
Talk about non-Windows malware and most people automatically think of Linux, MaxOS X etc. etc. But this very modern attitude overlooks a couple of interesting stages in the history of computer virology.
Some of you might wonder what I’m getting at here. Well, at the beginning of this week, IT luminaries such as Steve Wozniak (the co-founder of Apple) and Jack Tramiel (former Technical Director at Commodore and later Head of Atari) got together to celebrate the 25th anniversary of the the Commodore 64.
What a lot of people don’t know – even these revered 8-bitters had computer viruses. Even though the Commodore used a Basic intepreter from Microsoft, the blame for these almost prehistoric bugs can’t be laid at the Redmond company’s door – back then, the majority of programs were written in pure assembler. In 1986, a hacking group – possibly the Bayrische Hacker Post group – developed the ‘BHP’ virus. It periodically caused the computer to cycle rapidly through all available sixteen colours on the display, showing the victim a message in German which said ‘HALLO FATTY, THIS IS A REAL VIRUS!’. The text was followed by a serial number, which increased by a count of one with every infection. BHP hooked a number of interrupts, included one normally called when a reset is carried out. This ensured that it would be able to survive a reset.
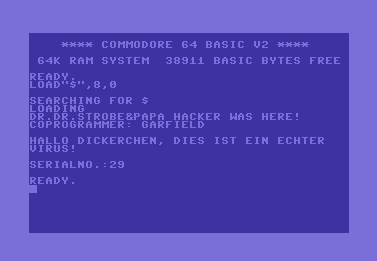
The nastiest C64 virus was “H.I.V”, which surfaced sometime in the middle of the 90s. It didn’t just make itself at home in RAM and on disks, but it also copied itself to the disk drive’s RAM (C64 disk drives had their own CPU and RAM on board). This meant that simply restarting the C64 wouldn’t be enough – the external disk drive also had to be restarted in order to wipe its RAM.
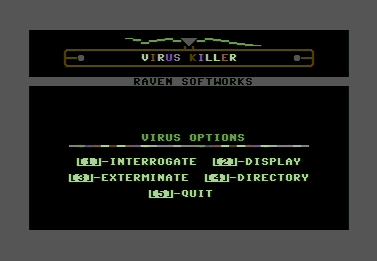
Although C64s were very popular in their time and disks were freely passed around the schoolyard (the precursor to today’s P2P networks), malware wasn’t ever a big problem – only 7 malicious programs in 25 years. There were disinfection utitilities, but given the very low incidence of malware for the C64, these were more of a curiosity than anything else. The advent of Commodore’s flagship product the Amiga changed all that. But that’s another story for another time – maybe we’ll cover it on the Amiga’s 25th birthday, in three years time.




















The C64 hits 25