New trick from cybercriminals of Brazil – a suspicious message arrives to the user with a file attached named “Comprovante_Internet_Banking.rtf”, translated from Portuguese it means “Receipt from Internet Banking”:
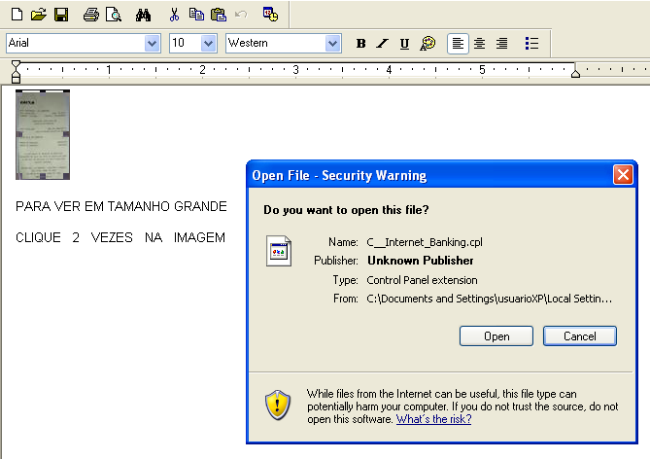
If the user were to open the file it would be presented with the image of a bank receipt and the invitation to double click on it (the text below says “Click to see in a larger size”, “To display the banking receipt click twice in the image”)
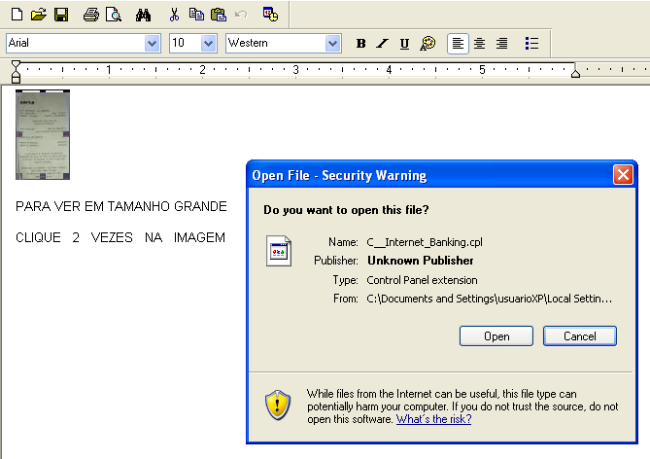
When clicking on the embedded object the the user will be asked to execute it starting the infection process by running a CPL file
The .RTF file format and some text editors allow the insertion of file objects inside documents, interestingly even an executable file can be embedded:
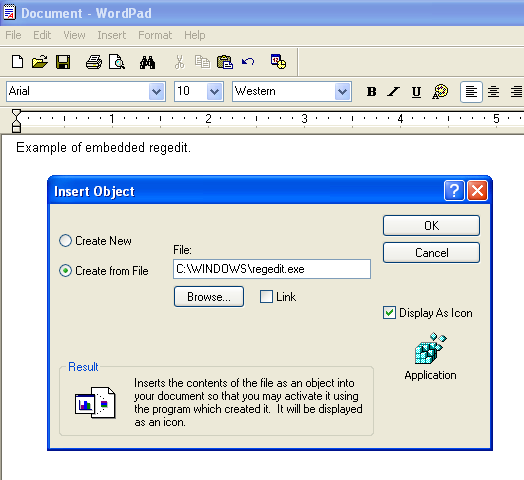
The .RTF file has 2 blocks of binary data:
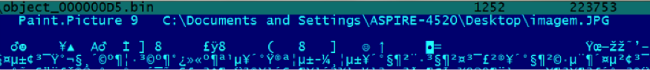
object size 223753 at index 000000D5
object size 15744 at index 00070215
One of them which reveals the path used by the bad guy to create the image, revealing ownership of an Acer Aspire-4520 computer:
The .CPL file (MD5: 563707b4edcc0bb0c88365a6702d4ba0) embedded into the RTF file is a well-known Brazilian Trojan banker, written in Delphi, belonging to the family Trojan.Win32.ChePro – after executed it drops several files through the system to keep the infection running. Embedding malicious files into RTF or DOC files allows cybercriminals to bypass e-mail filtering by extensions or type; also it allows them to break the AV detection by signatures.
We are sure that we’ll see this technique being exploited in Brazil more times from now on.





















Brazilian Bankers Gone Wild: Now Using Malicious Office Files