australia added 1.96 p.p. to the previous quarter’s figure and came third with 12.69%. The percentage of attacked users in New Zealand increased to 12.06% (+ 0.12p.p.), with Azerbaijan (11.48%) in fifth. The Republic of South Africa (9.38%), Argentina (9.35%) and the UK (9.29%) rounded off this top 10.
In the second quarter, Russia (8.74%) exited this top 10 of countries with the largest percentage of users affected by phishing attacks, falling to 18th place.
| Brazil | 18.09% |
| China | 12.85% |
| Australia | 12.69% |
| New Zealand | 12.06% |
| Azerbaijan | 11.48% |
| Canada | 11.28% |
| Qatar | 10. 68% |
| Venezuela | 10.56% |
| South Africa | 9.38% |
| Argentina | 9.35% |
| UK | 9.29% |
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q2 2017, the Banks (23.49%, -2.33 p.p.), Payment systems (18.40%, +4.8 p.p.) and Online stores (9.58%, -1.31 p.p.) categories accounted for more than half (51.47%) of all registered attacks.

Distribution of organizations affected by phishing attacks by category, Q2 2017
Hot topics this quarter
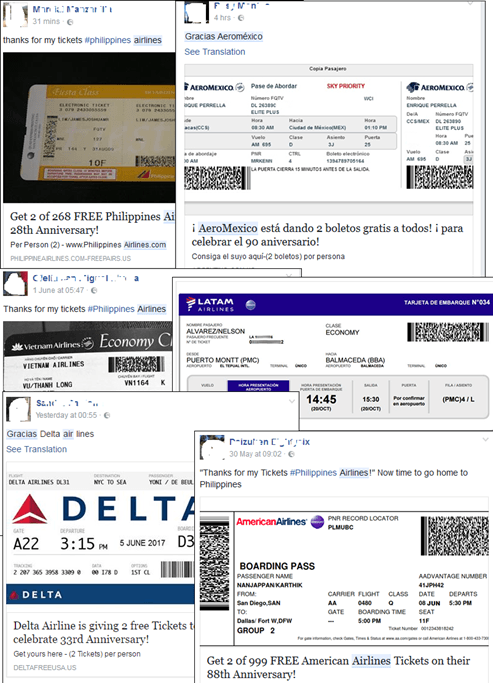
Airline tickets
In the second quarter of 2017, Facebook was hit with a wave of posts that falsely claimed that major airlines were giving away tickets for free. Naturally, there were no promotions giving away airline tickets: fraudsters had created a number of sites on which users were congratulated on winning an air ticket and were asked to perform a series of actions to receive their prize. First, the victims were asked to post the promotional information on their Facebook page. Secondly, the victims had to click the “Like” button. After performing all the necessary actions, the website redirected the user to a resource promoted by the fraudsters. The content of these pages varied – from harmless ads to malicious software.
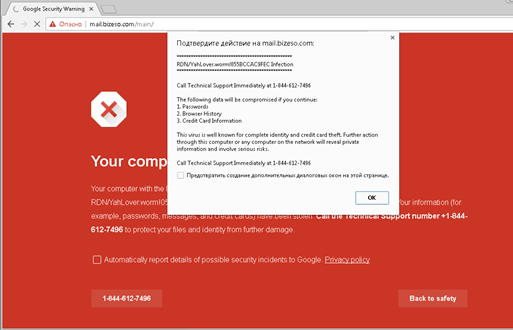
False browser blocking
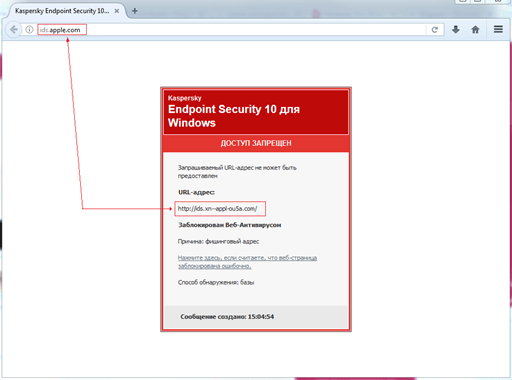
Almost all the popular browsers have built-in protection against web threats. When entering a malicious or phishing page, they often warn the user of the potential dangers and recommend not visiting it.
Fraudsters also make use this protection measure for their own purposes and distract the victim with warnings. For example, they simulate the Chrome blocking page. A user who has ever seen this warning from the browser is more likely to trust the page and follow the criminals’ prompts.
The main danger of these pages is that careful examination of the address bar doesn’t help – a browser warning usually “pops up” on untrusted web resources.
However, they may also appear when trying to enter a domain belonging to companies that act as a hosting service. And it is precisely such warnings that cause the victims to have greater trust in them:
As a rule, when a user calls the numbers specified, the fraudsters pretend to be a support service, tricking victims into paying for services they allegedly need.
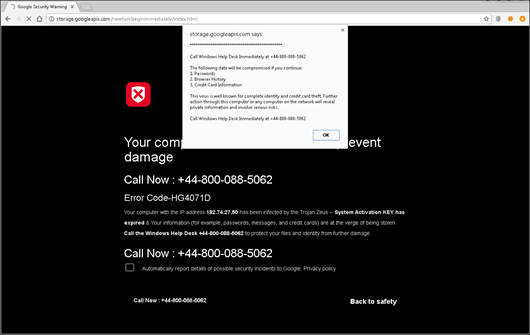
Punycode encoding
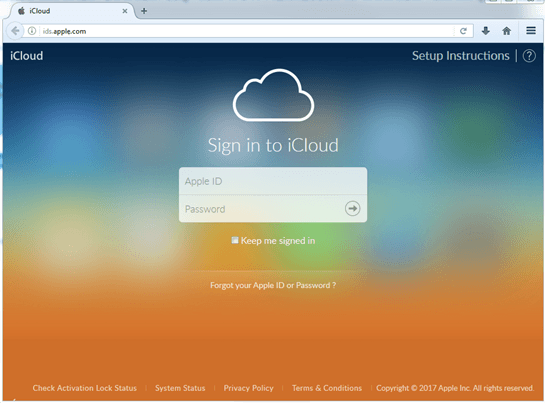
Close examination of the address bar may not help if the phishers use non-Latin characters that are similar to Latin letters to create domain names that are almost identical to the names of popular web resources. Web browsers use Punycode to represent Unicode characters in a URL. However, if all the characters in the domain name belong to the character set of one language, the browser will display them in the language specified rather than in Punycode.
The screenshot of the phishing page below demonstrates this technique.
Sometimes on closer examination, you can see inconsistencies, for example, like the dot under the letter ‘e’.
Have a look at the banner of the blocking site: it displays a URL in Punycode. However, it differs from what we see in the browser. This address is definitely not a domain owned by a well-known company.
Technically, the address is completely different from the original one. Moreover, phishers have used different encodings in the names of pages before. However, for ordinary users, recognizing this type of phishing can be a problem.
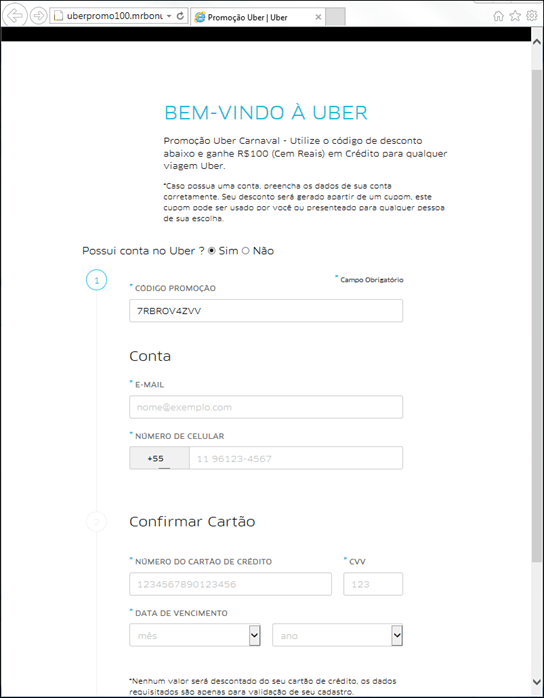
Attacks on Uber users
One of Q2’s high-profile news stories was an attack on Uber users. Phishing pages were distributed via spam mailings; recipients were offered a large discount if they completed a “registration” form, where in addition to personal data they had to enter their bank card information. After completing the questionnaire, the user was redirected to the legitimate site of the company.
Because Uber often holds promotions and offers discounts, users are less inclined to doubt the authenticity of the offer.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies.
| Organization | % of detected phishing links |
| 8.33 | |
| Microsoft Corporation | 8.22 |
| Yahoo! | 8.01 |
For the third quarter in a row the top three organizations attacked most often by phishers remained unchanged. In Q1, Yahoo! was the organization whose brand was mentioned most often on phishing pages. However, in the second quarter it dropped to third, giving way to Facebook (8.33%) and Microsoft (8.22%).
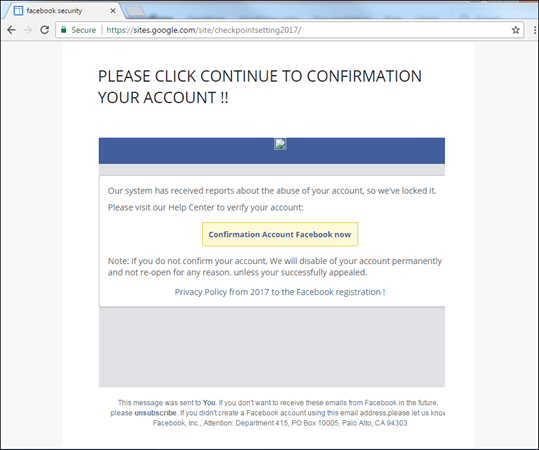
One of the phishers’ tricks is to place pages of popular organizations on domains belonging to other popular organizations. In the example below, a link to a free hosting service is shown, and while not all users will know what this is, mentioning Google is more likely to make them think it’s genuine.
The actual data form is usually located on another domain, where a user ends up after clicking on the button.
Conclusion
In Q2 2017, the average share of spam in global email traffic amounted to 56.97%, which was only 1.07 p.p. more than in the previous quarter. One of the most notable events of this quarter – the WannaCry epidemic – did not go unnoticed by spammers: numerous mass mailings contained offers of assistance in combating the ransomware, as well as various workshops and training for users.
In the second quarter, the most popular malware family was the JS.SLoad (8.73%), with another downloader, MSWord.Agent, in second (3.31%). The Fareit Trojan family (3.29%) rounded off the top three.
The Anti-Phishing system prevented over 46.5 million attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017. Noticeably, in their earlier attacks, fraudsters counted on user carelessness and low levels of Internet literacy. However, as users are becoming more cyber savvy, phishers have had to come up with new tricks, such as placing phishing pages on domains owned by well-known organizations.





























Spam and phishing in Q2 2017