
While ransomware is a global threat, every now and then we see a variant that targets one specific region. For example, the Coinvault malware had many infections in the Netherlands, because the authors posted malicious software on Usenet and Dutch people are particular fond of downloading things over Usenet. Another example is the recent Shade campaign, which targets mostly Russia and CIS.
Today we can add a new one to the list: Wildfire.
Infection vector
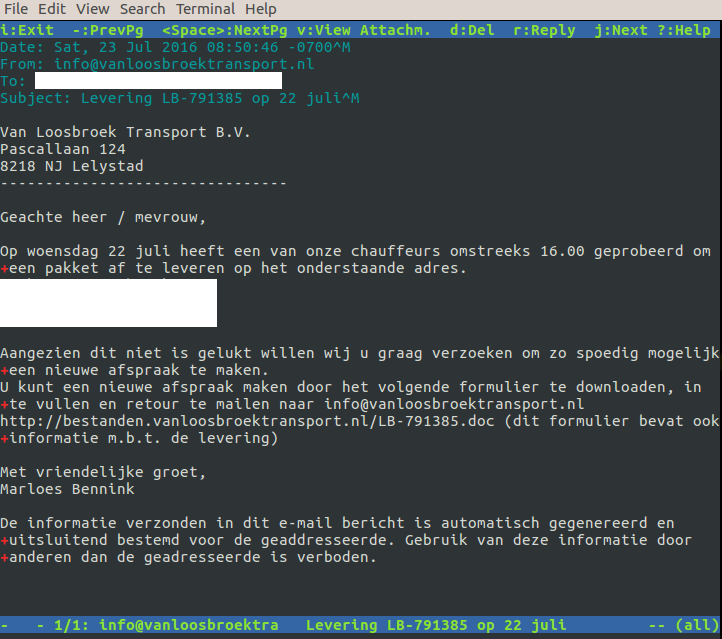
Wildfire spreads through well-crafted spam e-mails. A typical spam e-mail mentions that a transport company failed to deliver a package. In order to schedule a new delivery the receiver is asked to make a new appointment, for which a form has to be filled in, which has to be downloaded from the website of the transport company.
Three things stand out here. First, the attackers registered a Dutch domain name, something we do not see very often. Second, the e-mail is written in flawless Dutch. And thirdly, they actually put the address of the targeted company in the e-mail. This is something we do not see very often and makes it for the average user difficult to see that this is not a benign e-mail.
However, when we look at who registered the domain name, we immediately see that something is suspicious:
The registration date (registered a few days before the spam campaign started), as well as the administrative contact person seem to be very suspicious.
The Word document
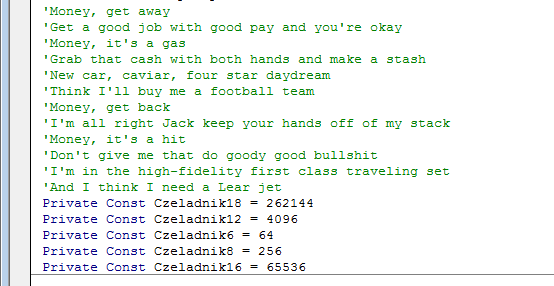
After the user downloaded and opened the Word document, the following screen is shown:
Apparently the document has some macros, containing pieces of English text, which clearly show the intent of the attackers (actually it is the lyrics of the famous Pink Floyd song Money), but also has several variables in the Polish language.
The ransomware itself
The macros download and execute the actual Wildfire ransomware which consists in the case we analyzed of the following three files:
- Usiyykssl.exe;
- Ymkwhrrxoeo.png;
- Iesvxamvenagxehdoj.xml
The exe file is an obfuscated .net executable that depends on the other two files. This is exactly similar to the Zyklon ransomware that also consists of three files. Another similarity is that, according to some sources (http://www.bleepingcomputer.com/forums/t/611342/zyklon-locker-gnl-help-topic-locked-and-unlock-files-instructionshtml/, http://www.bleepingcomputer.com/forums/t/618641/wildfire-locker-help-topic-how-to-unlock-files-readme-6de99ef7c7-wflx/), Wildfire, GNLocker and Zyklon mainly target the Netherlands. In addition, the ransom notes of Wildfire and Zyklon look quite similar. Also note that Wildfire and Zyklon increase the amount you have to pay three-fold if you don’t pay within the specified amount of time.
Anyway, back to Wildfire. The binary is obfuscated, meaning that when there is no deobfuscator available reversing and analyzing it can take a lot of time. Therefore we decided to run it and see what happens. Just as we hoped, this made things a bit easier, because after a while Usiyykssl.exe launched Regasm.exe, and when we looked into the memory of Regasm.exe, we clearly saw that some malicious code had been injected into it.
Dumping it gave us the binary of the actual Wildfire malware. Unfortunately for us, this binary is also obfuscated, this time with Confuserex 0.6.0. Even though it is possible to deobfuscate binaries obfuscated with Confuserex, we decided to skip that for now. Why? Well it takes a bit of time, and because by working together with the police on this case, we had something much better in our hands: The botnetpanel code!
Inside the botnetpanel code
When you are infected with Wildfire, the malware calls home to the C2 server where information such as the IP, username, rid and country are stored. The botnetpanel then checks whether the country is one of the denylisted countries (Russia, Ukraine, Belarus, Latvia, Estonia and Moldova). It also checks whether the “rid” exists within a statically defined array (we therefore expect the rid to be an affiliate ID).
If the rid is not found, or you live in one of the denylisted countries, the malware terminates and you won’t get infected.
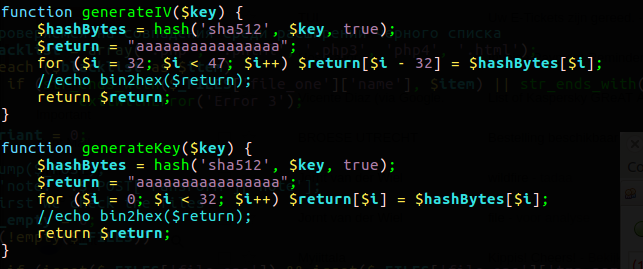
Each time the malware calls home, a new key is generated and added to the existing list of keys. The same victim can thus have multiple keys. Finally the botnetpanel returns the bitcoin address to which the victim should pay, and the cryptographic key with which the files on the victim’s computer are encrypted. We don’t quite understand why a victim can have multiple keys, especially since the victim only has one bitcoin address.
Also interesting is the encryption scheme. It uses AES in CBC mode but the key and the IV are both derived from the same key. This doesn’t add much security and defeats the sole purpose of having an IV in the first place.
Conclusion
Even though Wildfire is a local threat, it still shows that ransomware is effective and evolving. In less than a month we observed more than 5700 infections and 236 users paid a total amount of almost 70.000 euro . This is also due to the fact that the spam e-mails are getting better and better.
We therefore advise users to:
- Be very suspicious when opening e-mails;
- Don’t enable Word macro’s;
- Always keep your software up-to-date;
- Turn on Windows file extensions;
- Create offline backups (or online backups with unlimited revisions);
- Turn on the behavioral analyzer of your AV.
A decryption tool for Wildfire can be downloaded from the nomoreransom.org website.
P.S. the attackers agree with us on some points:






























Wildfire, the ransomware threat that takes Holland and Belgium hostage