
Malware using the .CPL extension is nothing new for us, but it’s still interesting that almost all the banking malware currently originating in Brazil is distributed in this format. It doesn’t matter whether it’s a drive-by download or a simple attack based on social engineering, users find themselves at the epicenter of a real CPL storm every day. We decided to look into this trend and find out why Brazilian cybercriminals now favor this approach.
CPL files are applets used in Windows Control Panel. Once executed, rundll32.exe is used to launch a wide variety of actions defined in DLLs. Among the many things it can do is invoking Control Panel applets. When Windows first loads a Control Panel item, it retrieves the address of the CPlApplet() function and subsequently uses that address to call the function and pass messages to it.
Each cybercriminal has a preferred modus operandi to distribute this kind of malware. Most of them like to put the CPL file inside a ZIP, but we have also found it inserted inside RTF files. This kind of malware belongs to the Trojan-Banker.Win32.ChePro family, first detected in Russia in October 2012.
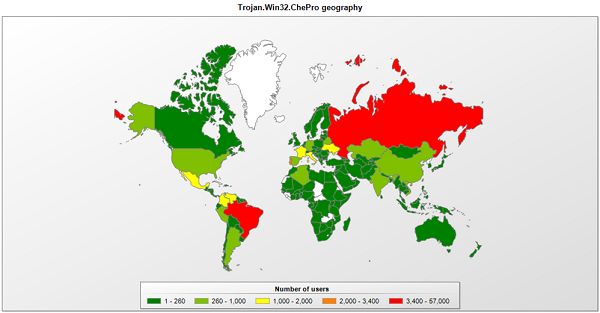
Since the beginning of the year we’ve had a lot of ChePro detections in Brazil:
Checking for the most infected countries we found Brazil and Portugal together (because they share the same language). But it was a surprise to see Russia up there with them. This is a sign that Brazilian bad guys are cooperating and using techniques developed by their Russian counterparts, quickly adapting it for their new banking Trojans.
The files of this family have some common characteristics:
- all the files have *.CPL extensions
- files are a DLL image
- most of the timestamps are 808992537 or 1362009600
- linker major version is 2
- linker minor version is 25
- 80 bytes in the last page
- 2 pages in each file
- exports the CPlApplet() function
- coff file characteristics is 0xa18e
- initial sp value is 0xb8
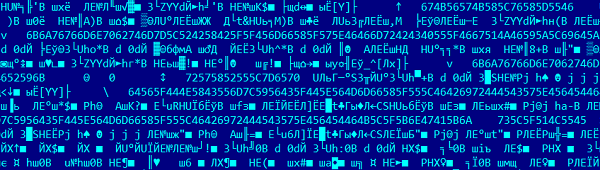
The first samples were packed with pecompact and used such string encryption:
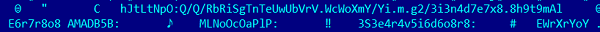
The next generation was packed with UPX and used a different kind of string encryption, adding random symbols between the meaningful ones:
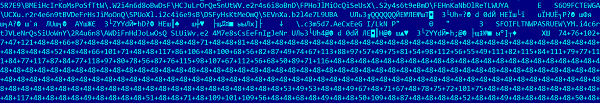
They also used base64 for big blocks:
Why did the bad guys decide to use this extension? There are several reasons, starting with the fact that end users are often unaware of any dangers associated with these files. Some webmail filters are not set up to block it, even when it’s attached to a zip file in an e-mail message. But the main reason is to bypass AV detection since they can apply several layers of encryption inside the same file.
Most ChePro samples are downloaders which need other files to complete the infection, most of the time installing banking malware that will take screenshots, capture keyboard strokes and reads the content of the clipboard, enabling the malware to attack virtually any internet banking service. Here we saw some innovations as the crooks tried to avoid detection for as long as possible. Several Trojans usegeo localization or queries system for timezone and Windows version; the trojans will not attempt to complete an infection outside of a Brazilian IP or in a Windows running in different timezone from Brazil or a language that is not Portuguese. Other Trojans also download a non-executable file such as an .xml which is later split up into separate files belonging to the infection:
We have created several heuristic and generic detections for these ChePro Trojans.
Thanks for my colleagues Dmitry Bestuzhev and Santiago Pontiroli for the collaboration and Fernando Mercês for very useful info.























Trojan ChePro, the CPL Storm