
It’s been a while since Nigerian spam, aka 419 scam emails, came only from Nigeria. Spammers use every method they can to hook trusting users – they’re ready to make use of any region or country which is perceived as being corrupt or volatile in any way.
At the end of March, spam analysts at Kaspersky Lab encountered a mass mailing of 419 messages, which traditionally include a request for help in transferring funds, or cashing assets in return for a substantial percentage of the overall sum mentioned. In this case, the scammers are going under the guise of a Russian financial analyst. Of course, this analyst doesn’t actually exist. And any user who thinks that s/he’ll be able to make an easy profit by contacting the scammers is mistaken – s/he is very very unlikely to receive the promised sum and is more likely to find his/ her bank account emptied.
This is a typical 419 scam. However, it has a couple of interesting points:
- The Russian theme – this is rare in 419 spam, and it’s the first ‘Russian’ message we’ve seen since a wave of 419 messages purporting to be from the wife/ lover/ secretary of Khodorkovsky, the jailed former CEO of Yukos.
- The relatively small sum offered by the alleged sender – normally, 419 scammers mentions millions or even billions of dollars, with the recipient being offered 20 – 25% of the overall sum in return for help.
This may well be a calculated new approach on the part of the spammers. Most, if not all, users have already wised up to such scams, and understand that the promise of untold riches is just that – an empty promise. This proposal is more firmly rooted in the real world, and might make some users think it could be genuine.
But let’s call things by their real names. This is a 419 scam, no doubt about it – it just takes a slightly different approach.

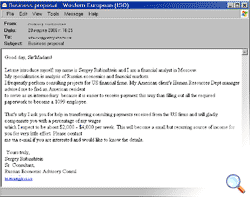



















419s – from Russia with love