
Today, I received this message from a friend living in Mexico via Whatsapp.
According to the message, Starbucks is giving away 500 in local currency credits if you take their survey, so my friend asked me to take a quick look to determine if it’s real.
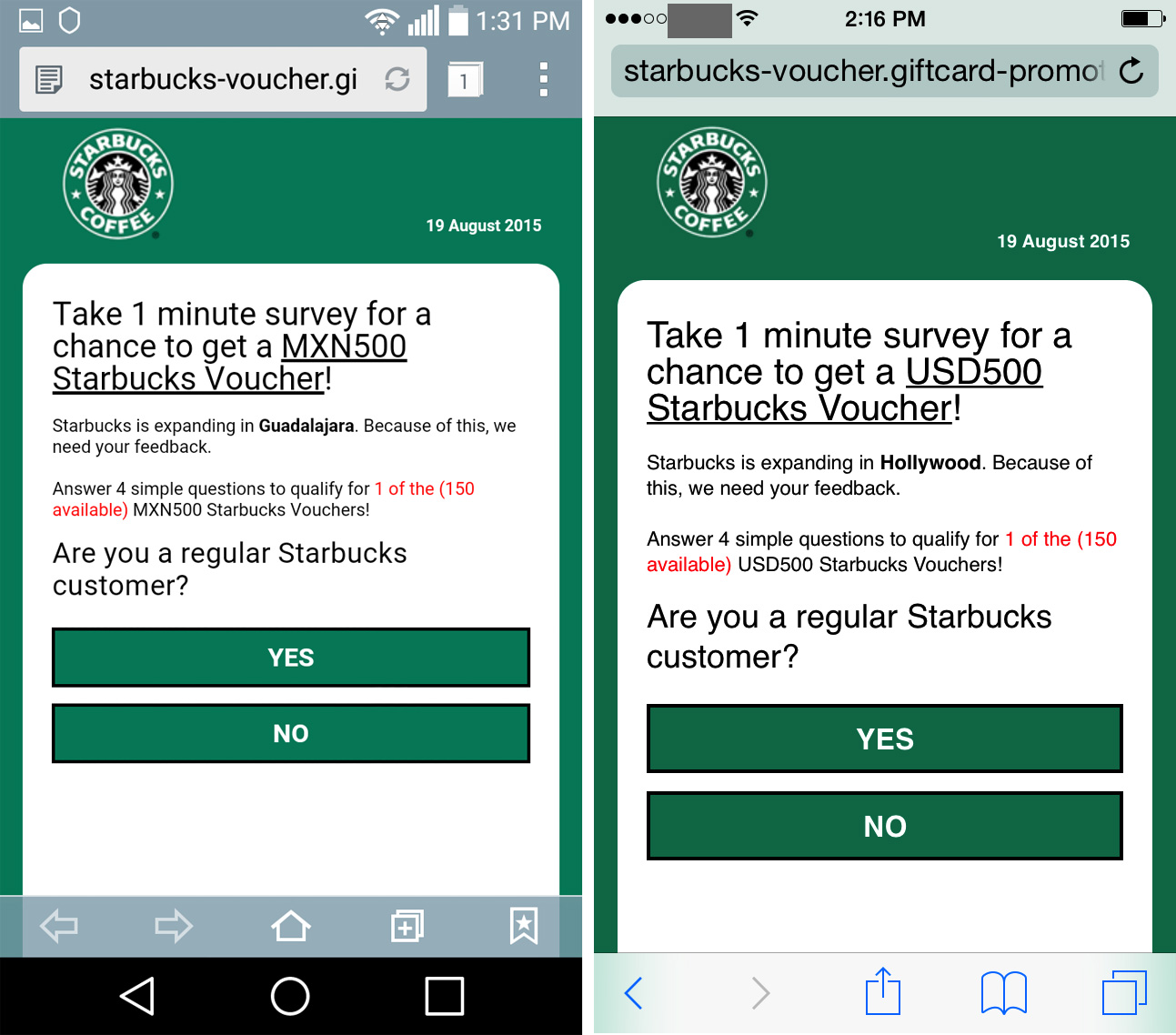
Sadly for the coffee lovers among us, this is a classic hoax campaign abusing the Starbucks brand. If the victim follows the link from a mobile device, it loads a fake Starbucks survey with some scripts designed to customize the campaign according to the city of origin and its local currency.
So if you live in the U.S. you’re promised $500 USD but if you’re in Argentina then it’s only 500 pesos and so on. Argentinians are clearly getting the worse end of that deal.
If you have the patience to click through the survey, the scammers have the gall to ask you to spread the message to 10 of your contacts in order to redeem your imaginary voucher. This is how this Hoax is spread –by enlisting the help of gullible victims to prey on their friends!
What if the victim uses a desktop browser? There is a script on the aforementioned site, which is actually located in Moldova, that detects the browser’s user agent. If it matches with a desktop version, the script redirects the visitor to the following URL:
hxxp://dpgoo.[***].com/258769f2-6910-4d0b-9db1-4d386c60c9d7
That URL in turn redirects visitors to another website for a Fake (Rogue) Technical Support service meant to scare the victim into providing remote access to their system.
It turns out that Google Hangouts calls to that number are prohibited. My first calling attempt met an automated answer of ‘This number is not in service’. However, on a second attempt with an alternate line I was able to connect to somebody with a foreign accent.
If you’re so inclined, you can listen to just how nice and attentive the ‘support staff’ is. Note the pauses and emotional inflection behind each scripted scene like ‘My name is…’ and when I revealed that my computer is infected: https://clyp.it/v2gjp3jq
As you can see, this is an all around ‘Hoax-Fraud-Rogue’ scheme with redundancies and low chance of failure. Victims themselves are enlisted to rekindle the campaigns flames by spreading the message to 10 new users. So, first things first, it’s very important to break the cycle, stop bombarding your friends with scams! Next, invite them to have a conversation about how hoaxes work, maybe over a cup of coffee you’ll actually have to pay for.
You’re Paying for Your Starbucks, One Way or the Other
























alberto
Hi, I found this site after having seen it personally and on FB, and finding a reference to this post form many Spanish-speaking news sites, which most of them, totally unprofessionally, don’t even link to the post, so I had to google the soure.
A couple of comments. This post is not clear on what to do, or if you even are infected, which is the first question most people are making on the FB posts warning about this. I think it’s pretty safe to say the phone is not being infected even if you complete the survey.
However, at the end of the survey they ask for name and email. It’d maybe be prudent to alert your readers to expect emails with links to the scareware/rougue site, even bypassing their spam filters.