
Geocities.com has been gone for a month now, and you’d have thought the spammers would be missing it. But one of the messages we got today shows that on the contrary, the spammers are looking forward to the future.
Here’s the message we got today – with tomorrow’s date on it. As most people configure their mail client to sort incoming messages by date, putting a future date on an email will ensure maximum visibility by putting it right at the top of the inbox.
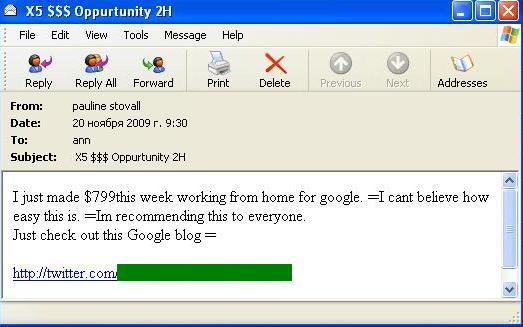
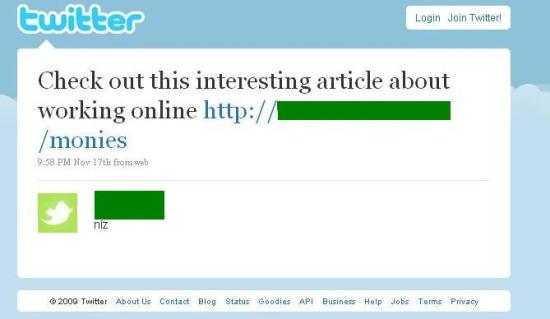
The links in these messages lead to new Twitter accounts:
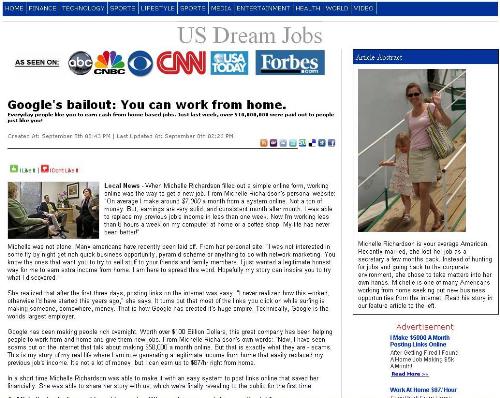
Which in turn link to a site looking very like a news portal. But the only working links here reference making money by working from home.
The account shown above also has tweets with links to typical Viagra and weight loss sites. It’s clear that spammers may be moving with the times by changing the tools they use, but they haven’t changed their message. And why should they, as long as there’s profit to be made?





















Tomorrow’s spam – today