
The FBI’s “Operation Ghost Click” announcement in Nov 2011, involving the Rove Digital botnet delayed cleanup efforts that we previously discussed, continues to haunt both the internet networks and the mass media. A Forbes article and a Times article yesterday brought the apparition back to the front, with some claiming that the site offered by the DNSChanger Working Group is a new one, which it is not. The 2011 Operation being described, and the temporarily outsourced DNS server replacements and delayed cleanup, is the same. This phantom is nothing supernatural, so why all the discussion? The federal judge’s extension allowing the Fbi to run these replacement DNS servers still cuts off access in early July. When those replacement servers are removed in early July, the infected systems resolving DNS queries at these previously-owned Rove Digital servers will simply not be able to resolve DNS requests. July 9th will arrive soon, and notifications continue to go out related to the hundreds of thousands of systems in the US alone that are still infected.
In the simplest terms, connectivity will not be severed for DNSChanger-infected systems, but internet communications will not function for infected systems that have not been cleaned up. In the US, government agencies, home users, and other organizations still infected with the malware will have systems that effectively can’t get online, can’t send email, etc. It will look like they are connected to their network, but they just won’t communicate with anything.
At the same time, there seems to be issues with some existing identification efforts. Yesterday, I infected a system with DNSChanger and visited dns-ok.us. Results here:
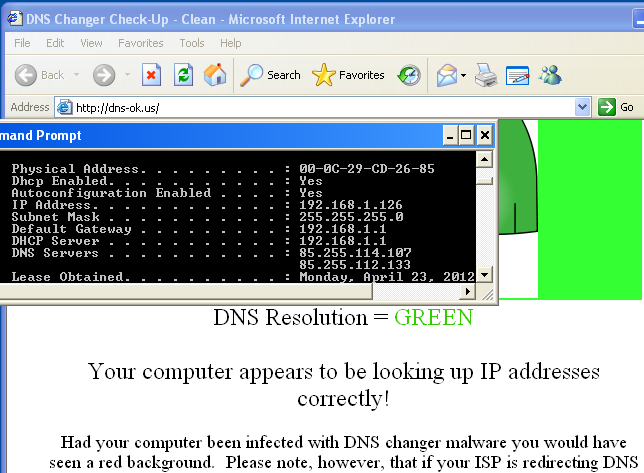
Regarding the dns-ok site visit, my ISP’s support team isn’t aware of any “DNS redirections” that would cause the test to fail, and I will update this post with any update from our network admin that they are redirecting my system’s dns queries. But that piece is highly doubtful. My point here is that infected system owners may be confused by this check. And the ip address was within the Fbi-provided ranges run by Rove Digital – perhaps a reader knows differently?
UPDATE (1:40 p.m. MST) – I received some details from my local ISP network admin. They are not redirecting any related DNS queries. However, one of their large upstream providers is redirecting DNS requests to another DNS server of their own. The other upstream link to the net does not seem to be re-routing DNS requests. So my infected client’s traffic must be favoring routes through the larger upstream provider, and poof, the green/clean response banner appears. Any way you look at it, the response from the site can be inconsistent – sometimes red, sometimes green. Unfortunately, this sort of situation is going to confuse cleanup efforts. So, here we are again. To the potentially millions of folks running DNSChanger infected systems and are listening to the cacophony of incident responder consultants tossing out cheap cynicism that “AV is dead!”, go ahead to http://www.dcwg.org/fix/ and download an “AV product” to scan your system. Of course, I like recommending our scanners (just visit http://www.kaspersky.com) because I have cleaned up DNSChanger infected systems with it (and the products have fully functional trial periods), along with our TDSSKiller rootkit removal tool to clean up especially complex DNSChanger infections.





















Update to “DNSChanger – Cleaning Up 4 Million Infected Hosts”