
Last week, Kaspersky Lab identified a mass mailing of phishing letters sent in the name of leading IT security providers. The messages we detected used the product and service names belonging to Kaspersky Lab, McAfee, ESET NOD32 and many others.
The text and general layout of each letter followed the same template; only the senders’ names and the IT security solutions mentioned in the text were different. In their messages, the cybercriminals invited the reader to install an important security update for his/her security solution to guarantee protection against a new piece of malware supposedly ravaging the web. To do so, the user simply needed to open the attached ZIP archive and launch the executable file in it. Not surprisingly, the writers urged their victims to act immediately rather than spend time thinking about who might be behind this sudden urgent letter.
However, even the name of the attached file should have set alarm bells ringing for the user: too many numbers, meaning it was obviously generated in an arbitrary manner.
As a matter of fact, there is a malicious program in the attached archive, detected by Kaspersky Lab’s products as Trojan-Spy.Win32.Zbot.qsjm. This Trojan belongs to the renowned Zeus/Zbot family, and is designed to steal confidential user information, preferably banking and financial data. Using this malware, cybercriminals can modify the contents of banking sites by planting malicious scripts in them to steal authentication data such as login credentials and security codes. To these endsTrojan-Spy.Win32.Zbot.qsjm can also take screenshots and even capture video, intercept keyboard input, etc. In addition, this Trojan is notable in that it does not access a pre-determined C&C to receive commands and a configuration file, but rather uses a P2P protocol to receive this data from other infected computers.
Here are some more examples of messages containing malicious attachments, all taken from the mailing lists that we discovered:
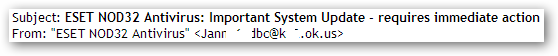
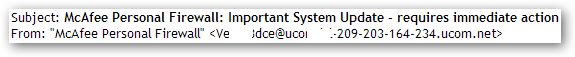
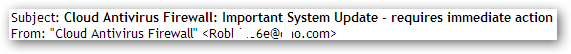
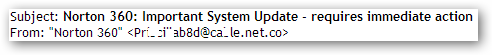
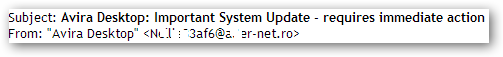
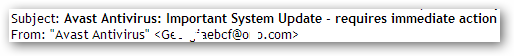
The subject lines of these messages follow the same template with the cybercriminals just changing the names of the security products in them. The messages are sent from real users’ mailboxes that were apparently hijacked after their computers were infected with the malicious program and became part of a botnet.
Following this incident we would like to remind readers that no reputable IT security manufacturer would send security updates for its product in a zipped attachment to an email address. Moreover, we don’t recommend opening any file attached to an email unless you are expecting it and know who the sender is.

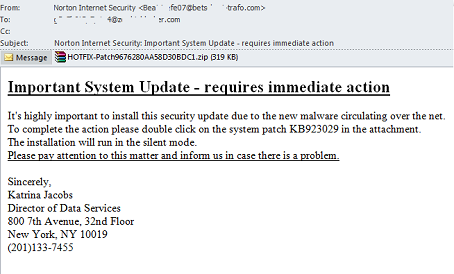



















ZeuS – now packed as an antivirus update