
The biggest security news of the week is the leaked photos of many celebrities. Many people, especially the involved celebrities, wondered how such a hack could take place.
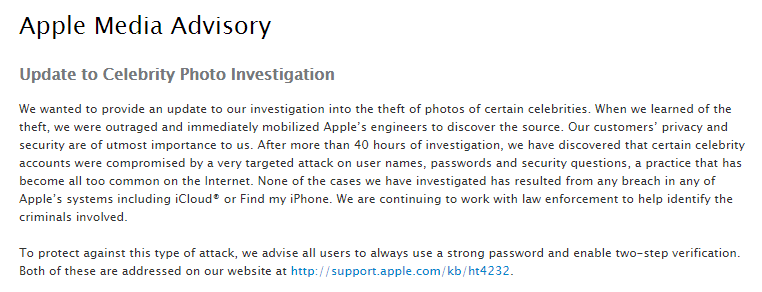
The initial statement by the attacker was that the iCloud was hacked. This prompted Apple into their we-do-not-really-comment-until-we-have-done-our-research mode. Today, they released a statement on the incident:
 https://www.apple.com/pr/library/2014/09/02Apple-Media-Advisory.html
https://www.apple.com/pr/library/2014/09/02Apple-Media-Advisory.html
For me the most interesting quote is: “accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet.”
Apple is thus well aware of the problems that arise with these forms of authentication. The more interesting is their advice: strong passwords and two-step-verification.
Strong passwords are, according to Apple, passwords with a minimum of 8 characters, with some additional requirements. Interesting enough they do not enforce of all their suggestions. A password such as “Password1” is acceptable, even though it can be easily guessed.
Their other advice, using two-factor-authentication is somewhat flawed. For instance, it does not protect your iCloud backups (see this post). Also, two-step-verification is not available in every country. If you use, for example, a Romanian or a Croatian telephone number, then bad luck. Considering that Google offers two factor authentication for such countries as well, one might wonder why Apple didn’t implement it as well. Could it be the cost of the SMSes?
So how to protect yourself properly? My colleague Alex Savitsky wrote an excellent article about this.
To summarize:
- Use strong and unique passwords that are easy to remember and hard to crack (for instance, a phrase in your native language with “spaces” in it, a number and a special char)
- If available in your country, enable two-factor authentication
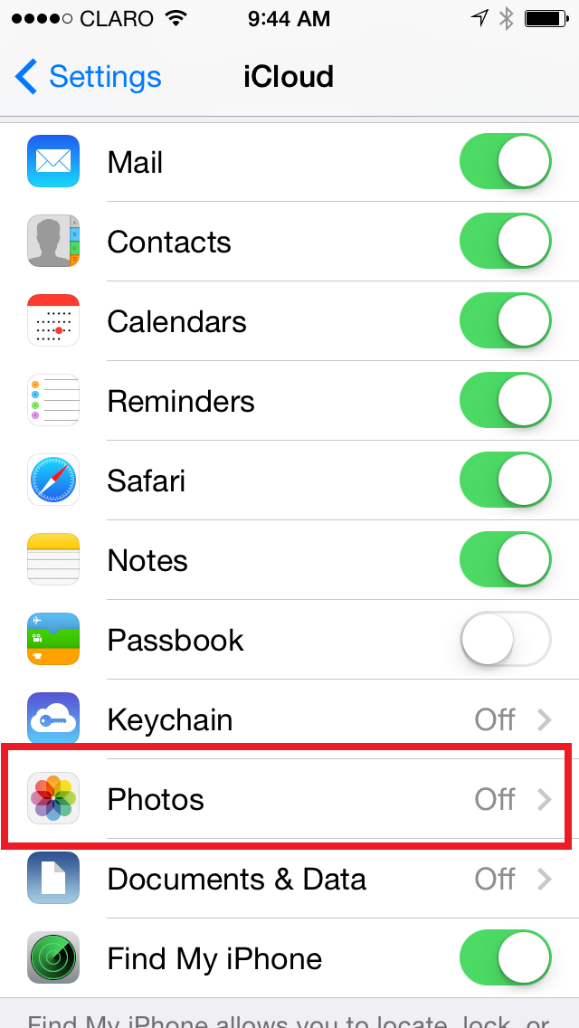
- iPhone users may want to disable iCloud photo Stream / photo Sharing. Additionally iPhone users may want to delete the backup of their photos / iPhone in the iCloud.
Photo courtesy of my colleague Dmitry Bestuzhev – https://twitter.com/dimitribest/status/506820178320322560
And remember – if you don’t want your private photos to get leaked, better not take them in the first place!
Protecting yourself against the celebrity iCloud hackers


















monika kadian
very knowledgeable……very helpful…..