
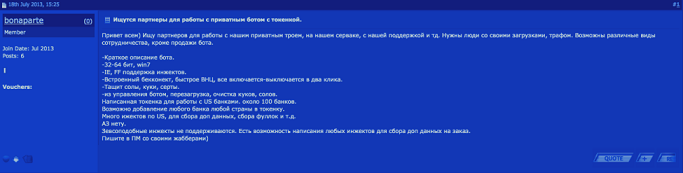
On July 18, 2013, the following post was published on a closed cybercriminal forum:
The author of this post was offering a malicious program that could be used to attack “about 100 banks” by seeding add-on code onto bank websites viewed with Internet Explorer and Mozilla Firefox, with VNC connections, and other ways to attack “any bank in any country.”
Kaspersky Lab immediately began to dig deeper, and discovered that the program the malicious users were offering was Trojan-Banker.Win32/64.Neverquest. By mid-November Kaspersky Lab had recorded several thousand attempted Neverquest infections all around the world. This threat is relatively new, and cybercriminals still aren’t using it to its full capacity. In light of Neverquest’s self-replication capabilities, the number of users attacked could increase considerably over a short period of time.
An analysis of executable files
| executable md5 | Compilation date |
| 0eb690560deb40bec1a5a9f147773d43 | Thu Sep 05 12:33:35 2013 |
| 212a7ef73af17a131bb02aa704aa1b14 | Thu Aug 29 15:30:01 2013 |
| 2a9e32e488c3e6d5ba8dc829f88ba31b | Fri Aug 23 12:10:14 2013 |
| 385509d00c7f652689a13df0c4142a91 | Sat Oct 28 05:37:40 2000 |
| 5c6f1704632afbbaa925fa71ebc2f348 | Wed Aug 28 10:22:16 2013 |
| 61720b34825e28e05c6a85a20dd908c9 | Mon Sep 02 16:41:05 2013 |
| 79da4f9675b87d261cb1b9cb9c47e70a | Mon Aug 26 14:35:00 2013 |
| 808b13ebae56569db0f7f243fab9e9ed | Wed Sep 04 10:50:18 2013 |
| 8e918b0f0643b1e6a7ae1ebf8fbaaec7 | Thu Sep 05 12:50:17 2013 |
| a22cf98fb397b537de0f9c9f4263b6a5 | Mon Sep 11 02:47:52 2000 |
| b26578721c11bf387ed72b02c1237ed7 | Fri Sep 06 21:40:39 2013 |
| b76628896fb602d02abbcc118a704d30 | Thu Aug 29 15:30:24 2013 |
| c0244295fc0cb98c938bb39bbada2e61 | Wed Aug 14 09:30:45 2013 |
| dd12ec2f1cd96bc8677934abb6a545b0 | Fri Sep 06 21:40:39 2013 |
| fd3231ab2f7829659c471b7369808fab | Tue Aug 27 09:38:43 2013 |
| ffad56a2b4693d98e31ad8c4be86d055 | Wed Sep 04 13:13:45 2013 |
A table of executable md5s for Trojan-Banker.Win32/64.Neverquest with their compilation dates
This program’s primary function is contained in a dynamic library installed onto a system using an additional program, such as a Trojan Downloader or a Trojan Dropper. These types of programs install the library file in the %appdata% folder under a random name with a .DAT extension (for example: qevcxcw.dat). This library runs automatically due to “regsvr32.exe /s [path to library]” being added to the registry under “SoftwareMicrosoftWindowsCurrentVersionRun.” After that, the program begins its only export from this library, initializing the malicious program.
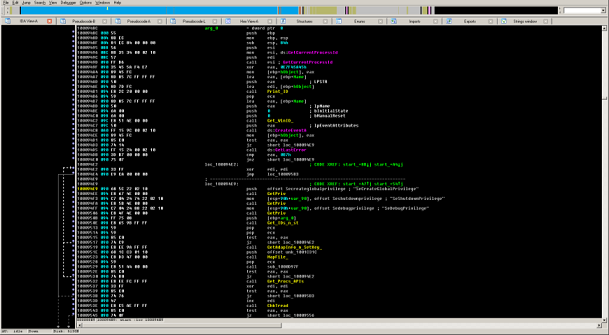
Neverquest’s initial code, disassembled
The program checks the computer for any copies of itself that may already be installed on the computer. If there aren’t any, it then launches a VNC server and sends its first request to the command center in order to receive a configuration file.
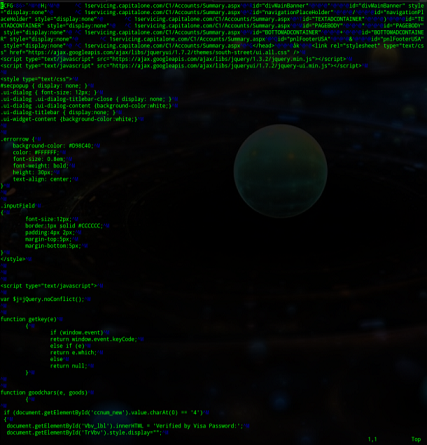
Neverquest’s configuration file
The configuration file is encrypted with a key packed by an aPLib library compression and then transmitted to the command center.
The configuration file contains a set of malicious JavaScripts and a list of websites that, when launched in IE or Firefox, will install the corresponding scripts.
There are 28 sites on the list, including those that belong to large international banks – sites of German, Italian, Turkish and Indian banks, as well as payment systems.
When a user on an infected machine visits one of the sites on the list, the malware controls the browser’s connection with the server. Malicious users can obtain usernames and passwords entered by the user, and modify webpage content. All of the data entered by the user will be entered onto the modified webpage and transmitted to malicious users.
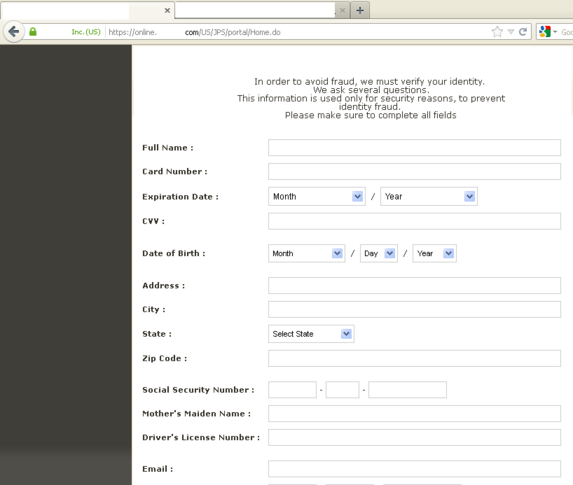
A webpage seeded with malicious content. All data that the user enters on this page will be transmitted to malicious users.
After gaining access to a user’s account with an online banking system, cybercriminals use a SOCKS server and connect remotely to the infected computer via a VNC server, then conduct transactions and wire money from the user to their own accounts, or – in order to keep the trail from leading directly to them – to the accounts of other victims.
Another function helps malicious users replenish their list of targeted banks and develop code to be seeded on new websites that were previously not on the target list. This is done as follows:
- The configuration file contains a list of key words that, if they are found on a webpage in the browser, prompt the malicious program to intercept the process and send the full contents of the webpage and its URL to malicious users.
- Based on that received data, the malicious users then develop additional code to be seeded onto that website:
- The new website is then included on the list of targeted websites, and the new code is added to the arsenal of malicious scripts in the configuration file.
- The updated configuration file is then distributed to all infected computers.
The list of key words used to develop additional seeding code is:
|
|
|
Of all of the sites targeted by this particular program, fidelity.com – owned by Fidelity Investments – appears to be the top target. This company is one of the largest mutual investment fund firms in the world. Its website offers clients a long list of ways to manage their finances online. This gives malicious users the chance to not only transfer cash funds to their own accounts, but also to play the stock market, using the accounts and the money of Neverquest victims.
Prevalence
In 2009, Kaspersky Lab detected a threat related to a new way of spreading malware. This malicious program was dubbed Bredolab, spread by the Pegel botnet. This program’s distribution methods were so successful that in early 2010 it ranked among the Top 3 most widespread malware on the Internet. Neverquest uses the same self-replication mechanisms as Bredolab.
Neverquest’s features include a collection of data used to access FTP servers via the following programs:
| Far | Far2 | CuteFTP | Ipswitch | FlashFXP |
| BulletProof FTP | SmartFTP | TurboFTP | FTP Explorer | Frigate3 |
| SecureFX | FTPRush | BitKinex | NetDrive | LeechFTP |
| FTPGetter | ALFTP | GlobalDownloader | Notepad++ | FTPInfo |
| NovaFTP | FTPVoyager | WinFTP | DeluxeFTP | Staff-FTP |
| FreshFTP | BlazeFtp | GoFTP | 3D-FTP | EasyFTP |
| FTPNow | FTP Now | FTPShell | NexusFile | FastStoneBrowser |
| FTP Navigator | FTP Commander | FFFTP | COREFTP | WebSitePublisher |
| ClassicFTP | Fling | FTPClient | WebDrive | LinasFTP |
| PuTTY | LeapFTP | WindowsCommander | TotalCommander | FileZilla |
| ExpanDrive | AceBIT | Robo-FTP | WinZip | Firefox |
| Thunderbird | InternetExplorer |
A table of programs used to access FTP servers targeted by Neverquest
The data stolen from these programs is then used by the cybercriminals to further distribute the malicious program using the Neutrino exploit pack, which is described by our colleagues here.
This malicious program also steals data from the user’s email clients and harvests data during SMTP/POP sessions. This data is used by cybercriminals to send out mass spam mailings with attachments containing Trojan Downloaders, which then install Neverquest. These emails are typically designed to look like official notifications from a variety of services. The names of the malicious attachments could be any of the following:
- travel-00034.jpg. zip
- travel-00034.sg.67330-2-2-8.jpg.zip
- jpg.zip
- light details_united airlines.pdf.zip
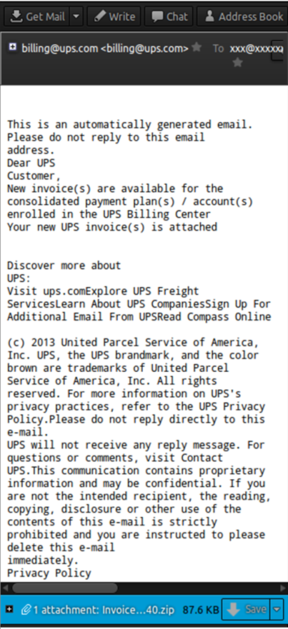
An example of a spam email containing a Trojan Downloader that will install Neverquest
Neverquest is also designed to harvest data to access the accounts on a number of popular social services:
|
|
|
Kaspersky Lab was not able to detect the proliferation of this particular malicious program via these services, although there is nothing that would prevent them from doing so.
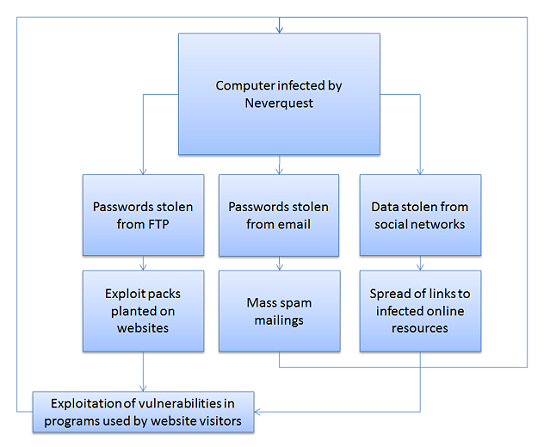
The flowchart below illustrates how Neverquest spreads:
Conclusion
Neverquest supports just about every possible trick described in our previous article on online bank attacks: web injection, remote system access, social engineering, and so on.
The following modules are built into Neverquest:
- A module that steals data entered by users on online bank websites. Data is stolen from IE and Firefox browsers.
- A module that seeds code onto banking websites when launched in IE or Firefox. Malicious JavaScript is downloaded into the code of the webpage to be targeted by the Trojan.
- A VNC server: this provides malicious users with remote connections to conduct fraudulent transactions.
- An FTP password harvester. Stolen data is used by cybercriminals to plant exploit packs onto servers owned by the users of infected machines.
- An email account password harvester. The stolen data is used to send out mass spam mailings with malicious attachments.
- A module that harvests social service account data. This data can be used to spread links to resources that were previously infected.
- A SOCKS server. This is used to anonymously connect to victim computers via VNC during transactions.
- A RemoteShell. This module is capable of performing remote cmd.exe commands.
The weeks prior to the Christmas and New Year holidays are traditionally a period of high malicious user activity. As early as November, Kaspersky Lab noted instances where posts were made in hacker forums about buying and selling databases to access bank accounts and other documents used to open and manage the accounts to which stolen funds are sent. We can expect to see mass Neverquest attacks towards the end of the year, which could ultimately lead to more users becoming the victims of online cash theft.
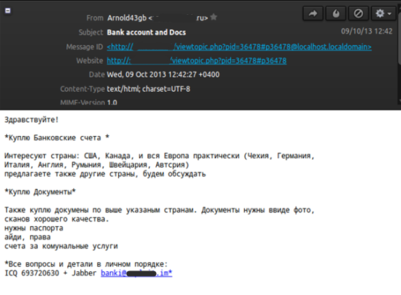
A post on a hacker forum about buying and selling databases of information used to access bank accounts and documents
On a final note, it should be said that after wrapping up several criminal cases associated with the creation and proliferation of malware used to steal bank website data, a few “holes” appeared on the black market. New malicious users are trying to fill these with new technologies and ideas. Neverquest is just one of the threats aiming to take over the leading positions previously held by programs like ZeuS and Carberp.
Protection against threats such as Neverquest requires more than just standard antivirus; users need a dedicated solution that secures transactions. In particular, the solution must be able to control a running browser process and prevent any manipulation by other applications.
Online Banking Faces a New Threat






















eileen
thank you for all this info it really tells us what is safe and what to do to stay safe/