
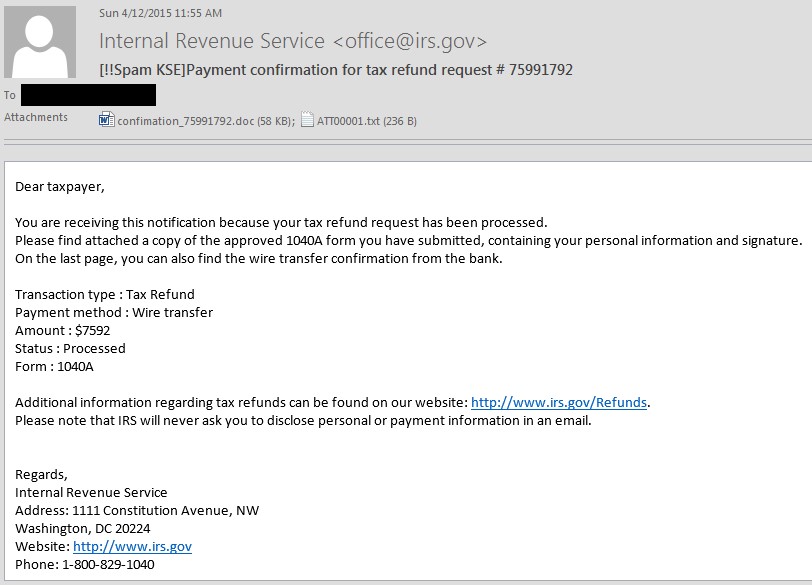
Last-minute tax declarations lead to IRS-themed Ransomware
Oh, how procrastination gets all of us! April 15th is the U.S. tax deadline and it looks like most of us will be coming down to the wire on declaring our taxes and holding our collective breath in expectation of that sweet, sweet refund. Sadly, our malware writing friends are aware of this and their discipline has proven far superior. Knowing that many are on the lookout for emails from the Internal Revenue Service concerning pending refunds, criminals have crafted some of their own:
The attachment is actually a Trojan-Downloader.MsWord.Agent malware, built by the same group behind the recent LogMeIn malicious campaign described here.
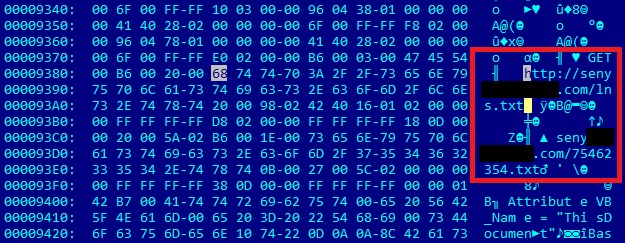
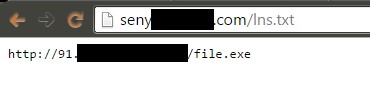
The infection scheme is very similar to the aforementioned, however, the threat actor has moved on from abusing Pastebin entries and has instead hacked a Web server in China to host the instructions script file. This file as well as the download URL are also encoded in Base64 and the resulting payload is actually ransomware.
URLs embedded in the malicious macros leading to a Base64 encoded instructions script file and the payload URL below
Instructions files with the URL to the ransomware payload
The malicious ransomware payload is detected by Kaspersky Anti-Virus as Trojan-Ransom.Win32.Foreign.mfbg
Due to the reliance on the IRS branding, this particular malicious campaign is mostly focused on US citizens and permanent residents of the USA.
Your Tax Refund with a Data Kidnapping Twist!





















Don Moore
Hello Dmitry.. I know you were trying to protect information in this article from getting out (by blocking out part of a URL in the code dump screen in your article). I want to let you know that I was able to decode it anyway because the hex code was still readable. Don’t worry sir – I will not use the information – I am just letting you know. There are still ‘old school-ers’ out there that still know a thing or two about deciphering what looks to others to be gibberish.
Regards.
Don