
We’ve just been contacted by a user who let us know that www.adoronin.ru has been infected with Trojan-Downloader.JS.Agent.bx. This Russian site can be used to book tickets for theatres, concerts, musicals, the circus and sporting events on-line. As there’s a lot of interest in the theatre and sports over here, the site gets pretty busy – a smart choice for a malicious user to infect a lot of systems.
So how did our user realize the site was infected? He clicked on an banner leading to the site. The banner was placed on mail.ru, which is one of Russia’s biggest Internet portals with more than 3 million users. But then his antivirus started to react, as he put it, “strangely”. It clearly showed him that the page he was trying to access was infected. It didn’t show the adoronin address though, but an entirely different address. It was clear that code had been injected into the main page of the adoronin site – code that would then download Trojan-Downloader.JS.Agent.bx to the user’s machine.
The Web Anti-virus component of Kaspersky Anti-Virus 6.0 detected the malicious activity and asked the user if he wanted to block it. This prevented his machine from being infected. And it gave us and the site administrator a heads-up – working with us, he was able to clean his site.

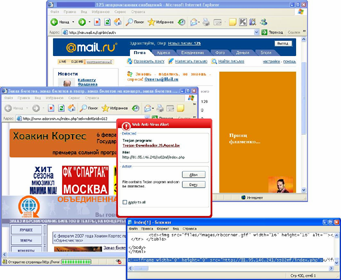

















Ticket site infected by Trojan-Downloader