
What are secure connections?
Secure connections are designed to protect data sent between two computers via the Internet. Secure connections should:
- Mask confidential data from third parties
- Verify the identification of the party with whom information is being exchanged
- Protect information from being viewed or modified by a third party
There are several ways to secure data transmission, and they all involve the use of data encryption and special keys used to read the information. The keys (also known as certificates) are usually stored in a dedicated database – a certificate archive – and are accessible to authorized users.
- Data encryption. This method involves masking information (emails, for example) from third parties and sender verification. This method, however, does not verify the authenticity of the two computers involved in the exchange of information. In order to create an encrypted message and have two recipients read it, the recipients must have the appropriate program installed (such as PGP, GPG or S/MIME). Most encrypted data is transferred via email.
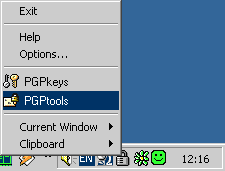
Fig. 2. Encrypting data using PGP
- Encrypting a transfer channel. This method involves concealing the entire contents of the network connection and verifying the authenticity of all computers participating in the network connection. However in most cases, the data itself, as opposed to the first method, is not verified. For example, sender verification of an email received via an encrypted channel is not possible. These encryption protocols are called SSL and TLS.
Support for an encrypted transfer channel is currently provided by the vast majority of Internet applications: email servers and client programs, web servers and browsers, as well as a number of proprietary network applications, such as banking systems used to manage accounts and make payments online. The simplicity of this method is obvious to developers: a standard data transfer protocol can be implemented within an established secure network connection, making any necessary modifications to network ready applications minor. This is how well-known protocols function:
- HTTPS (normally HTTP – the main Internet protocol which is encrypted using SSL/TLS)
- POPS (normally POP3 –the main protocol for receiving email, and encrypted using SSL/TLS)
- SMPTPS (normally SMTP – the main protocol for sending email, and encrypted using SSL/TLS)
- MAPS (normally IMAP4 – a common protocol for receiving email, and encrypted using SSL/TLS)
- NNTPS (normally NNTP – a common protocol for reading news and encrypted using SSL/TLS)
Some network services are offered exclusively via an encrypted connection, such as the popular Gmail.
This article examines encrypted transfer channels, or so-called secure connections.
Different types of protection against network threats
Network connections are used to transmit both useful information but also malicious data, which can pose a threat to computers. Typical examples of malicious data include most contemporary threats: hacker attacks, Trojans, email worms and exploits which target web application vulnerabilities.
The following types of programs and application packages can be used to protect against network traffic threats:
- Firewalls
- Checks every network connection on the local computer in accordance with designated rules: the connection will either be permitted or denied.
- Can detect (but not delete) Trojans when they attempt to transmit harvested confidential data to a third party.
- Cannot detect viruses, regardless of the type of connection.
- Protection against network attacks (IDS: Intrusion detection system):
- Scans for, and is capable of blocking attacks for which there is a signature with in an established network connection regardless of protocol;
- Can detect viruses, but not delete them from common HDLC protocols such as HTTP and POP3. When a virus is detected in an email received via POP3, the only possible action is to terminate the network connection. This does not guarantee, among other things, protection against the virus detected in the email. When the user attempts to get other emails from the server, the infected email will cause the victim machine to disconnect from the mail server;
- Cannot detect viruses within an encrypted connection.
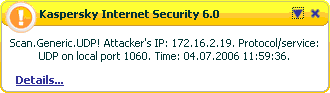
Fig. 5. Blocking a network attack
- Antivirus solutions (email and web):
- Can detect and neutralize viruses included in the database during sending and receiving data via a known HDLC protocol.
- Cannot detect viruses within an encrypted connection.
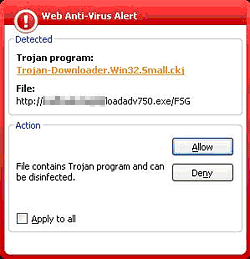
Fig. 6. Detecting a virus in a downloaded file
The danger of secure connections
As stated above, both useful and malicious information can be transmitted via network connections. Standard solutions protect computers against threats present in standard network connections, but aren’t able to counter threats present in secure connections. Verifying the contents of a secure connection is impossible by virtue of its secure nature, as demonstrated by the different types of protection listed above. As a result, malicious data within secure channels can cause a significant amount of damage, and sometimes more than if it were to be transmitted via a standard, non-secure connection.
The fact that it’s easy to encrypt a network channel and the fact that in most cases there will be no verification of who created the file results in a contradictory situation: a “secure connection” to a server provides the user with a feeling of security, but does not guarantee that the connection will be free from malicious data.
The dangers inherent in “secure connections” are particularly apparent now as such threats are becoming more and more widespread. After developers ensured SSL/TLS support for all popular web applications, a number of servers on the Internet began to offer their services via SSL/ TLS: together with major banking sites, all the big-name email services and partner sites opened access exclusively via secure connection. The qualifications of administrators of such servers is often barely enough for them to configure a secure server connection correctly.
The situation is exacerbated by the fact that an attack on a computer can be carried out remotely – for example, by simply placing a malicious file on a server which can be reached only via a secure connection.
A few examples can be found below.
Gmail and viruses
The popular email service Gmail offers access to its services exclusively via secure connection. It is known that Gmail servers use an antivirus program. Now let’s consider some hypothetical situations:
- A virus writer sends his virus to a Gmail subscriber.
- Gmail’s antivirus doesn’t detect the virus, because the antivirus database update has been delayed.
- After a certain time the user downloads the infected email from a local computer, because the Gmail antivirus has been optimized, resulting in emails being scanned only once they reach the inbox, and not when they are transmitted to the user.
- The antivirus program on the local computer, which has already updated its database to include the relevant signature, does not detect the virus since the network connection was encrypted in line with Gmail requirements, and the email antivirus was not able to scan the email.
- The file antivirus detects the virus in the email database and indicates that the entire email database should be deleted, since it is often impossible to disinfect an email database.
- Result: the user will lose all his correspondence.
Web servers and viruses
An equally interesting example: a malicious user can upload a malicious file to a web server and then attract Internet users to visit that server. If the virus is placed on a regular HTTP server, a computer with antivirus software will not be in any danger. However if the virus is placed on an HTTPS server the situation is a little more complicated:
- A virus writer can use a vulnerability to access files stored on a server (e.g. the case of the Valuehost servers, run by a Russian provider) and can replace files with the virus.
- A user opens a familiar website with a standard browser using HTTPS. The web antivirus cannot read the data in the encrypted connection and cannot prevent infected files from being downloaded.
- Instead of a normal web page, the browser loads a virus which exploits a browser vulnerability. The virus will instantly execute its code within the browser. The file antivirus cannot block the execution of the malicious code, because the infected file is processed by the file antivirus only after it has been saved to disk i.e. in this case after the malicious code has been executed.
- Result: the computer is infected.
Solutions
In order to check data transferred via a secure connection, most antivirus developers offer plug-ins for web applications. This approach has its pluses and its minuses:
- Pluses:
- The data stream between client and server is not affected
- The data stream cannot be accessed by third parties
- Minuses:
- It’s impossible to create a plug-in for certain applications. One key example: Outlook Express, the most common email program.
- There are limitations on using plug-ins, for example MS Outlook.
An alternative to using plug-ins is checking traffic using a man-in-the-middle method, which overcomes the negative aspects of plug-in architecture. Although it does have its drawbacks, antivirus vendors have been forced to implement this approach in order to protect their users.
This method is an attack on the essence of SSL/TLS, since it intercepts the secure connection, substitutes the original certificate and establishes two secure connections: between the application and the proxy antivirus, and again between the proxy antivirus and the remote computer.

Fig. 8. A standard secure connection
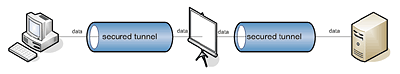
Fig. 9. A secure connection being scanned
- Pros:
- Connections can be scanned for any client application.
- Connection can be scanned for viruses under any known protocol.
- In addition to antivirus scanning, the proxy can conduct all other data operations, scanning for phishing, spam, etc.
- The data stream cannot be viewed by a third party unless s/he conducts a man-in-the-middle attack.
- Cons:
- The data stream between client and server is modified. As a result:
- Web applications cannot verify the authenticity of a server;
- A server cannot verify the authenticity of a client;
- If the proxy does not carry out its own verification, a second man-in-the-middle attack (between proxy and server) could be conducted. This could be done by a malicious user in order to read and modify data.
- The data stream between client and server is modified. As a result:
In practice, traffic scanning does not present any real danger to the user. Scanning is conducted on the local machine; the user can be asked to make choices, and all remote certificates can be verified by antivirus software and certificate archives, just as is done by web applications.
The drawbacks of the man-in-the-middle method are more than compensated for. The computer will be totally protection against threats on all types of network connections.
Kaspersky Internet Security
Kaspersky Internet Security includes solutions that verify both types of secured connections:
- Plug-ins for web applications:
- MS Outlook,
- TheBat,
- IE ScriptChecker
- Verification of secured connections in traffic using man-in-the-middle method:
- Kaspersky Internet Security informs the user of all actions:
- Notifies the user about server certificate substitutions
- Verifies certificates received from a server in the Windows certificate archives in exactly the same way as web applications
- The final stage of the man-in-the-middle method is not included. Registering a substitute certificate in the archives of trusted certificates has to be conducted by the user
- Kaspersky Internet Security provides the option to disable the checking of certain connections (configuration options: applications / servers / ports.) This solves any questions which could arise about the correct functioning of services which check the authenticity of the client.
- Kaspersky Internet Security checks all possible parameters within secure connections:
- The web antivirus component detects viruses in browser traffic
- The email antivirus component detects viruses in email traffic
- The anti-phishing component detects fake websites and links to these sites
- The antibanner component blocks pop-ups
- The antispam component blocks unwanted correspondence
- Kaspersky Internet Security informs the user of all actions:
Conclusion
Secure connections are designed to protect data against modification and theft. However, today, secure connections do not provide real protection against network attacks, and are therefore not as secure as they may seem.
Interestingly, the term secure connection may mislead users by creating a false sense of security. The situation is further exacerbated by the fact that standard security solutions cannot perform within secure channels.
Special methods have to be used in order to provide total protection against network threats. The simplest and most obvious solution is to use a plug-in for web browsers. Unfortunately, plug-ins are not universal, and many applications do not support them or impose too many restrictions on their functionality. Another solution found by antivirus manufacturers involves traffic verification.
The dangers of secure connections should not be underestimated. When you make important decisions about your computer’s security, make sure that your antivirus solution provides real protection against all network threats.




















Secure connections: how secure are they?