
We recently went on tour with some journalists through Copenhagen, the capital of Denmark, and took a quick look at the state of WiFi networks in the city. Copenhagen lies on two islands (Zealand and Amager) and is well known for its culture and the design of the city (as well as being the 14th most expensive city in the world according to Forbes List). That is the kind of information you can find in any guidebook, but what you won’t find are statistics on wireless networks. So it seemed a good idea for us to take a look!
We decided to take three different routes to see if there would be any noticeable differences in terms of security. We decided not to examine the ratio of encrypted to unencrypted networks for one reason: nowadays, most unencrypted networks are hotspots offered by telecom service providers or hotels so they’re left unencrypted on purpose. The only reliable way to find out if an unencrypted network belongs to a private individual would be to connect to it – and that’s something we wouldn’t want to do for obvious reasons. So instead of spending time guessing if an unencrypted network is an official hotspot, we focused on secure encryption (WPA) vs. weak encryption (WEP).
Our first trip took us through the east of the city near the harbor, beginning near the Kronborg (a UNESCO World Heritage Site). We found about 1524 access points within 34 minutes – maybe not a lot, but considering that our car had to stop a couple of times, it’s not bad. 23% of networks used WEP, with the other 76% using WPA.
Our second tour was round and about the city center, where a lot of companies as well as middle class households are located. Within 10 minutes, 1055 access points were detected. As you can see, about 82% of all encrypted networks used WPA, which is a very high percentage compared with some of the war driving we’ve done in the past. But given that WEP is crackable within minutes, it would of course be better if 100% of wireless networks implemented WPA.
The third and last trip led us through a part of the city where the inhabitants are both older and also wealthier than the average Copenhagen resident. They’re also obviously less concerned about encryption since only 72% of all encrypted networks used WPA. Within 9 minutes we found 1022 access points; the highest concentration of access points out of the three trips we’d made.
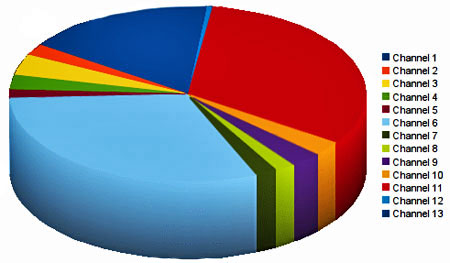
Finally, let’s take a look at the channels used by the WiFi networks: Channel 6 was the most popular, followed by Channel 11 and Channel 1. In most WLAN-Hardware Channels 6 and 11 are used by default, and it’s not really a surprise that most of the network owners hadn’t changed the default setting.
To summarize: we found 3127 encrypted networks, of which 23% used WEP and 77% WPA. The relatively high percentage of networks using WPA shows that Copenhagen overall is pretty security conscious. Even the “worst” result of 72% of networks with WPA is excellent compared to the 23% of networks using WPA which we detected in Santiago, Chile. It’ll be interesting to compare the Copenhagen results to those of other European cities which we haven’t researched yet. It seems to me I’ve got a good excuse to start booking some tickets!




















Wardriving in Copenhagen, Denmark